After completing a walkthrough of the Blue machine on the Hack The Box platform, feedback indicated that the analysis lacked depth. To address this and demonstrate a more advanced skill set, the next target selected was Active—a more complex and challenging machine on the same platform.
Summary
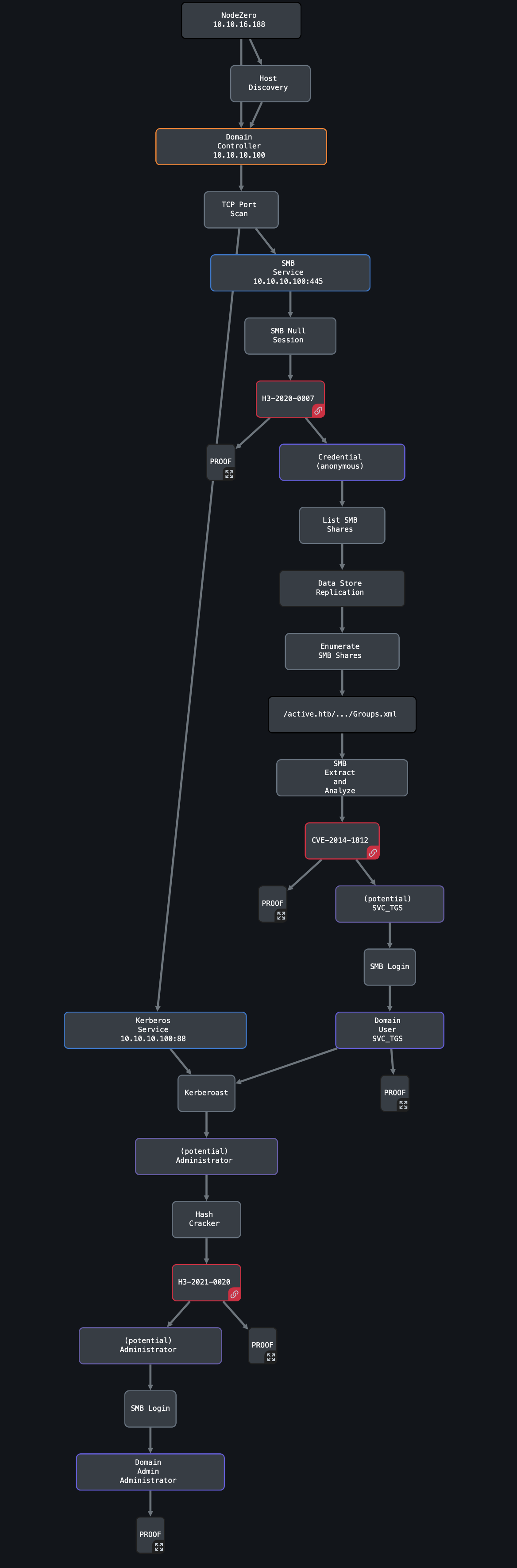
NodeZero obtained Domain Administrator privileges on Active by exploiting multiple issues common in Active Directory environments. First, it discovered cleartext credentials for the domain user SVC_TGS in a Group Policy file left in an open SMB share. Then, with domain user credentials, it escalated privileges to Domain Admin by executing a well-known Active Directory attack called Kerberoasting.
In addition, NodeZero found a second path to compromising Active using the critical vulnerability CVE-2020-1472, also known as ZeroLogon, which lets any unauthenticated attacker fully compromise a Domain Controller. This vulnerability was discovered a couple of years after the machine was released.
Timeline of Notable Events
| Timestamp (UTC) | Event |
|---|---|
| 2021-07-02 01:30:22 AM | Assessment started |
| 2021-07-02 01:31:02 AM | Identified an open SMB share called Replication accessible to any anonymous user |
| 2021-07-02 01:31:13 AM | Extracted cleartext credential for the domain user SVC_TGS in a Groups.xml file inside Replication share |
| 2021-07-02 01:31:32 AM | Identified the domain controller as vulnerable to critical vulnerablity CVE-2020-1472, a.k.a. ZeroLogon |
| 2021-07-02 01:31:42 AM | As the SVC_TGS user, performed a Kerberoasting attack to get a password hash for the Administrator user |
| 2021-07-02 01:33:38 AM | Cracked the Administrator user’s hash to recover the user’s cleartext password |
| 2021-07-02 01:33:53 AM | Logged into Active as Administrator, fully compromisng the domain |
Attack Graph
This is the attack graph that represents what NodeZero did:
Walkthrough
Enumeration
01:30:22 AM UTC – NodeZero began its assessment with the IP address 10.10.10.100. It confirmed the machine was live using an nmap ping sweep.
