- The Exploitation of Critical CISA Known Exploited Vulnerabilities (KEV)
- Exploitation of Critical VMware Vulnerabilities
- Misconfigurations And Vulnerabilities in DevOps Tools (Jenkins, GitLab, Kubernetes, and Docker)
- Misconfigurations and Vulnerabilities in Routers, iLOs, iDRACs
- Implications of Failures to Patch and Misconfigurations
- Policy Recommendations and Mitigation Actions

Many exploitable vulnerabilities often have prescribed solutions already available.
Over the last year, we have seen many of our Horizon3.ai customers run pentests only to find that their systems suffer from exploitable vulnerabilities that are several years old and have relatively easy fixes in the form of vendor-provided patches. This includes vulnerabilities from CISA’s list of Top 15 Routinely Exploited Vulnerabilities list and their Known Exploited Vulnerabilities catalog. Taken together, these lists provide a good starting point for cybersecurity professionals to understand what vulnerabilities are being actively exploited and what actions to take to fix or mitigate the threat.
Further, we have found that many customers have added software and hardware to their environments over time that is left with default settings enabled and/or improperly configured. In doing so, these environments become prime targets for nefarious cyber threat actors that can string together weaknesses and vulnerabilities to achieve critical impacts.
The Exploitation of Critical CISA Known Exploited Vulnerabilities (KEV)
Since its founding in 2018, CISA – and its predecessor organization, the National Protection and Programs Directorate before that – has informed the public of a variety of cybersecurity threats and vulnerabilities, as well as mitigation and fix actions. Our engineers and researchers, in addition to conducting their own vulnerability research and finding exploits on their own, use the information provided by CISA to prioritize NodeZero’s attack content. We also use this information in conjunction with our own open-source research to determine what vulnerabilities are actively being exploited by threat actors and what vulnerabilities may impact our customers.
