Resource Center
Welcome to our cybersecurity resource center where we uncover how malicious actors exploit weaknesses in systems, while going beyond the technical aspects and examining real-world perspectives across various industries.
Filters
Showing 409–414 of 473 results
Credential Misconfigurations
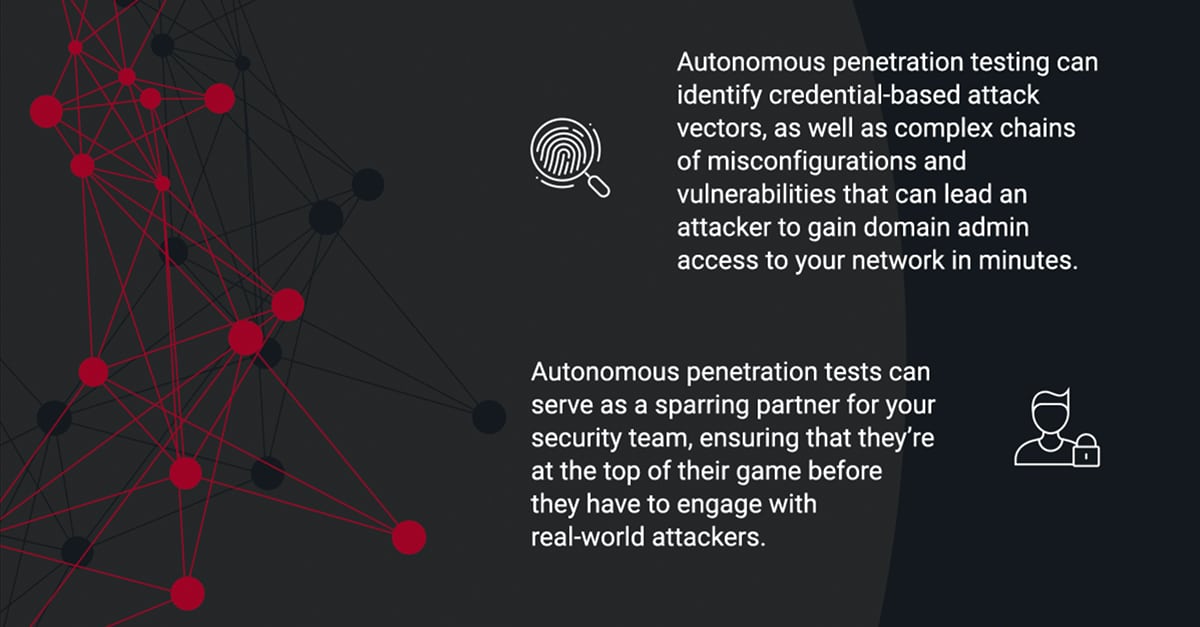
Are your credential policies implemented right? Are your enterprise accounts configured correctly? How do you know? Most phishing, ransomware, and credential attacks start by gaining access to a host and compromising a domain user (Credential Attacks – Horizon3.ai). With a credential in hand, an attacker can persist and pervade, appearing like a legitimate user and maneuver through your network with...
Read More Named 2021 Winner of the Pitch
Named a Winner of The Pitch 2021 by Constellation Research
Read More Apache CVE-2021-41773, CVE-2021-42013
We wanted to do something a little bit different with this post. Our vulnerability disclosures, exploit proof-of-concepts, and attack analysis blog posts have been awesome, but they have been catering to an offensive security audience.
Read More Exposed & Exploited
While so many are focused on vulnerabilities and malware on endpoints, understanding the attack paths an attacker would exploit to hold your business and brand at risk is key.
Read More Horizon3.ai Named a Winner of The Pitch 2021 By Constellation Research
PRNewswire: 10/05/2021 Horizon3.ai today announced it was named a first-place winner of The Pitch, a new competition for enterprise startups hosted by Constellation Research. The industry wide two-day event brought together startup founders, enterprise technology decision makers, venture capitalists, and system integrators to identify the next big player in innovation. Horizon3.ai was chosen as a leading startup in Core Tech...
Read More