It ran TCP and UDP port scans using nmap and found multiple open ports.
Based on the presence of LDAP, SMB, Kerberos, and DNS, NodeZero concluded the machine was likely a Windows Domain Controller.
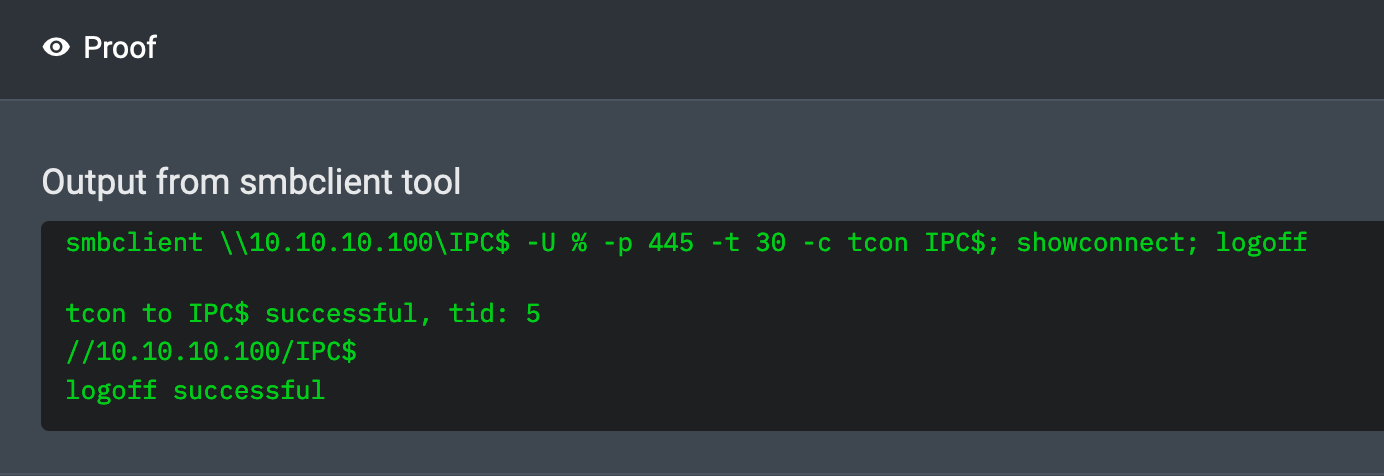
01:30:41 AM UTC – NodeZero confirmed that SMB port 445 permitted null session authentication by verifying anonymous access to the hidden IPC$ share. While low severity on its own, null sessions can sometimes expose valuable information such as usernames, groups, password policies, and available shares.
01:31:02 AM UTC – Using crackmapexec, NodeZero listed all SMB shares and confirmed that anonymous users had read permissions on a share called Replication.