Over the last year, we have notified our customers of multiple vulnerabilities that can impact their environments and are exploited by NodeZero in pentests. Probably too many to list here. However, we will highlight three of the most predominant vulnerabilities that we see our customers experience when running pentests.

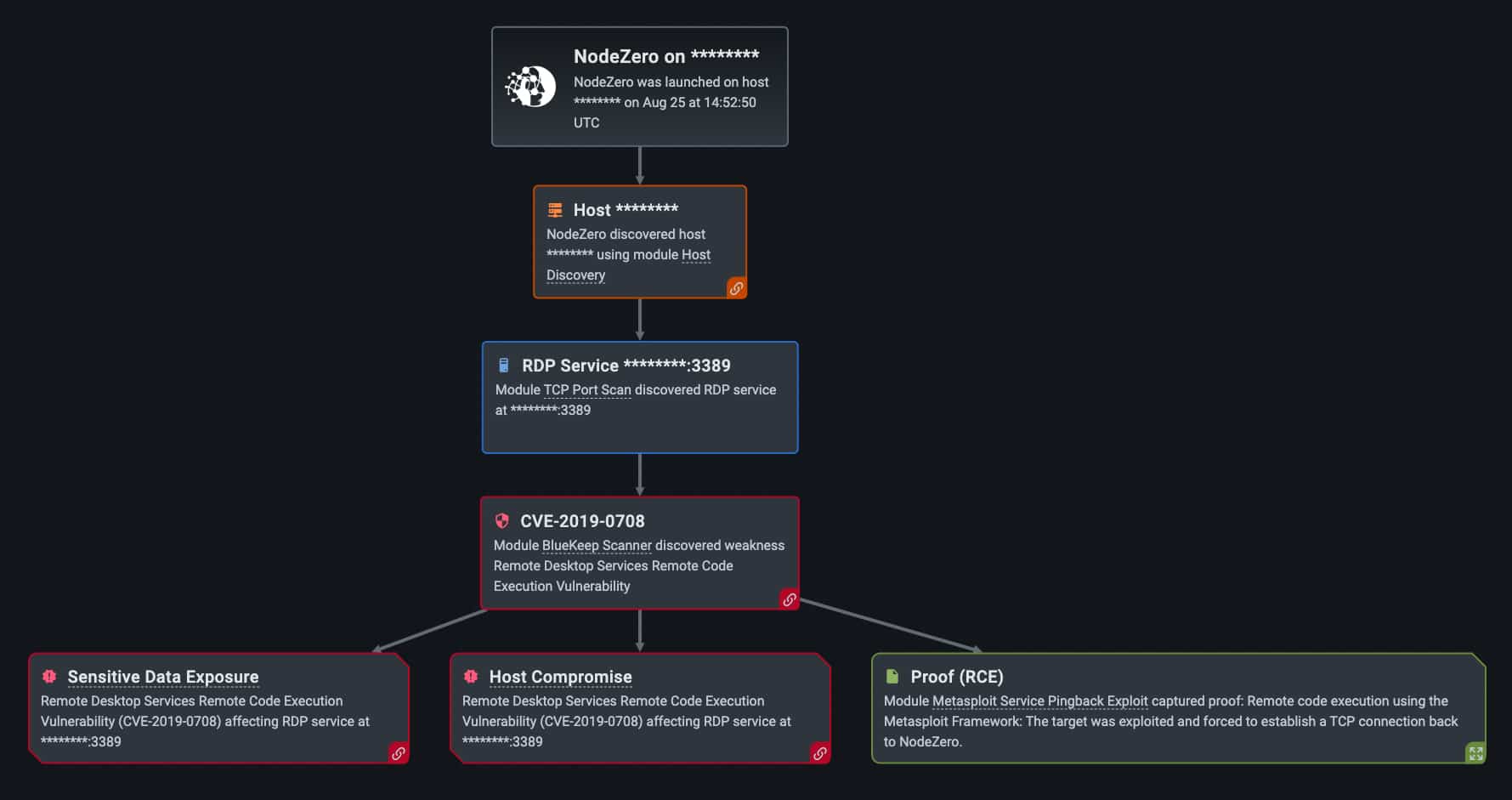
For example, our NodeZero exploited the Remote Desktop Services RCE Vulnerability (CVE-2019-0708), otherwise known as “BlueKeep,” over 550 times this past year (out of the 34,000 times in which NodeZero successfully executed an attack compromising at least one host). This vulnerability specifically affects older operating systems like Windows 7, Windows Server 2003, Windows Server 2008, Windows Server 2008 R2, Windows Vista, and Windows XP. The vulnerability is also significant because it targets the Windows Remote Desktop Protocol that provides a graphical user interface to connect to various computers using a network connection. Further, the vulnerability is potentially “wormable.” This means that it could be exploited and spread from one computer to another.

The Windows SMB Remote Code Execution Vulnerability (EternalBlue, CVE-2017-0144) was exploited over 500 times by NodeZero in customer environments this past year (out of the 34,000 times in which NodeZero successfully executed an attack compromising at least one host). Here, a vulnerability exists when the Microsoft Server Message Block 1.0 (SMBv1) server handles certain requests. An attacker can exploit the vulnerability by sending a specially crafted packet to the SMBv1 server. This would then give the attacker the ability to execute code on that targeted SMBv1 server. As we saw in the previous example with a major company sports and entertainment industry in Figure 2, this vulnerability was used on two different machines to ultimately achieve Ransomware Exposure.

