As we approach the holiday season, it is important that our customers stay vigilant and continue a regular cadence of autonomous pentests. Although it’s the time of year for holiday cheer, we’ve seen cyber threat actors (CTAs) take advantage of lackadaisical company manning and low staff.
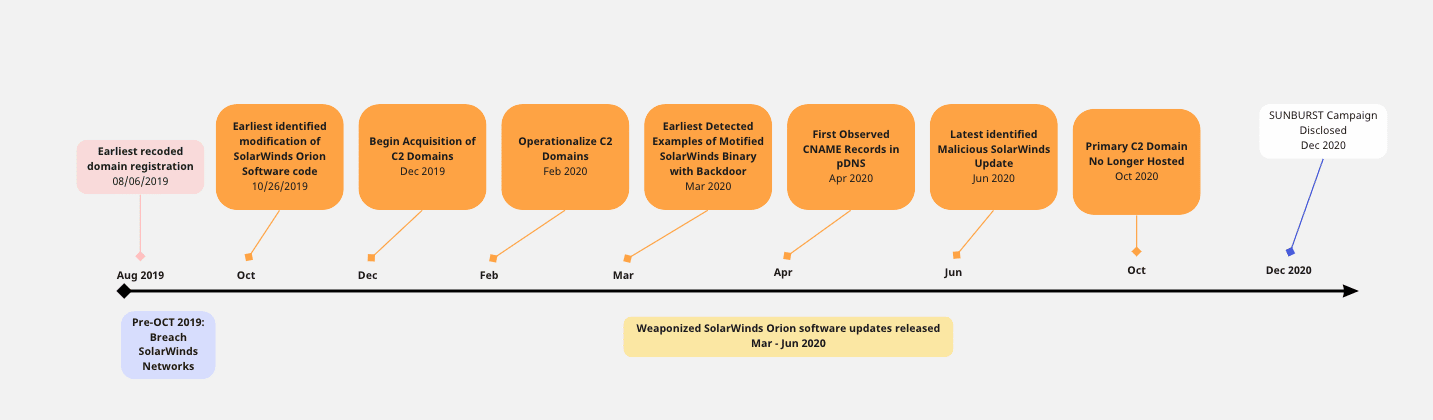
In September 2020, “the SolarWinds (major software company) hack, one of the biggest cybersecurity breaches of the 21st century” and was considered a highly lucrative target for CTAs based on its privileged access to IT systems. Specifically, the SolarWinds Orion IT monitoring software was targeted, allowing access to hundreds of thousands of organizations around the world to include portions of the US Government. Currently, nearly 30% of Horizon3 customers still use or have used SolarWinds applications in their networks, and two years later with 7% still finding the SolarWinds Orion API Authentication Bypass Vulnerability (CVE-2020-10148) in their pentests.
According to open-source research, below is the SolarWinds hack timeline:
Log4Shell: 2021’s worst holiday gift
Another example of a large-scale holiday season attack includes the Log4Shell remote code execution (RCE) vulnerability (CVE-2021-44228) that was surfaced right before Christmas in late 2021. On December 9, 2021, this new vulnerability was discovered in the Apache Log4j open source library, which is used in most of the developed java applications. Due to the proliferation of Log4j in java, “the number of devices that could potentially be affected by the security vulnerability is approximately 2.5 – 3 billion.” CTAs can exploit a vulnerable application by sending a crafted user input to it, hoping that the application will log their arbitrary code as input and allow them persistent access, as well as lateral movement. One year later, 64% of Horizon3 customers using NodeZero are still experiencing the CVE-2021-44228 vulnerability in their environment.

According to open-source research, below is the Apache Log4j timeline:
- December 9, 2021 – Original vulnerability disclosed and first patch (2.15.0) was made available
- December 14, 2021 – Second vulnerability disclosed and second patch (2.16.0) was made available
- December 18, 2021 – Third vulnerability disclosed and third patch (2.17.0) was made available
- December 28, 2021 – Fourth vulnerability disclosed and fourth patch (2.17.1) was made available
At the end of the day, attackers care greatly that we want to take some time off and enjoy our families, because that is when we are at our weakest. CTAs use these “down times” to take advantage of low staffing and chaos surrounding the holidays to deploy new tactics, techniques, and procedures (TTPs), while also focusing on targets with the biggest bang for the buck.
Remaining vigilant throughout the holiday season will help ensure your systems and networks are secure, which is why adopting an autonomous approach to proactively finding those attack vectors can save your security team its most critical resource: time. Incorporating a regular pentest cadence will get you results quickly, so mitigations and verifications are timely, giving you much needed time to enjoy the holidays!
Albert Martinek is a Customer Threat Analyst with Horizon3.ai.


