Attack Paths
SEARCH
CATEGORIES
TAGS
The FreePBX Rabbit Hole: CVE-2025-66039 and others
December 11, 2025
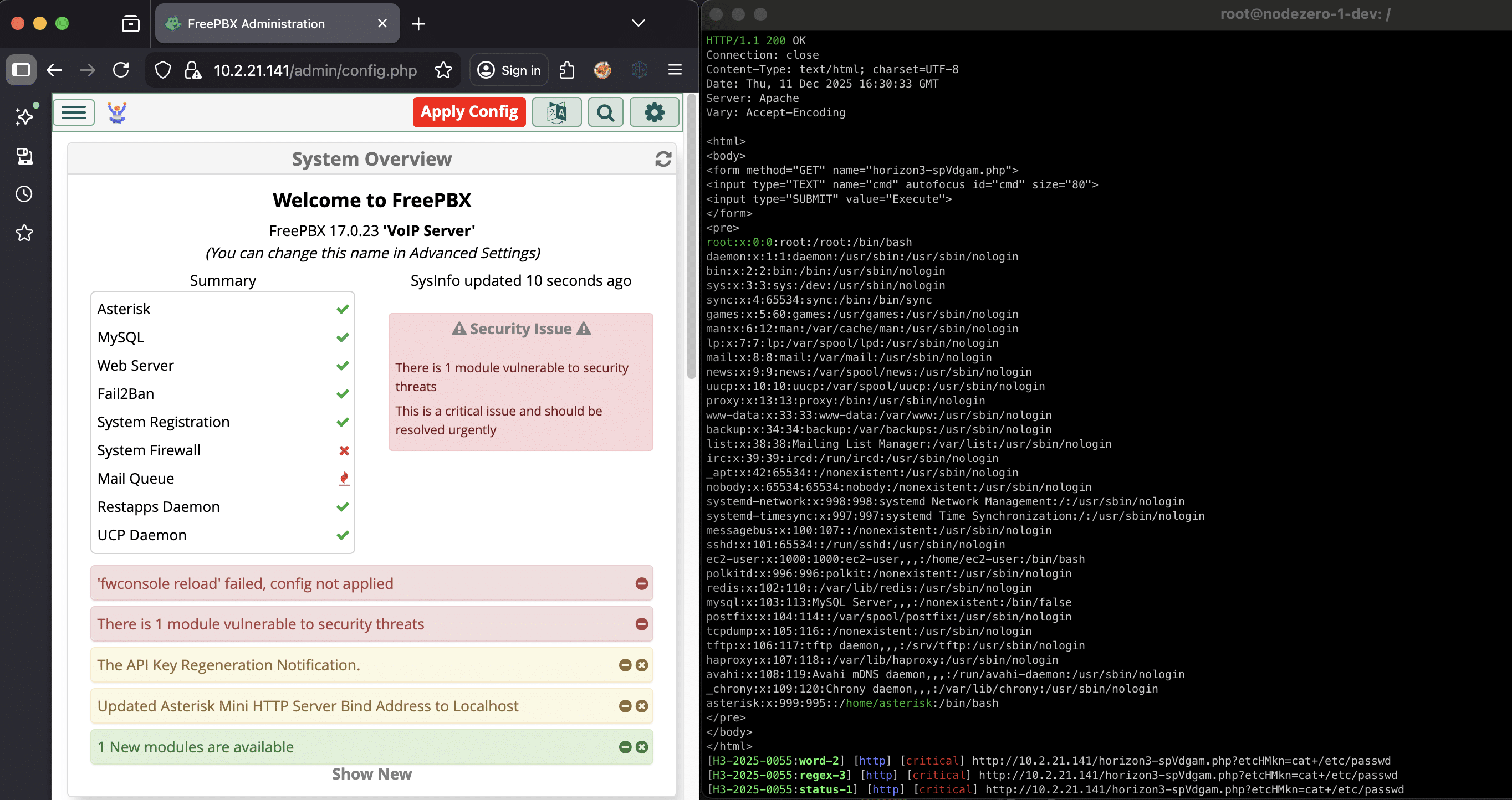
We dive into a new set of FreePBX issues beyond CVE-2025-57819: an authentication bypass in webserver mode (CVE-2025-66039), multiple SQL injections (CVE-2025-61675), and an arbitrary file upload bug leading to remote code execution (CVE-2025-61678). Together, they allow authenticated or unauthenticated attackers to achieve code execution on vulnerable FreePBX instances using risky auth settings. This write-up…
Hack The Box – Retro
November 10, 2025
NodeZero® autonomously solved Hack The Box Retro in just 11 minutes, chaining SMB guest access and weak credentials into an ADCS privilege escalation. This demonstration highlights how autonomous pentesting uncovers exploit chains and validates real attack paths, proving Horizon3.ai’s commitment to evidence-based, attacker-validated security.