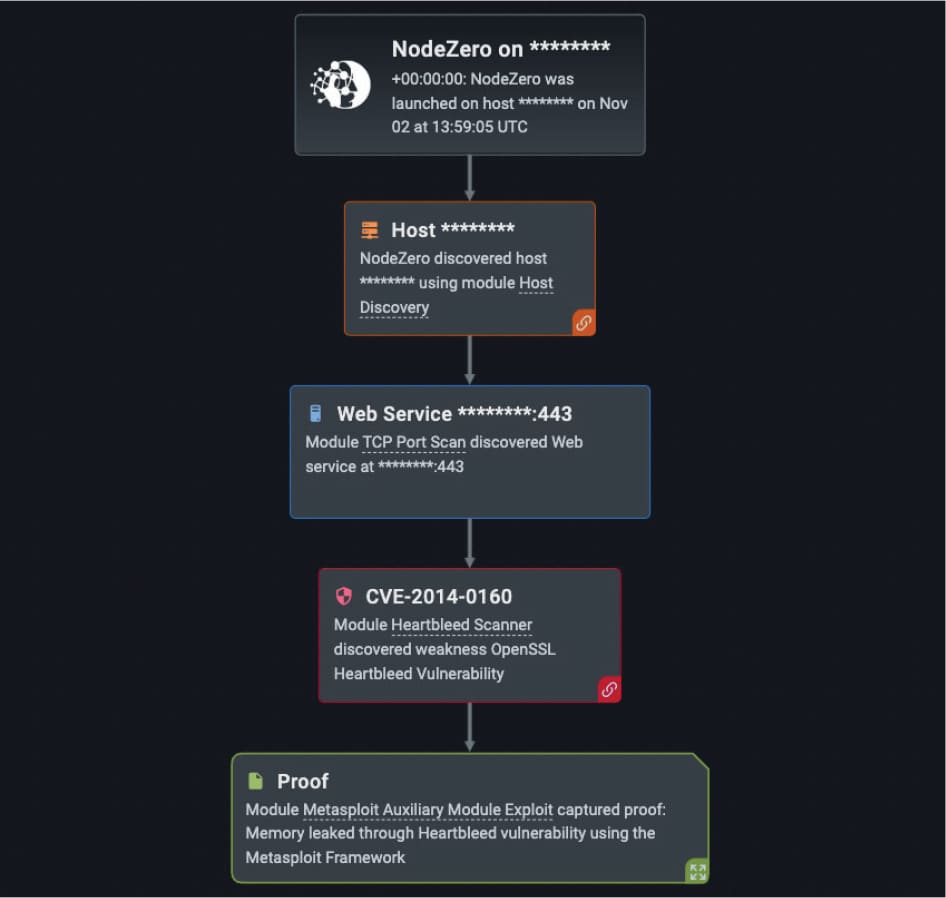
Our customers over the last year also experienced the OpenSSL Heartbleed Vulnerability (CVE-2014-0160) nearly 200 times in their NodeZero pentests (out of the 34,000 times in which NodeZero successfully executed an attack compromising at least one host). This vulnerability allows for the stealing of protected information by the SSL/TLS encryption used to secure the internet. SSL/TLS provides communication security and privacy over the internet for applications such as web, email, internet messaging and virtual private networks. The vulnerability allows anyone on the internet to read the memory of the systems used by unpatched versions of OpenSSL software. This not only compromises the secret keys used to identify service providers and to encrypt traffic, the user credentials, and the actual content, but it allows attackers to eavesdrop on communications, steal data and impersonate services or users. The affected versions of OpenSSL are 1.0.1 through 1.0.11.
Threat Intelligence Reference
As one can see, many of our customers find that they are susceptible to these dated vulnerabilities, even though we know that they have been actively exploited in the wild. In the case of Bluekeep, security researchers found evidence of a global campaign in 2018 that involved cyber threat actors scanning the internet and spraying exploits. While BlueKeep has been a major annoyance to the cybersecurity community at large so far, it is important to keep in mind that a similar worm used in 2017 caused more than $10 billion in damage worldwide.
We saw further damage with the use of EternalBlue in the WannaCry ransomware attack, when more than 200,000 devices across 150 countries were encrypted within just 24 hours back in 2017. After the files were encrypted, a ransom note appeared on the devices demanding $300-600 to paid. Several organizations were targeted, including hospitals, and cost ~$4 billion in damages. Further, many cyber threat actors remain poised to use EternalBlue or similar tactics and techniques to garner ransom payments. And, finally, we know that the OpenSSL Heartbleed vulnerability affected nearly two-thirds of the internet’s servers dependent on SSL encryption and millions of devices, including Android phones. While it remains unclear as to which cyberattacks can be blamed on Heartbleed, both websites Yahoo and OKCupid users were advised to not log into their accounts for a short period of time until the services were able to patch their installs of OpenSSL. Further, an attack on Community Health Systems, where patient data was stolen was blamed on the vulnerability, as was an attack on the Canadian Revenue Agency that resulted in the theft of social identification numbers.
Exploitation of Critical VMware Vulnerabilities
In addition to the number of critical vulnerabilities like BlueKeep, EternalBlue and Open SSL Heartbleed that CISA alerts us to, we continue to see critical and exploitable vulnerabilities in various VMware products.

