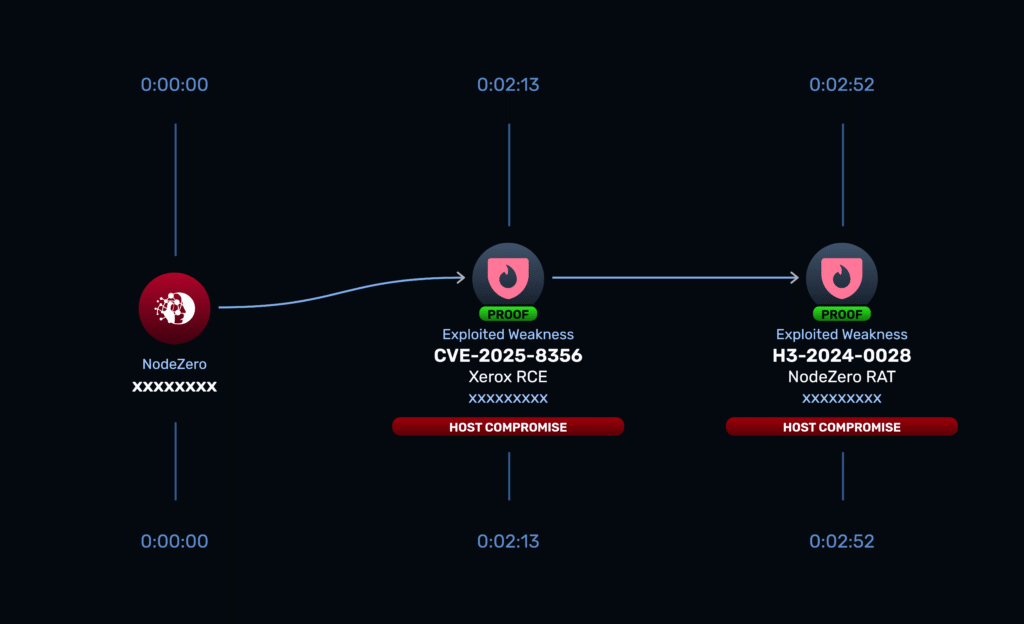
TL;DR
We discovered XXE Injection (CVE-2025-8355) and Path Traversal (CVE-2025-8356) vulnerabilities in Xerox FreeFlow Core, a print orchestration platform. These vulnerabilities are easily exploitable and enable unauthenticated remote attackers to achieve remote code execution on vulnerable FreeFlow Core instances. These issues are patched in Xerox FreeFlow Core version 8.0.5, and we encourage all users to upgrade as soon as possible.
Background
A few months ago, we received a support request from a customer concerned about a potential false positive in their environment. NodeZero had reportedly exploited an XXE (XML External Entity) injection issue on one of their hosts, but for a product that wasn’t installed on the host. In fact, the product wasn’t even present in their environment.
What’s interesting, however, is that NodeZero was still somehow receiving callbacks from this host with clear indicators of an XXE vulnerability having been exploited. This can sometimes happen when WAFs (web application firewalls) or other security utilities are in place that do some sort of introspection on inbound requests. That said, given the high standards for actual proof of exploitation that we hold for NodeZero modules, it was obvious the callbacks indicated there was something more going on, so we decided to dig a little deeper.
FreeFlow Core Overview
The product at the center of the issue was something called Xerox FreeFlow Core. FreeFlow Core is a print orchestration platform used for prepress automation workflows. You’ll usually find it deployed in environments that utilize commercial print shops, such as packaging and marketing providers, universities, government agencies, and anyone else with a need for large-scale printing operations.
Given the nature of the product, FreeFlow Core installations have a lot of moving parts and require relatively open access and availability, which combined with the fact that print jobs of this kind generally contain pre-public information around marketing campaigns makes this an ideal target for attackers.
Xerox’s security guide for the product, which details the many services involved and provides guidance for security administrators, contains the following application architecture overview.
It also gives descriptions of the ports for each running service.
CVE-2025-8355 – External XML Entity Injection Vulnerability
The service of interest in our environment happened to be the JMF Client service listening on port 4004. This service is responsible for handling JMF (Job Message Format) messages. These messages contain commands for managing print jobs and reporting on their status. The binary responsible for handling these messages (jmfclient.jar) included an XML parsing utility that did not properly sanitize or limit usage of XML External Entities. By submitting a request like the following, we were able to perform SSRF (server-side request forgery) attacks through this vector.
Ordinarily, we’d try to leverage this issue for greater impact, but during our investigation, we came across another issue with a much more severe and immediate impact.
CVE-2025-8356 – Path Traversal Vulnerability
While investigating the XML parsing routines of the service, we discovered that some JMF commands included the processing of files. Upon closer inspection, we noticed that the mechanism controlling the upload of these files contained a path traversal vulnerability. Below is a snippet of the vulnerable function (processIncomingRQEMessage()).
The following request demonstrates JMF command message that triggers this routine and places a webshell in a publicly accessible location.
While the service on port 4004 doesn’t contain any features that would allow this file to be served, the primary web portals provide all the necessary functionality for executing and serving our malicious payload.
Remediation and Disclosure Timelines
These issues were disclosed in accordance with Horizon3.ai’s Vulnerability Disclosure Policy. For more information, please refer to Xerox’s advisory. Xerox has mitigated these issues in FreeFlow Core version 8.0.5.
Coverage for these issues is already available in NodeZero. To see how the NodeZero platform can help uncover and remediate critical vulnerabilities like this in your environment, visit our NodeZero Platform page or speak with an expert by requesting a demo.
CVE-2025-8355 Timeline
- June 12, 2025 – Horizon3.ai requests dedicated security contact from Xerox via https://forms.business.xerox.com/en-us/xerox-security-response-center/
- June 13, 2025 – Xerox provides security contact details.
- June 23, 2025 – Horizon3.ai discloses issue to Xerox.
- June 24, 2025 – Xerox acknowledges and assigns a case number.
- July 4, 2025 – Xerox provides status update.
- July 22, 2025 – Horizon3.ai requests status update.
- July 24, 2025 – Xerox provides status update.
- July 30, 2025 – Xerox provides a preview patch.
- July 31, 2025 – Horizon3.ai confirms that the original PoC no longer works after applying the patch.
- August 6, 2025 – Xerox provides pertinent advisory information.
- August 8, 2025 – Xerox releases patch and advisory.
- August 13, 2025 – This write-up.
CVE-2025-8356 Timeline
- June 24, 2025 – Horizon3.ai discloses issue to Xerox.
- June 24, 2025 – Xerox acknowledges and assigns a case number.
- July 4, 2025 – Xerox provides status update.
- July 22, 2025 – Horizon3.ai requests status update.
- July 24, 2025 – Xerox provides status update.
- July 31, 2025 – Xerox informs Horizon3.ai that the installer provided for XXE issue includes a fix for this issue and requests verification.
- August 4, 2025 – Horizon3.ai confirms that the original PoC does not work in the patched version provided.
- August 6, 2025 – Xerox provides pertinent advisory information.
- August 8, 2025 – Xerox releases patch and advisory.
- August 13, 2025 – This write-up.