Domain User Access
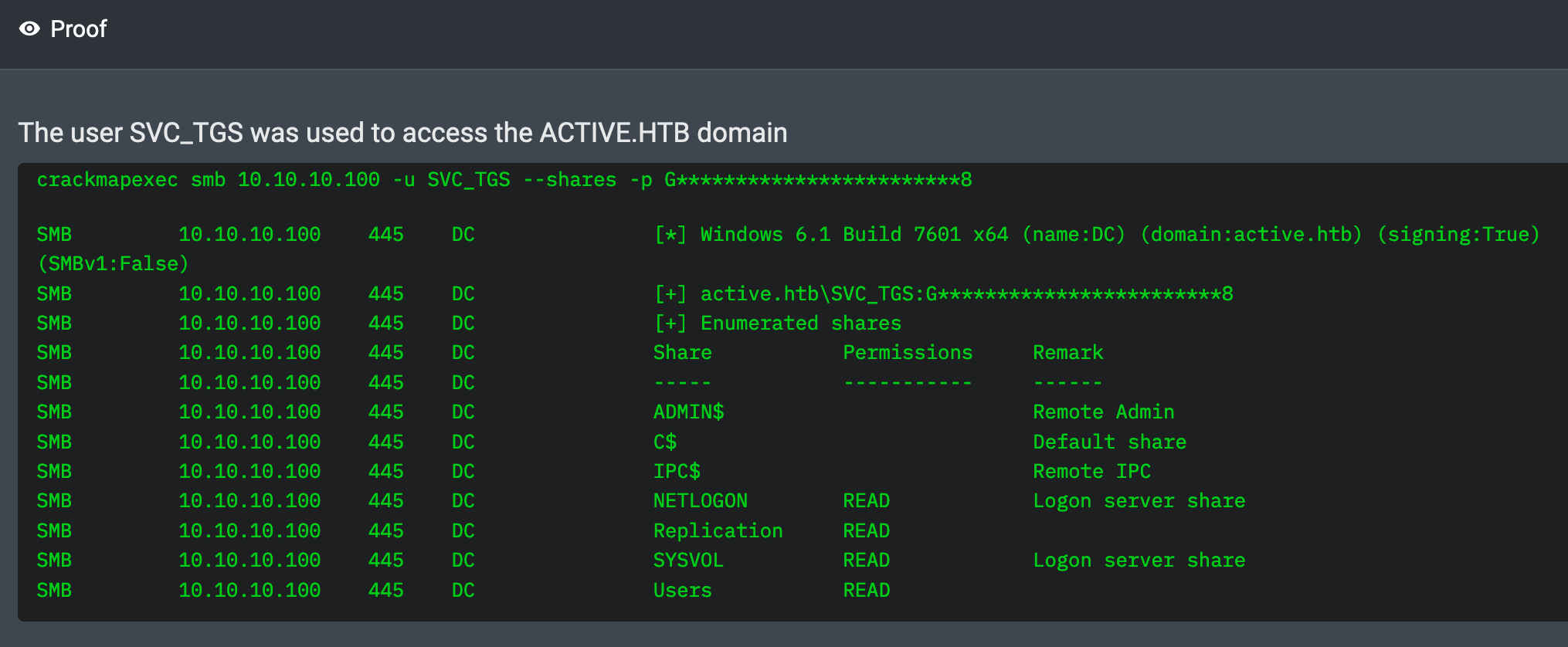
01:31:13 AM UTC – Using smbclient, NodeZero listed files in the Replication share and retrieved a file named Groups.xml. Inside, it found the password: GPPstillStandingStrong2k18 for the domain user SVC_TGS.
This is evidence of a known Active Directory vulnerability, CVE-2014-1812, which involves two issues:
- Group Policy passwords stored in files accessible to all domain users (typically in the SYSVOL share)
- Those passwords encrypted using a hard-coded AES key common across all Windows installations
Even after patching, any previously stored passwords remain unless removed manually.
In this case, the Groups.xml file was accessible to anonymous users in the Replication share, which was a replica of the SYSVOL share. NodeZero decrypted the password using the well-known AES key.
01:31:26 AM UTC – NodeZero confirmed the credentials were valid by logging in as SVC_TGS.
Escalating to Domain Administrator
NodeZero used a well-known technique called Kerberoasting, disclosed by Tim Medin in 2014, to escalate from domain user to Domain Admin.
Kerberoasting enables any domain user to recover cleartext passwords for other domain accounts that have Service Principal Names (SPNs) assigned. If the password is weak, the encrypted Ticket Granting Service (TGS) ticket can be brute-forced offline.
01:31:42 AM UTC – NodeZero used the Impacket script GetUserSPNs.py to query for SPNs tied to domain user accounts and requested a TGS ticket for the Administrator user, who was linked to the CIFS service.
