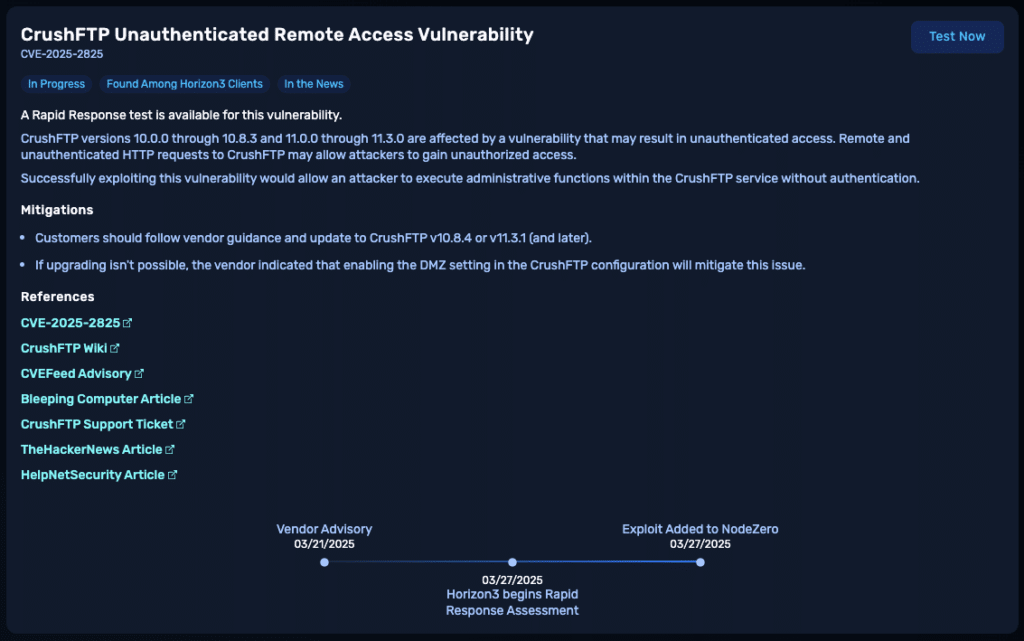
On March 21, 2025, CrushFTP released versions 10.8.4 and 11.3.1 in order to mitigate a critical authentication bypass vulnerability. Initially, there was no CVE assigned to this issue, but after waiting around for a few days, the good folks over at VulnCheck took matters into their own hands and assigned CVE-2025-2825, which put the vulnerability on Horizon3.ai’s radar.
Given that issues regarding CrushFTP have been known to appear in the CISA KEV in the past (such as CVE-2024-4040), Horizon3.ai researchers began digging into the patches to develop an exploit and triage our customers.
CrushFTP Users: What to Look For
The vulnerability is an authentication bypass, which could allow attackers to gain unauthorized access to the administrative functions of the CrushFTP service.
CrushFTP users should check session logs for successful authentication attempts from unknown sources for default CrushFTP accounts, such as “crushadmin” and “anonymous.” Session logs can typically be found under the “session_logs” folder in CrushFTP’s root logging directory. For example, in Docker-based deployments, the logging location is set to “/app/CrushFTP11/logs” by default.
SESSION|03/27/2025 12:41:24.636|[HTTP:250_22299:crushadmin:REDACTED_ATTACKER_IP] WROTE: *230 Password OK. Connected.*
SESSION|03/27/2025 12:41:24.636|[HTTP:250_22299:anonymous:REDACTED_ATTACKER_IP] WROTE: *230 Password OK. Connected.*Sample Session Logs
NodeZero Rapid Response Test for CVE-2025-2825
Horizon3.ai’s Attack Team has built an exploit for the CrushFTP vulnerability into the NodeZero platform. Customers can run targeted tests now to determine if they are vulnerable.
Go Crush Your Exposure
Given past exploitation of CrushFTP in the wild, we expect to see activity surrounding this vulnerability over the coming days. If you’re a CrushFTP user, we encourage you to apply patches as soon as possible.
As always, we’re here if you’d like a tailored demo to see how NodeZero can support you for this and future emerging threats.