Cutting Through the Noise: Security Insights by Brad Hong
SEARCH
CATEGORIES
TAGS
Building FixOps: Architectural Considerations for Autonomous Security Workflows
Designing reliable autonomous security workflows requires more than AI and automation—it demands solid architecture. This guide explores orchestration frameworks, integration points, scaling strategies, and human oversight models that help teams move from prototypes to production-ready FixOps systems built for resilience, precision, and continuous verification at scale.
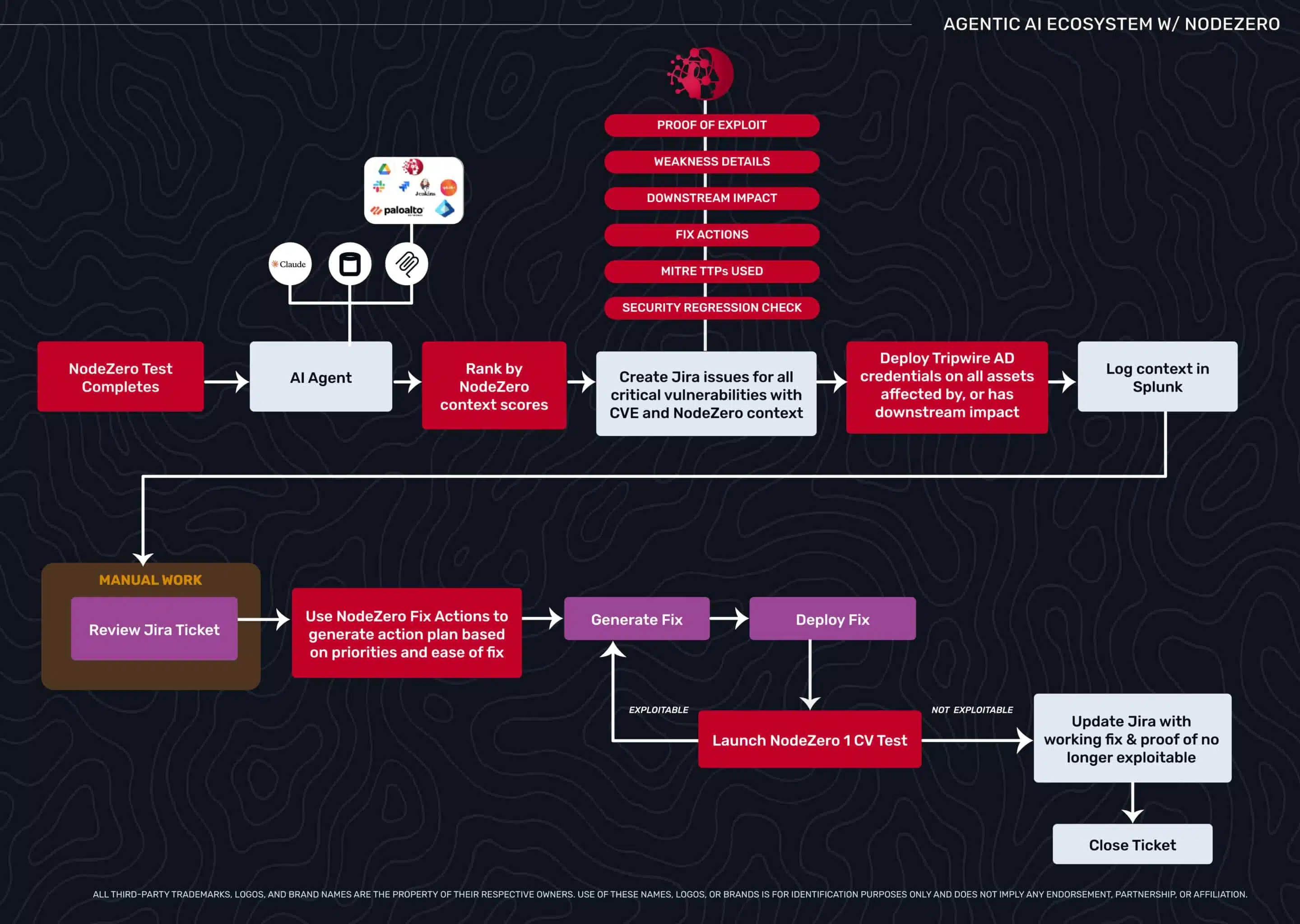
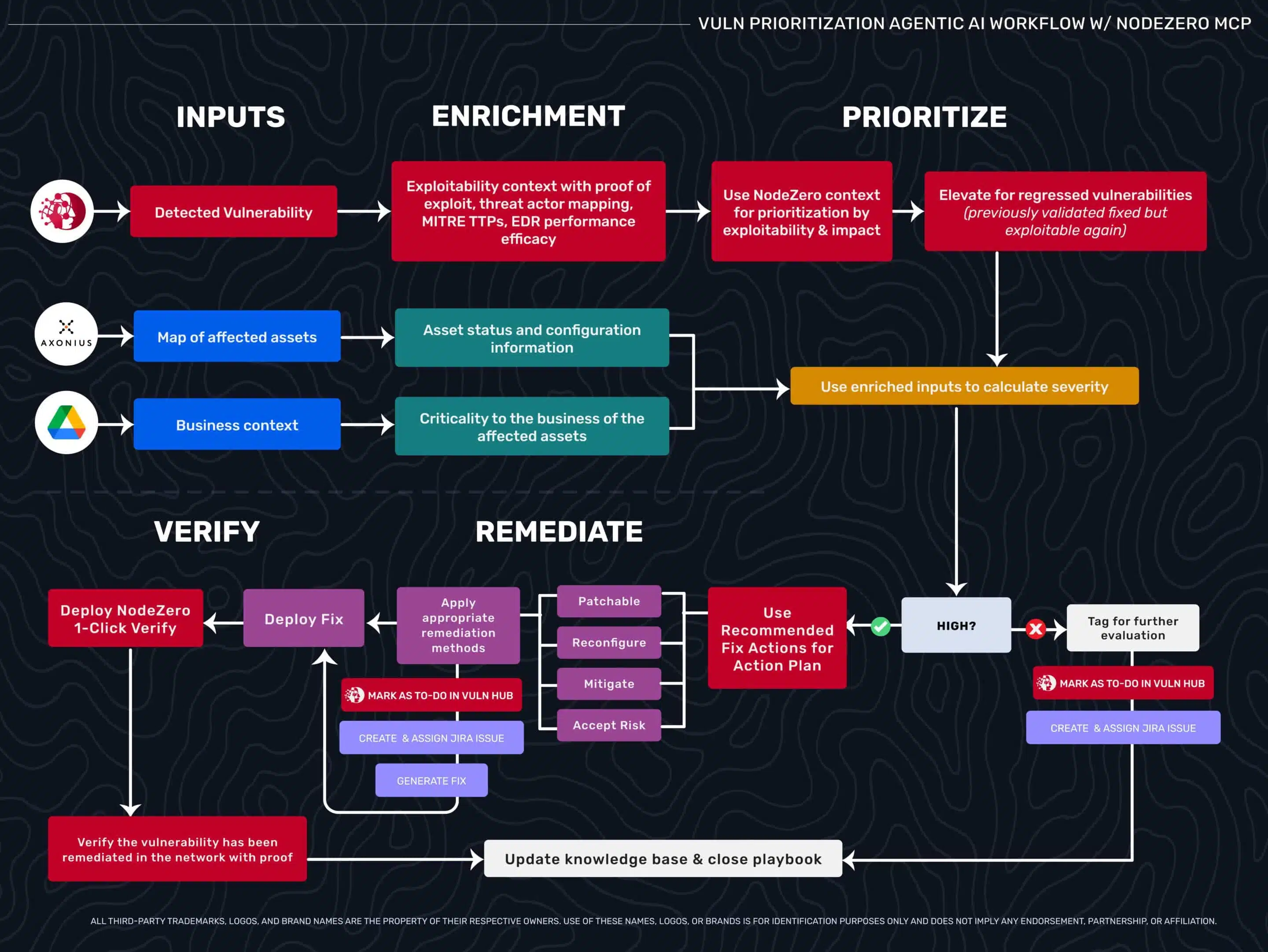
Beyond Triage: How Exploitability Data Transforms Agentic Security Workflows
Security teams drown in critical CVEs that don’t matter while missing medium flaws that lead to domain admin. This blog explores how exploitability data—validated through autonomous pentesting—enables agentic AI workflows to move beyond triage, prioritize what’s truly exploitable, and automate verification with confidence.
Uncover Kubernetes Security Weaknesses with NodeZero™
Discover key Kubernetes vulnerabilities, misconfigurations, and how NodeZero automates detection to secure containerized applications effectively.
Strengthening Cloud Security: A Comprehensive Approach
In the evolving landscape of cloud and hybrid environments, robust security measures are more critical than ever. In this webinar Brad Hong, CISSP, explores autonomous pentesting methodologies and strategies that can help your organization take a more efficient and comprehensive approach to securing your entire digital infrastructure that embraces multiple cloud vendors.
Outpace Emerging Cyber Threats with Horizon3.ai Rapid Response
In this webinar. Horizon3.ai cybersecurity expert Brad Hong covers our new Rapid Response service.
World Password Day: Credentialed attacks by the numbers
May 5, 2022
It’s World Password Day, but it’s never a bad time to think about credential security and usage. Credentialed attacks are the most popular means of entry into any digital infrastructure, and remain the easiest method of reconnaissance and privilege escalation for bad actors. With some of the most sophisticated open-source attack tools to date, it’s…
“And Then, My EDR Just Watched It Happen”
April 18, 2022
Learn how NodeZero empowers customers to run continuous penetration tests to find vulnerabilities from an attacker’s perspective, to verify fixes after remediation, and hold the EDR and the rest of the security stack accountable for delivering on their capabilities as designed.