Horizon3.ai customers found their VMware products reachable, vulnerable, and exploitable over 350 times (out of the 34,000 times in which NodeZero successfully executed an attack compromising at least one host). By using VMware platforms, organizations can run multiple hosts, applications, and operating systems on one single server – thereby enhancing resource management and efficiency. Virtual machines behave exactly as separate computers but run simultaneously on the physical machine on which they are installed. Further, a user can run a variety of operating systems on their existing machine. A user can run Linux on a Windows machine, or MacOS on a Linux machine for example.

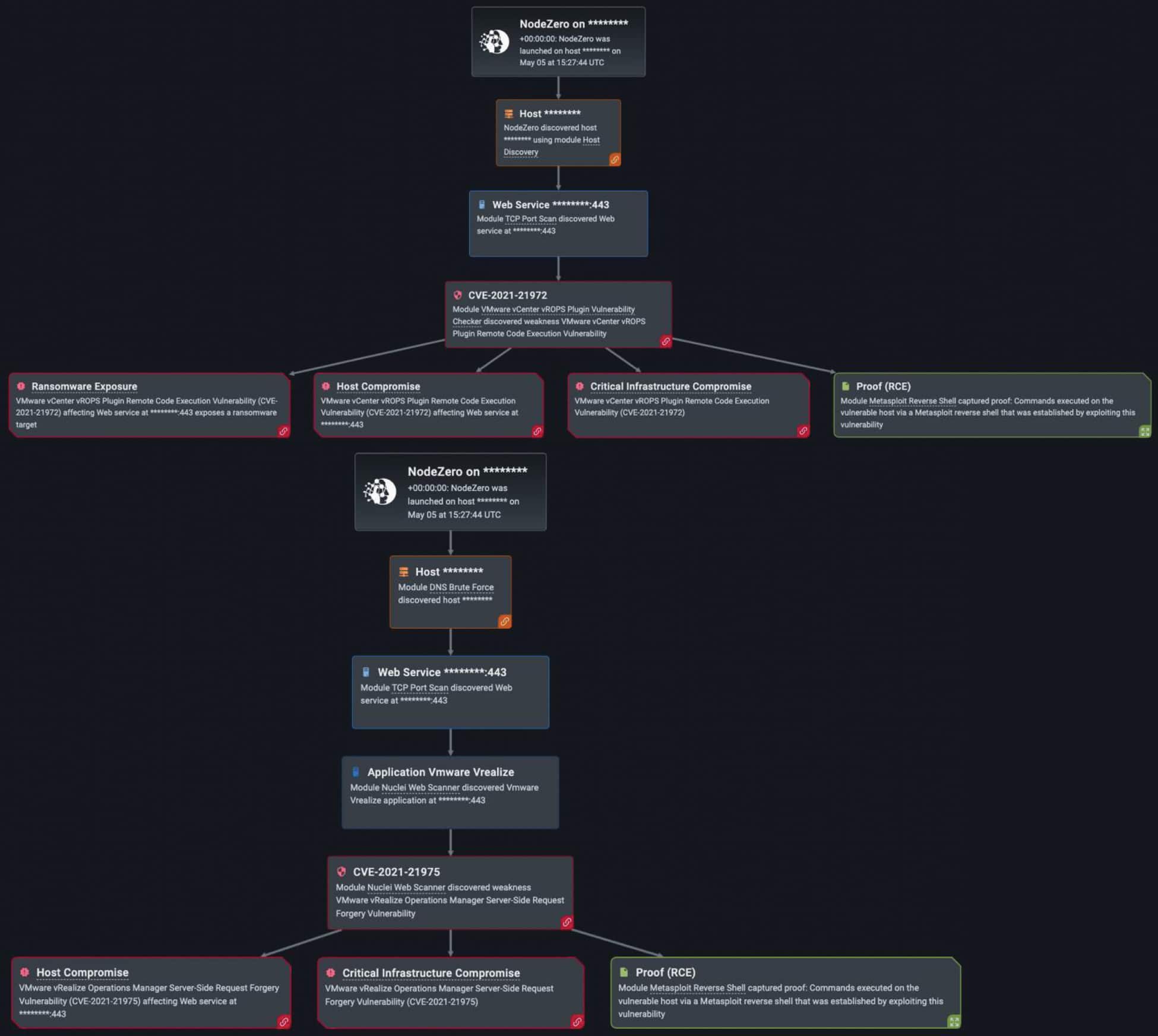
- VMware vulnerabilities are vast and dangerous when exploited. Horizon3.ai has developed exploits for CVE-2022-22972, an authentication bypass affecting local domain users. According to VMware, an adversary “with network access is able to obtain administrative access to the UI without authenticating their identity,” impacting VMware Workspace ONE Access, Identity Manager and vRealize Automation, and VMware identity manager, among other products. The suggested mitigation is to apply the KB88438 patch, as well as looking into strengthening your organization’s authentication policy. This could include encrypting user session IDs and cookies, enforce a high password length, and validating user input on the server-side, if not done already.
