The engineering team has been working tirelessly to improve the “what to wow” user experience, add more attack content, add indicators of best practices and improve analytical insights.
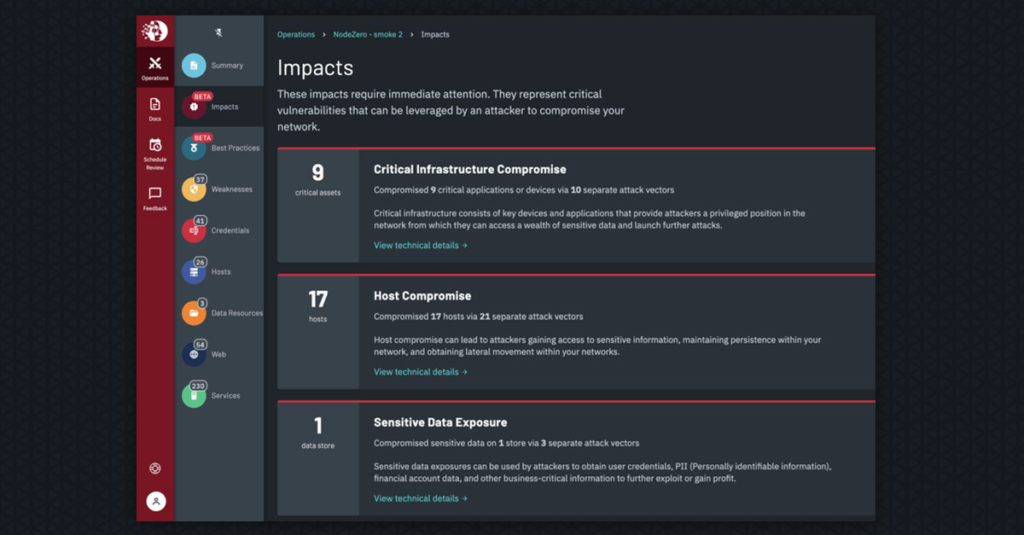
- Improving our “what to wow” user experience – In security, there are two types of findings: critical problems that require you skip lunch, or cancel plans with your family, to urgently fix and everything else that you need to fix someday soon. With the “Critical Impacts” feature, identifying critical findings is a few clicks away.



- Improving analytical insights – A “critical” finding for you might be a “low” finding for another enterprise, because context matters. You may have an exploitable Bluekeep vulnerability (CVSS score of 10), but if that vulnerability doesn’t enable data theft or systems disruption, is it really a critical? Similarly, you may have a directory traversal misconfiguration (CVSS score of 0.1) that enabled an attacker to gain domain administrator access to your network, which is a really big deal. Our “context scoring” feature now takes impact into account and subsequently increases or decreases the severity of a finding.

Our engineering team focused on these categories based on two observations from customer engagements:
- Our prospects kept comparing us to vulnerability scanners, which was very offensive (pun intended) because our goal is to disrupt those noisy legacy tools.
- Our results have decimated the PDF reports produced by manual pen testing consultants. In a recent customer engagement, we proved that 22/28 (80%) of the critical findings discovered by an offshore pen testing company could not actually be exploited and were really false positives, reinforcing our point-of-view that being vulnerable does not mean you’re exploitable.

[author] [author_image timthumb=’on’]https://horizon3.wpengine.com/wp-content/uploads/2021/08/Tony.jpg[/author_image] [author_info]Anthony “Tony P” Pillitiere is the co-founder and Chief Technology Officer at Horizon3.ai, a cyber security company passionate about helping organizations improve their security posture through automated penetration testing. Prior to his position at Horizon3.ai, he served 21 years in the United States Air Force, 16 of which were spent in highly competitive positions at organizations with highly sensitive missions. His breadth of experience spans from supporting DoD research and development and education and training, to tactical communications and enterprise communications across six bases and five deployments to the Middle East. His twilight position was as the Deputy CTO for a U.S. SOCOM organization, where he drove the digital transformation that significantly increased the efficiency and capability of national mission force and the intelligence community. During his service, he earned two degrees in technology and military technical instruction; as a disabled veteran, he is extremely passionate about helping veterans any way he can. But his biggest passion of all is his family, his amazing wife and two beautiful children.[/author_info] [/author]