Combining Compromised Credentials Enables Domain Takeover
When running internal phishing campaigns to help train employees, one challenge IT security teams face is explaining to leaders, “why the credentials of an intern (or whatever level employee) are valuable to attackers.” The common pushback security teams normally hear is, “They are an intern. They do not have access to anything critical, so why is it so important?”
Demonstrating how an intern’s credentials, combined with other issues, could lead to a domain compromise, sensitive data exposure, or other critical impacts is not an easy task when organizations do not have something like NodeZero™ on hand.
A credential injection test
A terrific way for security teams to tell the end-to-end story to leaders is to “inject” a low-level user’s credentials into a running NodeZero penetration test. NodeZero will then use those credentials as it identifies ways to compromise the environment.
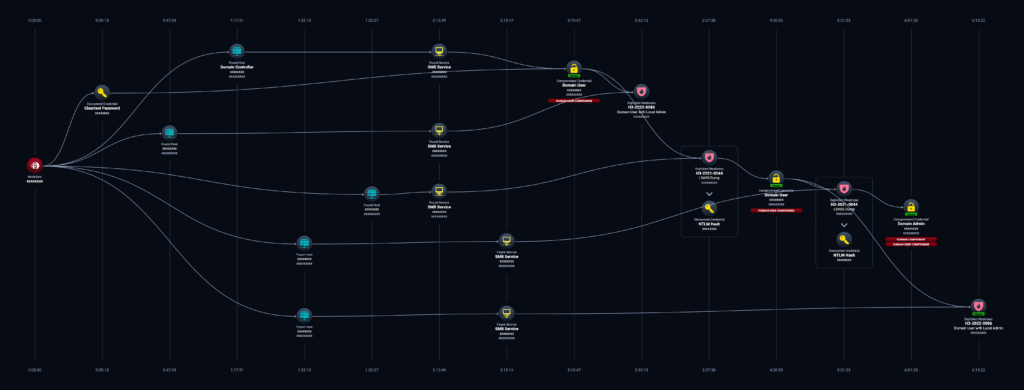
Below is an example of a real attack performed by NodeZero with no human penetration testers or red teams involved. NodeZero started with the privileges of a low-level domain user and ultimately ended up fully compromising the domain. The attack was executed safely against production systems that were not in a lab environment.
Attack Path to Domain Compromise
- In this case, NodeZero started out as an authenticated member of the internal network. NodeZero was given the credential for domain user user1.
- NodeZero verified the credential for domain user user1 in domain domain1 over SMB.
- NodeZero discovered that user1 has local Administrator privileges on a Windows machine, machine1. NodeZero raised a new weakness, H3-2022-0086: Domain User with Local Administrator Privileges.
- Logged in as user1 on machine1, NodeZero dumped credentials from LSASS memory. NodeZero raised a weakness H3-2021-0044: Credential Dumping – Local Security Authority Subsystem Service (LSASS) Memory.
- Among the credentials dumped from LSASS memory on machine1 is the NTLM hash for domain user user2. Using a Pass-The-Hash attack, NodeZero verified the credential for user2 against domain1 over SMB.
- NodeZero discovered that user2 has local Administrator privileges on another Windows machine, machine2. NodeZero raised a new weakness, H3-2022-0086: Domain User with Local Administrator Privileges.
- Logged in as user2 on machine2, NodeZero again dumped credentials from LSASS memory. NodeZero raised a weakness H3-2021-0044: Credential Dumping – Local Security Authority Subsystem Service (LSASS) Memory.
- Among the credentials dumped from LSASS memory on machine1 is the NTLM hash for domain user admin1. Using a Pass-The-Hash attack, NodeZero verified the credential for admin1 against domain1 over SMB.
- NodeZero further identified that domain user admin1 is a domain admin.
How can this work?
Typically…
- A domain user also has local admin rights.
- With local admin rights an attacker can access sensitive processes like LSASS.
LSASS stores credentials in memory for users active on the machine. The purpose of keeping these credentials in memory is for a form of single sign on, so the user does not have to reinput credentials for network resources shares, or services within the domain.
Once LSASS is dumped, additional credentials can be harvested and used to log into adjacent machines, where LSASS can be dumped again (and again, and again.)
It is highly likely that at some point, an LSASS dump will contain a privileged credential (e.g., Service Account, Domain Admin account, etc.)
In addition, the attacker has access to every system and data resource a compromised domain user credential has access to, unless those resources are MFA’d, but that is atypical for things like file shares and databases.
Note: Typically, EDR solutions should be able to block dumping credentials from LSASS, but in practice, the effectiveness of EDR solutions can vary widely depending on how they are configured.
The likely outcome
From something as simple as gaining a low-level employee’s credentials can allow attackers to eventually become a domain admin, which means the domain is fully compromised, and all hosts, domain user accounts, data, infrastructure, and applications tied to that domain should be considered fully compromised as well. Additionally, applications running on a domain-joined machine or any application that uses Active Directory integration to authenticate users should be considered fully compromised too.
Attack path details taken from NodeZero
As shown in Figure 1, during the attack, NodeZero leveraged:
- H3-2021-086: Domain User with Local Admin
- H3-2021-0044: LSASS Dump
- H3-2021-0044: LSASS Dump
- H3-2021-086: Domain User with Local Admin
The attack path involved 3 compromised credentials:
- Domain user user1 (injected into the pentest)
- Domain user user2
- Domain admin admin1
The attack spanned 5 hosts
Key takeaway
This attack path is very common in internal pentests and is typical of the methods real-world attackers use once they have breached the perimeter. Not a single CVE was used in this attack, no humans were involved in this attack, just NodeZero pivoting with credentials and eventually becoming Domain Admin in a little over six hours. The key takeaway is to ensure the least privilege access for users. Domain users having local admin privileges is what led to LSASS dumping twice in this case. In addition, tuning EDR solutions to detect and block credential dumping can help.