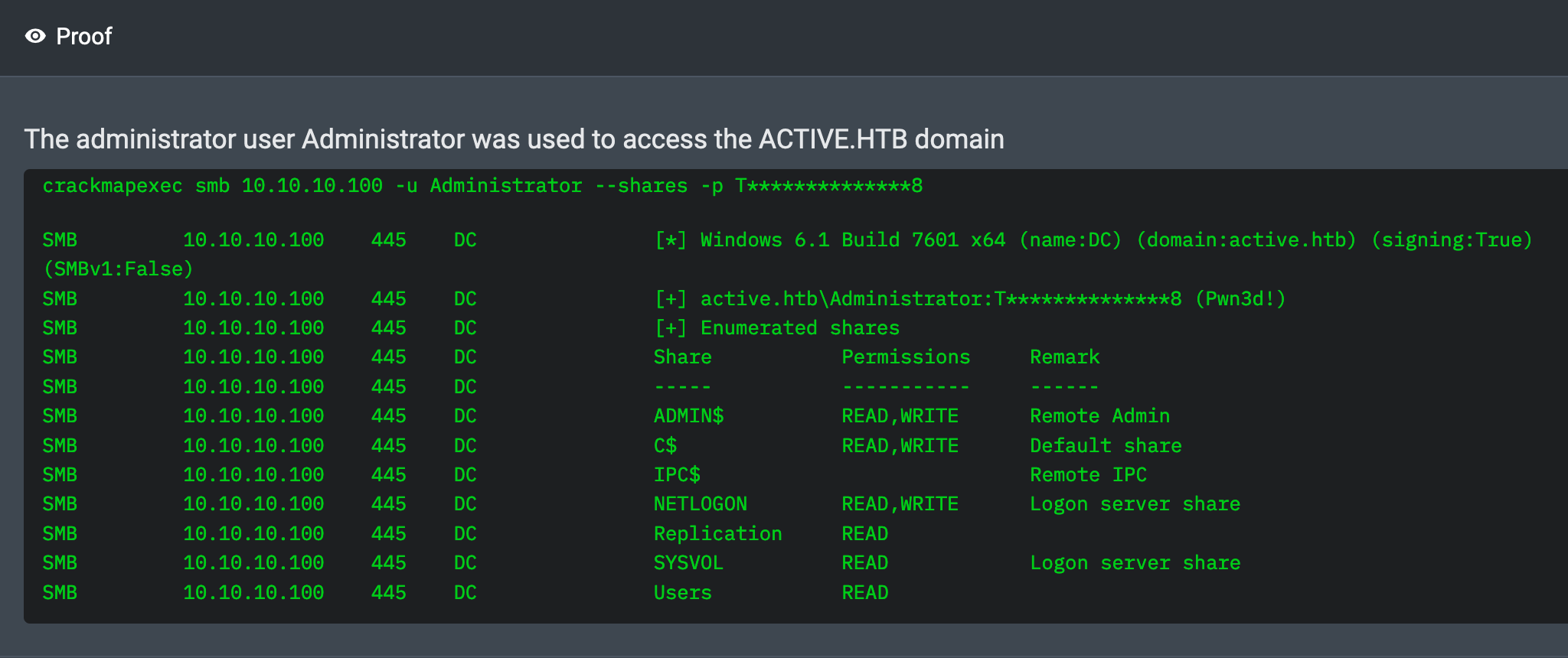
01:33:38 AM UTC – NodeZero cracked the Administrator hash using hashcat, revealing the password: Ticketmaster1968
01:33:53 AM UTC – NodeZero logged in as Administrator over SMB, fully compromising the domain.
Post-Exploitation
01:35:00 AM UTC – With Domain Admin privileges, NodeZero dumped all credentials from the machine using the Administrator account. It ran the auxiliary/scanner/smb/impacket/secretsdump module in Metasploit and retrieved the NTLM hash for the krbtgt user.
An Alternate Path To Domain Compromise
01:31:32 AM UTC – During the course of the assessment, NodeZero also identified that the domain controller was vulnerable to CVE-2020-1472 (ZeroLogon) — a critical vulnerability that allows any unauthenticated user to fully compromise the domain.
Although this vulnerability was discovered after Active was released, it presents a valid alternate path to domain compromise without any prior access.
Conclusion
In this post, NodeZero walked through a few basic “oldie-but-goodie” techniques for attacking Active Directory environments. These techniques proved helpful for fully compromising Active. But this is the very tip of the iceberg in terms of what’s possible. Securing Active Directory environments is truly hard work.