Resource Center
Welcome to our cybersecurity resource center where we uncover how malicious actors exploit weaknesses in systems, while going beyond the technical aspects and examining real-world perspectives across various industries.
LATEST VULNERABILITIES
WEBINAR REPLAY
SEARCH
CATEGORIES
TAGS
SEARCH
CATEGORIES
TAGS
Vulnerable ≠ Exploitable
September 19, 2021
The hardest part of cyber security is deciding what NOT to do. Being vulnerable doesn’t mean you’re exploitable.
OMIGOD – RCE Vulnerability in Multiple Azure Linux Deployments
September 16, 2021
Overview On September 14, multiple vulnerabilities were discovered by researchers at Wiz.io. The most critical of them being CVE-2021-38647, now dubbed OMIGOD, which effects the Open Management Infrastructure (OMI) agent in versions 1.6.8.0 and below. Azure customers effected by this vulnerability are still vulnerable and must take manual action to ensure the OMI agent is updated.…
Hack The Box – Jerry
September 16, 2021
The Jerry machine from the Hack The Box platform nicely illustrates the danger of weak and default credentials.
Confluence Server OGNL Injection: CVE-2021-26084
September 13, 2021
On August 25, 2021, Atlassian released a security advisory for CVE-2021-26084, an OGNL injection vulnerability found within a component of Confluence Server and Data Center. This critical vulnerability allows an unauthenticated attacker to execute arbitrary commands on the server. A few days later, on August 31, security researchers @iamnoob and @rootxharsh quickly developed a working proof of concept given the vulnerability…
The Password Pandemic
September 10, 2021
Credential attacks bypass traditional defenses and cause billions in damage. Learn why they work, what’s at risk, and how Horizon3.ai helps fix what matters.
Hack The Box – Active
September 5, 2021
NodeZero compromises the "Active" machine on Hack The Box by chaining classic Active Directory vulnerabilities: GPP password exposure, Kerberoasting, and CVE-2020-1472 (ZeroLogon). This advanced walkthrough builds on earlier feedback and demonstrates multiple escalation paths to Domain Admin.
ProxyShell: More Ways for More Shells
September 4, 2021
In August, Orange Tsai released details and also spoke at BlackHat and DEFCON detailing his security research into Microsoft Exchange. His latest blog post details a series of vulnerabilities dubbed ProxyShell. ProxyShell is a chain of three vulnerabilities: CVE-2021-34473 - Pre-auth Path Confusion leads to ACL Bypass CVE-2021-34523 - Elevation of Privilege on Exchange PowerShell Backend CVE-2021-31207 - Post-auth Arbitrary-File-Write leads to…
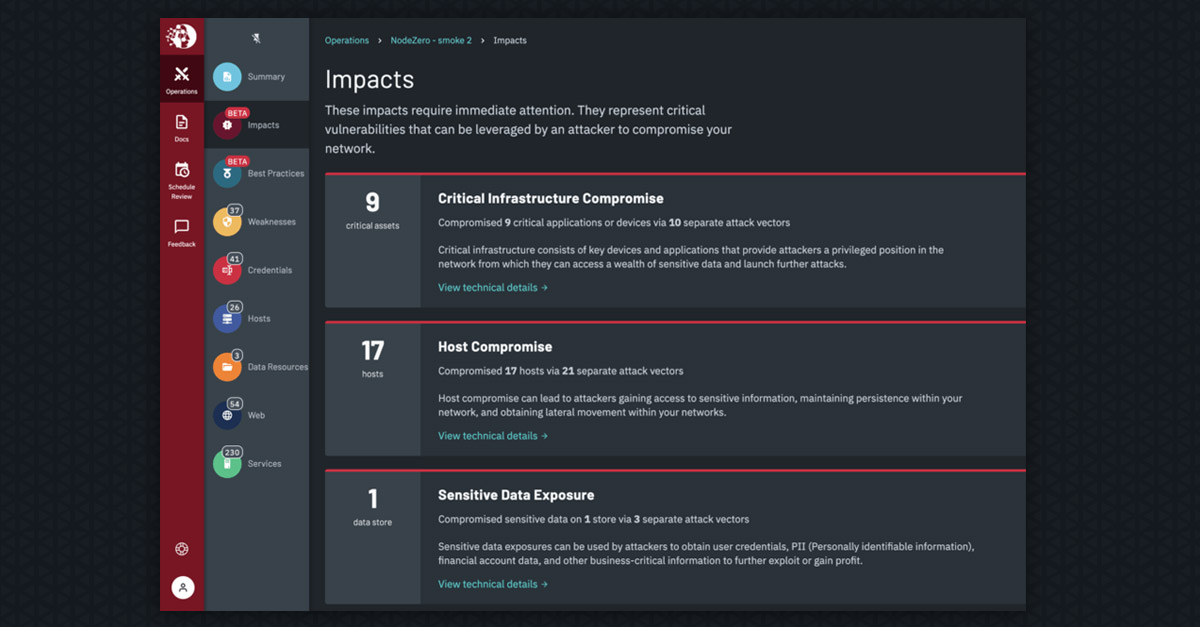
Product Updates from our CTO
August 27, 2021
The engineering team has been working tirelessly to improve the "what to wow" user experience, add more attack content, add indicators of best practices and improve analytical insights. Improving our "what to wow" user experience – In security, there are two types of findings: critical problems that require you skip lunch, or cancel plans with…
Hack the Box – Blue
August 27, 2021
NodeZero exploited EternalBlue on HTB’s Blue machine to gain system access and dump credentials, showing the risk of unpatched SMB vulnerabilities.
Compliance In Security: Go from Compliant to Secure
August 17, 2021
Learn why regulatory compliance is not enough for true cybersecurity. Discover how continuous automated pentesting and network segmentation help you move beyond check-the-box security.