The Quiet Attack Path
October 21, 2025
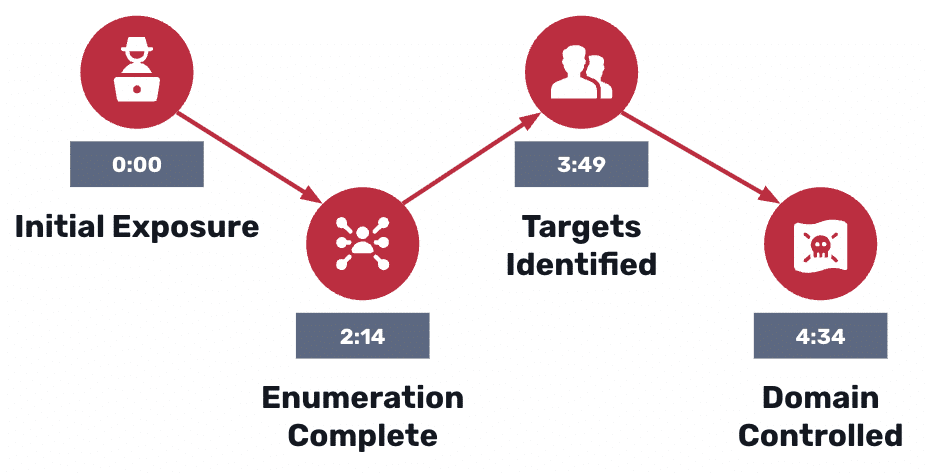
Attackers turn native Active Directory features into a low-noise, high-impact playbook: stealthy enumeration, Kerberoasting, and AS-REP roasting can produce crackable credentials and clear paths to domain admin in minutes. This post walks through the first 15 minutes of an AD intrusion, why traditional SIEM/EDR struggles to detect it, and what defenders must catch early to…
How Hackers Weaponize Slack: Lessons From Real Slack Dump Attacks
Slack's popularity creates data exfiltration risks. Autonomous pentesting finds hidden vulnerabilities.
The Value of Data Pilfering at Scale
Hackers don’t break in, they log in. This has never been more true – as the demand for data increases, more files than ever are being stored across the enterprise. Local files, file shares, cloud backups, and more are filling up with precious data. And with that, comes increased risk that the data being stored…
On-Prem Misconfigurations Lead to Entra Tenant Compromise
As enterprises continue to transition on-premises infrastructure and information systems to the cloud, hybrid cloud systems have emerged as a vital solution, balancing the benefits of both environments to optimize performance, scalability, and ease of change on users and administrators. However, there can be risks involved when connecting a misconfigured or ill-protected network to cloud…
NodeZero APT: Azure Password Spray Leads to Business Email Compromise
February 6, 2024
NodeZero APT: Azure Password Spray to Business Email Compromise
The Elephant In the Room – NTLM Coercion and Understanding Its Impact
January 9, 2024
Since introducing NTLM coercion techniques such as PetitPotam into the NodeZero platform, we frequently have security practitioners request help understanding these techniques and what impact they have to their enterprise. There is a lack of concise resources to inform Blue Teams on how these techniques work, and clearly distinguishing them from other misconfigurations/vulnerabilities in the…
AWS Misconfiguration Leads to Buckets of Data
December 8, 2023
Misconfigured AWS Role Enables Cloud Initial Access
Apache ActiveMQ RCE Leads to Domain Compromise
December 1, 2023
Pervasive CISA Known Exploited Vulnerability Enables Initial Access