Research Blog
Welcome to our cybersecurity research blog where we uncover how malicious actors exploit weaknesses in systems, while going beyond the technical aspects and examining real-world perspectives across various industries.
Here you’ll find extensive research and insight from the well-known Horizon3.ai attack team, intuitive perspectives on everything security, and real-world attack path short stories that come directly from discoveries made by NodeZero.
Filters
Showing 103–108 of 161 results
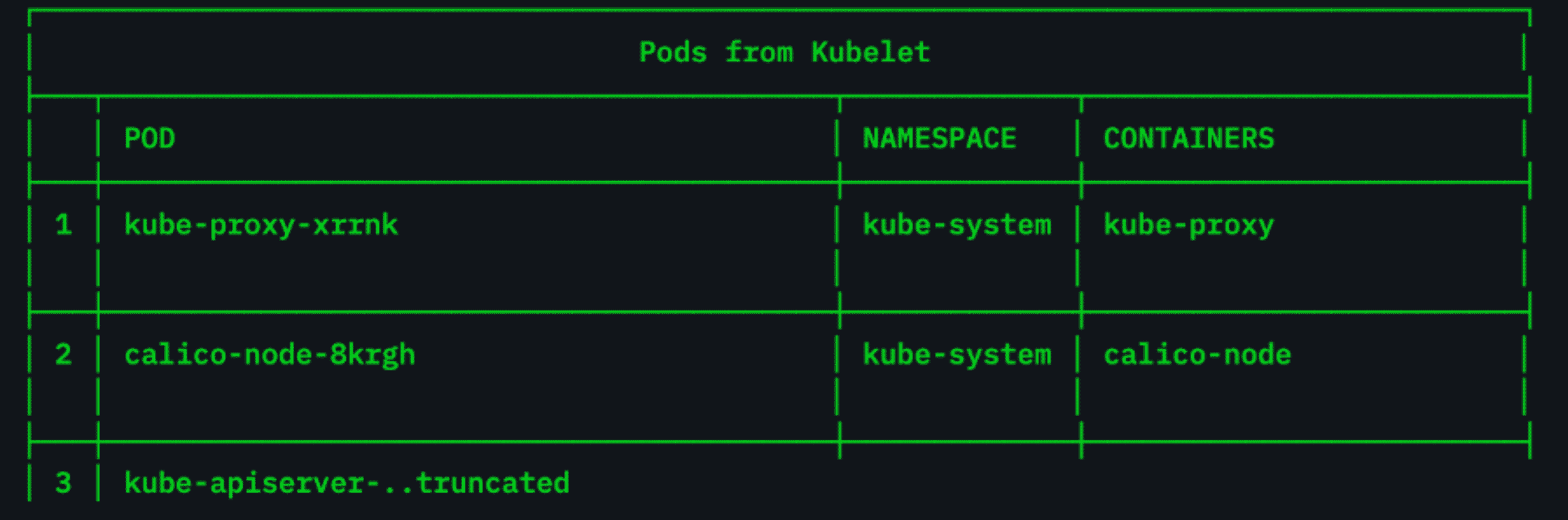
Are Your Kubernetes Clusters Configured Properly?
Researchers recently discovered some 900,000 Kubernetes clusters that were potentially exposed to malicious scans and data theft during a threat-hunting exercise.
Read More Tech Talk: The Attackers Journey Pt. 6
Noah King, one of Horizon3's front-end developers, is inviting you into his experience as he learns to be an expert at ethical hacking and get his OSCP cert!
Read More Go Hack Yourself: 5 Crazy Ways NodeZero Became Domain Admin
Attackers don't have to "hack in" using zero-day vulnerabilities. Often, attackers log in by chaining together misconfigurations, dangerous product defaults, and exploitable vulnerabilities to harvest and reuse credentials. This session will discuss five real-world attacks that enabled Horizon3.ai to become domain administrator, gain access to sensitive data, take over cloud VPCs, and compromise critical business systems. In most instances no...
Read More An International Look at Cybercrime
Authoritarian regimes have learned in recent years that cybercrime can be a profitable economic enterprise – so much so that they continue to invest substantial resources in large- and small-scale cybercrime.
Read More Beyond Password Issues: How NodeZero Found Access to an Organization’s Azure Cloud Environment
NodeZero is a generational leap beyond a traditional pentest – organizations often see that for themselves from the moment they give our autonomous pentesting platform a shot. NodeZero surfaces risks and weaknesses that would never have come up during a general vulnerability scan as it chains together attack tactics and techniques to illuminate your most critical impacts an attacker could...
Read More The Attackers Perspective Through Splunk Data & Workflows
As the industry accelerates toward a threat landscape of attack and defense by algorithm and machine, humans must run at machine speed to manage the stakes of tool misconfiguration, mishandling of logs, and missed patching opportunities. The NodeZero app for Splunk is a force multiplier—combining attacker insights into your unique environment with your existing Splunk data and workflows to enable...
Read More