- Another highly critical vulnerability is local privilege escalation (CVE-2022-22973), in which an adversary with local access can escalate their privileges to “root” . The consequences of a successful privilege escalation attack may end up with the attacker modifying, stealing, or deleting essential data. The recommended patch prescribed by VMware for this vulnerability is KB88438, but other steps may be taken to prevent privilege escalation attacks. This includes regularly performing scans of all IT infrastructure (network, applications, operating system, etc.), minimizing the number of privileged accounts, and monitoring and reporting suspicious user behavior.
- As with numerous applications, RCE vulnerabilities are equally persistent in VMware (CVE-2022-22954). RCE affects VMware workspace ONE and Identity Manager with a server-side injection, in which an attacker with network access can execute arbitrary shell commands as a VMware user. A server-side template injection (user-input embedded into a server-side template) is a possible avenue for conducting RCE attacks. To prevent RCE attacks, it is important to immediately patch Workspace ONE and Identity Manager installations and ensure you are employing input sanitization tactics to avoid code injections.
Threat Intelligence Reference
To make matters worse, we know that cyber threat actors are continuing to exploit vulnerabilities within VMware products even with patches available like in the case of the aforementioned VMware Workspace ONE Access. Researchers with Fortinet FortiGuard Labs have observed attacks in the wild targeting sensitive data with the intent to use the victim’s resources to install ransomware for extortion and to collect cryptocurrency. To combat this, users should keep their systems patched and be aware of and stop suspicious processes occurring in their environment.
Misconfigurations And Vulnerabilities in DevOps Tools (Jenkins, GitLab, Kubernetes, and Docker)
Horizon3.ai customers often use DevOps tools like Jenkins, GitLab, Kubernetes, and Docker that are critical to their business for the deployment, configuration and automation of software development and design. These tools also run the risk of compromise by cyber threat actors due to misconfigurations and known vulnerabilities. NodeZero is also adept at exploiting misconfigurations in those same DevOps tools in pentests.

Take, for instance, Jenkins, the open-source automation software that focuses on the deployment and delivery of applications, working to implement CI/CD workflow analysis. Jenkins is useful for testing and building software projects with continuous integration and allowing for changes to be made during any stage of the development process, while also sharing the changes in a community repository. However, NodeZero has discovered over 100 instances of exploitable Jenkins configurations targeted in internal pentests (out of the 34,000 times in which NodeZero successfully executed an attack compromising at least one host).
One of the most frequent vulnerabilities discovered in the product includes XSS (cross-site scripting). Cross-site scripting is an attack that allows an adversary to modify web applications by injecting malicious code into web pages viewed by users. The location of code injections could include the contacts form or search bar of a website. When a “search” or “submit” request is sent by a user, a malicious query is forwarded to the web application’s server. Other types of XSS attacks also include storing a malicious payload on the server to compromise the website, going after vulnerable Javascript code, or taking advantage of blind cross-site scripting (a successful payload overseen by the administrator).
There are several ways to mitigate XSS vulnerabilities, including the use of post-hack methods and preventive procedures. Before an XSS attack occurs, it is always beneficial to limit user input to a strict Allowlist, restrict HTML inputs on web applications, employ HTTPOnly flags on cookies, and establish a WAF (Web Application Firewall) to filter through malicious traffic. After an XSS attack, it is important to immediately discover where the vulnerability exists, remove the bad data from the database, and apply the appropriate patch.

