Planted where attackers escalate
Tripwires are embedded directly into Active Directory. They appear vulnerable to attack but are in actuality uncrackable.
Decoys that Blend In. Alerts that Stand Out.
Active Directory is one of the most targeted systems in every enterprise. Nearly 90 percent of Global 1000 organizations rely on AD to manage on-prem and hybrid users and assets; reaching Active Directory is the ultimate prize for attackers, with more than 40 percent of AD attacks resulting in a compromise.
As the NSA and partner agencies warn, “Gaining control of Active Directory gives malicious actors privileged access to all systems and users… bypassing other controls and accessing critical business applications at will”.
Read the NSA guidance on Active Directory compromises here.
Attackers don’t hack in, they log in: they enumerate accounts, steal Kerberos tickets, and abuse weak trust relationships under the guise of normal activity, evading traditional detection until they escalate privileges, seize the domain, and deploy ransomware or destructive sabotage.
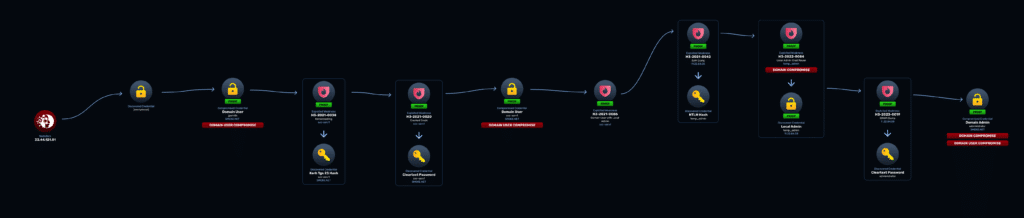
AD Tripwires are decoy accounts created by attackers to catch attackers, they are designed to blend in with production identities to look exploitable and irresistible, targeting specific techniques threat actors use most — kerberoasting, AS-REP roasting, and metadata scraping. Any interaction is suspicious by definition and if one is touched, you’ll know an attacker is in your AD.
Receive high-fidelity alerts the moment a tripwire is touched, getting proof of real attacker activity instead of noisy guesses.
Detect privilege escalation attempts in minutes before attackers reach domain admin.
Validate that your SOC and detection tools can detect and respond to identity attacks in production.
Catch identity attacks that bypass traditional monitoring, minimizing attacker dwell time.
Leverage detection methods validated by government-backed research as the only effective approach.
AD Tripwires protect the identities and privileges attackers target most.
Tripwires confirm our SOC can detect and respond to real AD exploitation attempts.
By catching exploitation of AD in real time, we stop attacks before they spread.