Autonomous, AI-Powered Web Application Pentesting
From Login to Host Compromise
NodeZero® WebApp Pentest tests web applications the way real attackers operate. It traces real attack paths from authenticated access and application abuse through to cloud and on-prem host compromise, exposing real business impact, not isolated findings.
Horizon3.ai is expanding NodeZero into web application pentesting with an Early Access program grounded in how modern attacks actually unfold.
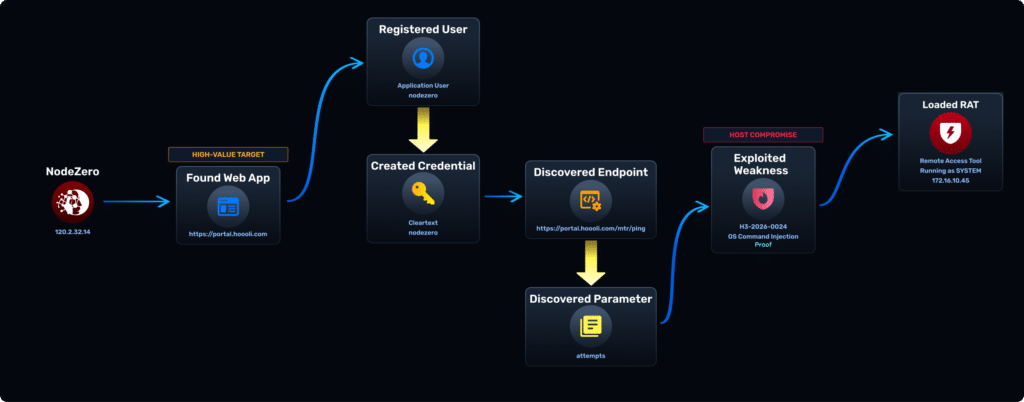
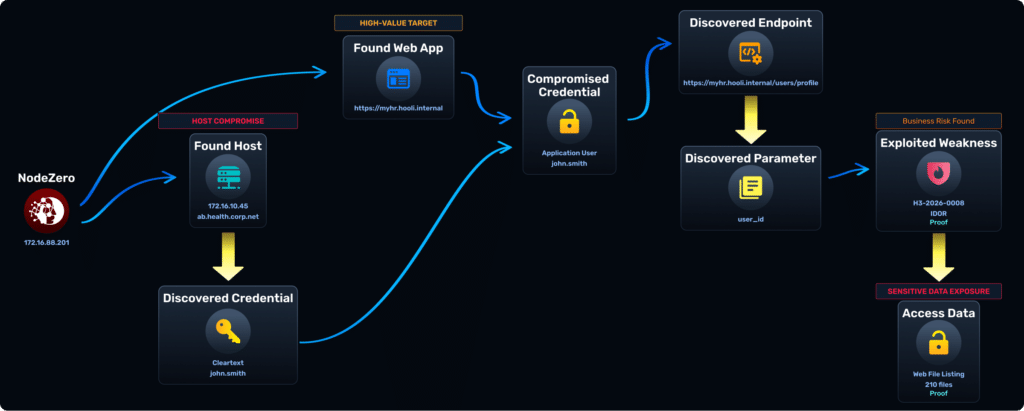
Attackers rarely “hack in.” They log in using compromised credentials, abuse application logic to escalate privileges, then pivot from the application into underlying infrastructure. NodeZero safely executes these real attack paths across internally and externally facing applications, identity, and infrastructure, showing how a single foothold becomes data exposure, host takeover, or domain compromise.
This is what it means to test at the intersection of web applications, identity, and infrastructure.
Compromised credentials are the most common starting point for modern attacks, collapsing the boundary between web application security and identity security. Once inside, attackers abuse business logic to expand access and elevate privileges.
Broken Access Control is the top web application weakness for a reason. It emerges after login, lives in application workflows, and directly determines how far an attacker can go. Most tools avoid this problem because it is hard to test at scale. We built for it.
A web application compromise is only the beginning. Real impact occurs when attackers pivot from the app into cloud and on-prem infrastructure to seize data, take over hosts, or gain domain-level control. If you stop at the application, you stop too early.
NodeZero WebApp Pentest: End-to-End Proof
NodeZero WebApp Pentest is built to operate at the intersection of web applications, identity, and infrastructure, where real attacks actually happen.
It unifies testing across these domains to show how a single exploitable weakness such as XSS, SQLi, Broken Access Control, XXE, or SSRF turns into a tangible business risk.
Because real attacks chain across domains, testing must do the same. Point-in-time assessments cannot keep up with systems that change daily and attackers who adapt continuously.
Continuous testing of pre-production and production applications using the same safe, autonomous engine that powers NodeZero, covered under an annual subscription
Full attack paths that chain web application abuse, credential compromise, and host takeover
Coverage of OWASP Top 10 weaknesses, common CWEs, and complex access control failures scanners routinely miss
Clear, actionable evidence of exploitability, not noisy or theoretical findings
Be First to Test Your Web Apps the Way Attackers Do
Join the NodeZero® WebApp Pentest Early Access program and get autonomous, AI-powered testing across web applications, identity, and infrastructure. See real attack paths from login abuse to host compromise and prove what’s exploitable before attackers do.