GitLab is another DevOps software package that provides a collaborative platform for housing open-source code in community repositories, but like Jenkins, NodeZero also discovered almost 50 instances of Gitlab in Customer pentests (out of the 34,000 times in which NodeZero successfully executed an attack compromising at least one host). The most important instances include remote command execution vulnerabilities (CVE-2022-2185), XSS, unauthorized viewing of private variables (CVE-2022-2229) and exposing 2FA to unauthenticated users (CVE-2022-1963). GitLab has released the appropriate patches to fix these vulnerabilities, but more work is required to ensure advanced security for the teamwork-enhancing tool. According to GitLab’s critical security release report, it is highly recommended to update all versions to 15.1.1, 15.0.4, and 14.0.5 . To specifically avoid remote command execution attacks via project imports, it is always important to keep third-party software up to date and use buffer overflow protection in organizational software.

One of the more popular DevOps tools pentested by customers using NodeZero, Docker had a total of 50 instances discovered (out of the 34,000 times in which NodeZero successfully executed an attack compromising at least one host). Docker is a cloud computing tool used to automate the application deployment and management of cloud containers. While apps are being moved to different platforms on the cloud, Docker allows them to still operate for continuous organizational functions. The top docker vulnerabilities for 2022 included bugs in desktop versions 4.3.0 and 4.3.1 and the “dirty pipe” Linux vulnerability (CVE-2022-0847) . The “dirty pipe” is a highly critical vulnerability that overwrites read-only files in the Linux kernel host, allowing adversaries to modify the files from the container instance. If an organization is using the Docker engine for this service, it is important to ensure that the Linux OS version is updated to 5.10.102 or later.

The final DevOps tool reviewed was Kubernetes, in which NodeZero discovered over 50 instances of product vulnerabilities in the Horizon3.ai pentests (out of the 34,000 times in which NodeZero successfully executed an attack compromising at least one host). Kubernetes is an open-source container orientation system that automates the processes of launching, maintaining, and scaling applications. It focuses on expanding the scale of operations for an organization’s application ability and clustering multiple hosts (VMs) together on the cloud. Kubernetes is important for load balancing and running production software, but it houses the highly critical ingress-nginx vulnerability (CVE-2021-25742) . Ingress-nginx is a daemon (computer program running as a background process) that is important for configuring HTTP load balances for services running in the Kubernetes environment.
Due to a few misconfigurations, the ingress-nginx controller has allowed attackers to obtain important credentials and expose cluster secrets. To test whether this vulnerability exists in a Kubernetes cluster, it is important to first run a Kubescape scan. If the vulnerability is discovered, mitigations should include updating to Kubernetes versions v1.0.1 or v0.49.1 and upgrading ingress-nginx. In addition, it is helpful to prevent all nginx-ingress annotation snippets containing Lua code execution or alias statements.
Threat Intelligence Reference
We know that groups like Lapsus$ are actively seeking to breach major corporations and developers to obtain source code from code repositories like GitLab and Github. Earlier this year, Microsoft revealed that the Lapsus$ group posted a torrent file containing the source code for Bing, Bing Maps, and Cortana, which they obtained from by compromising a single employee’s account. While this is only one of many attacks by groups seeking to target development and collaboration platforms, it shows that they have the capability to exfiltrate sensitive product data as well as create changes or destroy that data, thereby causing great financial harm to the targeted company.
Misconfigurations and Vulnerabilities in Routers, iLOs, iDRACs
As of this year, misconfigurations and vulnerabilities in routers offered one of the greatest boons for adversaries in their tirade against big organizations. A router is a device that connects subnets to one another, generally allowing for a network to connect to the greater Internet. According to a report conducted by Kaspersky, many critical vulnerabilities discovered across various routers in 2021 remain unpatched in the year 2022.
Many of the leaders in hardware development like Huawei, Cisco, Arris International, and Netgear have experienced heavy compromises on their devices. The main attacks include adversaries employing arbitrary remote code execution (RCE) to misconfigure routers, taking advantage of unpatched router software, poisoning routing tables, performing SYN floods (denial of service), exploiting outdated Linux kernel in the firmware, and of course, weak user passwords. It is recommended by security professionals that organizations pay closer attention to the security of their hardware infrastructure, starting particularly with routers. A router can easily become more secure by resetting the factory default password, regularly performing patches, and upgrading firmware to the most recent versions, and employing an IDS or IPS to monitor router activity.
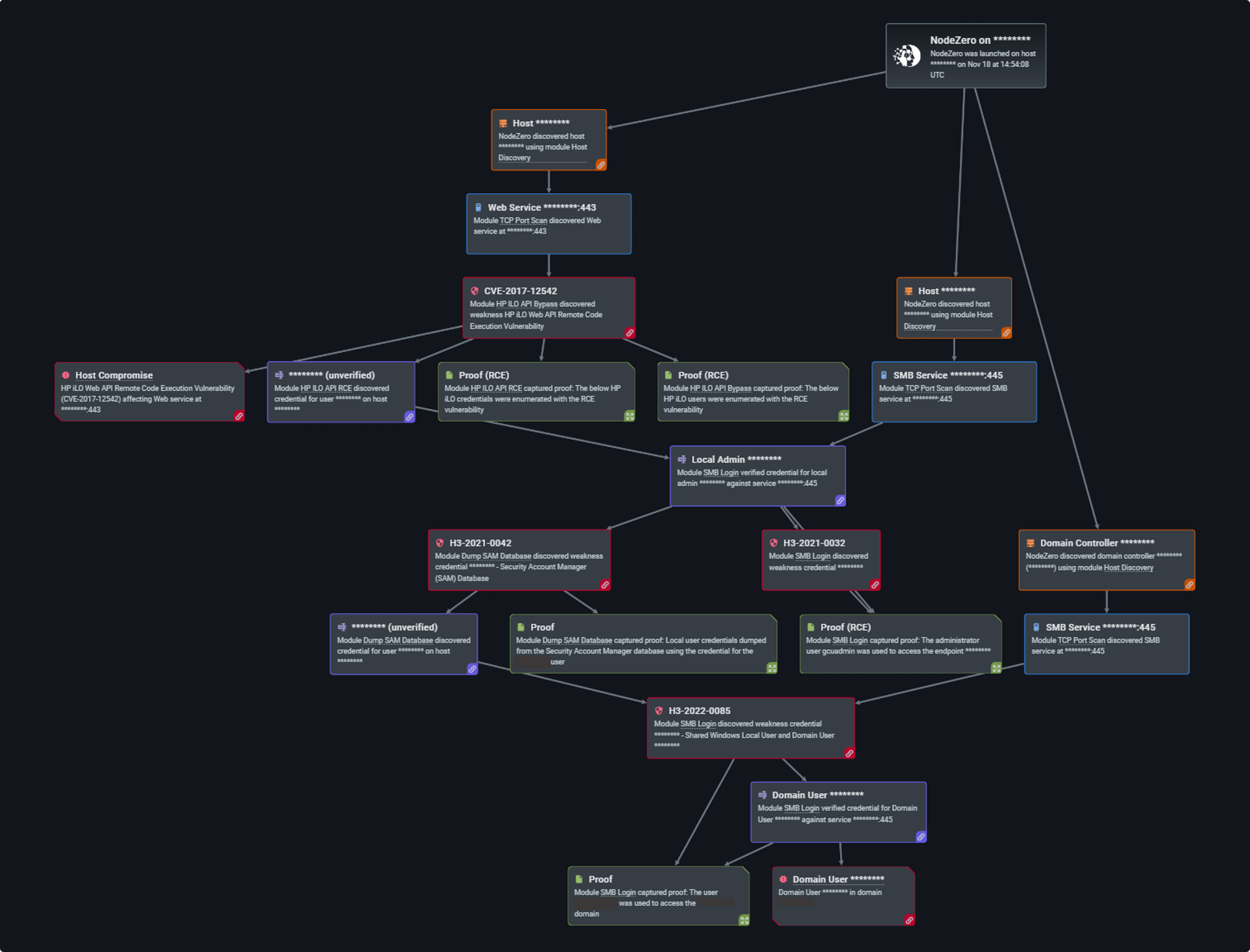
Along with the increase in router vulnerabilities and misconfigurations, there has also been a sharp rise in threats to iLOs (Integrated Lights Out) and iDRACS (Integrated Dell Remote Access). Integrated Lights Out is a remote server management processor card that is embedded on the system boards of servers, particularly HP Proliant and Blade. The iLO system helps update, configure, and run HP servers while monitoring them remotely. Each iLO card has its own IP address and network connection which server admins access via DNS (the Domain Name System) and the DHCP protocol (Dynamic Host Configuration Protocol).
Using iLO allows admins to power the server on and off, restart the server, measure power usage, apply patches, and access event logs of the system. As of 2021, attackers were able to gain control over HP iLO 4 servers and view user passwords in cleartext by exploiting a vulnerability in the device’s firmware (CVE-2017-12542).
An Integrated Dell Remote Access (iDRAC) is an out-of-band management card embedded into the system board platform of a Dell server. Like an iLO, an iDRAC is used for remote server management, such as controlling, configuring, and running Dell servers. A server administrator employs iDRAC to deploy servers, alert system issues, perform server patches and updates, and monitor the server on a continual basis. However, just like iLOs, iDRACS have suffered from severe vulnerabilities in the past year, most famously being improper input validation. Improper input validation involves an attacker sending a malicious web request to the server for the main goal of corrupting its responsiveness. In addition to this vulnerability, iDRAC versions 4.40 and earlier are especially submissive to SQL injection and buffer overflow attacks. The most recommended mitigation to counter these prevalent threats is updating to a more secure iDRAC server version (at least 5.00 or higher).
Threat Intelligence Reference
One good example of hardware being targeted by probable APT actors is when Hewlett Packard Enterprise’s iLO servers were compromised by the iLOBleed rootkit earlier this year. The attackers targeted HP server employees operating in several industries, including financial firms, hospital and healthcare, telecommunications, and more. According to researchers, the iLOBleed has been observed in the wild since at least 2020 and has provided attackers with full control over a compromised server and has allowed them to completely wipe the victim’s server’s disks. Furthermore, the attackers can do this repeatedly even after the server operating system is reinstalled because iLOBleed is implanted in the BMC firmware. With the iLOBleed rootkit deployed, attackers can also take full control over HP machines while silently preventing firmware updates and avoiding suspicion.
Implications of Failures to Patch and Misconfigurations
When NodeZero exploits these vulnerabilities and misconfigurations as a threat actor would, especially when they are strung together to reach critical impacts, it tells us a few things about the organization and its environment.
- It could imply that companies and organizations are having trouble implementing patching policies that keep their systems up-to-date and that previous vulnerabilities remain mitigated. Some of the vulnerabilities we briefly discussed are over five years old, have been found on multiple machines, and have published vendor fixes and/or mitigation actions. All they need to do is “simply” apply the patches or the mitigation actions and confirm that they are fixed.
- It may also imply that the customer is having difficulty prioritizing what needs to be fixed. The organization’s IT department might be spending time patching and fixing vulnerabilities that may not actually be exploitable within their environment or have a lower criticality than those that will lead to critical impacts like host compromise, domain compromise, or ransomware exposure. Meaning, they aren’t prioritizing and fixing what actually matters.
- It could also mean that an organization may have legacy systems that are not able to be patched to the latest version, because of certain incompatibility issues with other technologies on the network. In those cases, the systems that cannot be upgraded or patched need to be segmented from the rest of the environment. This will limit any impact that a threat actor would have if it were able to exploit the vulnerability on that specific machine.
- It tells us that IT departments may have issues configuring new hardware like routers when adding them to the network. Too often we find that customers find that new hardware was added to their network with default settings and passwords that are made available on the open web, making it easily exploitable for any nefarious actor who would come across it.
Policy Recommendations and Mitigation Actions
When it comes to preventing cyber threat actors from taking advantage of known vulnerabilities and weaknesses, Horizon3.ai recommends instituting patching and mitigation policies to keep your systems as up to date as possible. We understand that not every technology can be patched, because of the potential to interfere with other technologies in the environment. In those instances, we suggest that you use vendor-approved fix action and mitigation strategies to prevent the vulnerability from being exploitable in your environment. If those fix action or mitigation strategies are still not available to you, we recommend segmenting that machine from the rest of your environment to prevent a malicious actor from reaching other portions of your environment and achieving critical impacts.