Resource Center
Welcome to our cybersecurity resource center where we uncover how malicious actors exploit weaknesses in systems, while going beyond the technical aspects and examining real-world perspectives across various industries.
LATEST VULNERABILITIES
Gladinet Triofox Improper Access Control Vulnerability | Active Exploitation
Read More →WEBINAR REPLAY
SEARCH
CATEGORIES
TAGS
SEARCH
CATEGORIES
TAGS
The State of Cybersecurity in 2025: Data-Driven Insights from Over 50,000 NodeZero® Pentests
March 26, 2025
Insights from 50K+ NodeZero®️ pentests reveal why offensive security is key in 2025. Learn how to move beyond compliance and close critical gaps.
Critical or Clickbait: GitHub Actions and Apache Tomcat RCE Vulnerabilities 2025
March 21, 2025
Explore CVE-2025-30066 and CVE-2025-24813 with real-world data from Horizon3.ai to assess whether these vulnerabilities are truly critical or overhyped.
Fireside Chat: Horizon3.ai and Adaptic LLC
DoD supply chain cyber threats are surging. Learn how CAPT helps suppliers find, fix & verify gaps with scalable, autonomous security testing.
Is Continuous Threat Exposure Management right for you?
March 12, 2025
The CTEM framework has the right goals. NodeZero takes the bloat out of achieving them.
Traditional vs. Autonomous: Why NodeZero® is the Future of Cyber Risk Assessments
March 11, 2025
Learn how NodeZero® overcomes the limitations of traditional pentesting with continuous, real-time, autonomous security assessments for modern threats.
Why Every New CISO Should Run NodeZero® on Day One
March 10, 2025
New CISOs face immediate cyber risks. Run NodeZero on day one for real-time insights, validated threats, and a proactive security strategy.
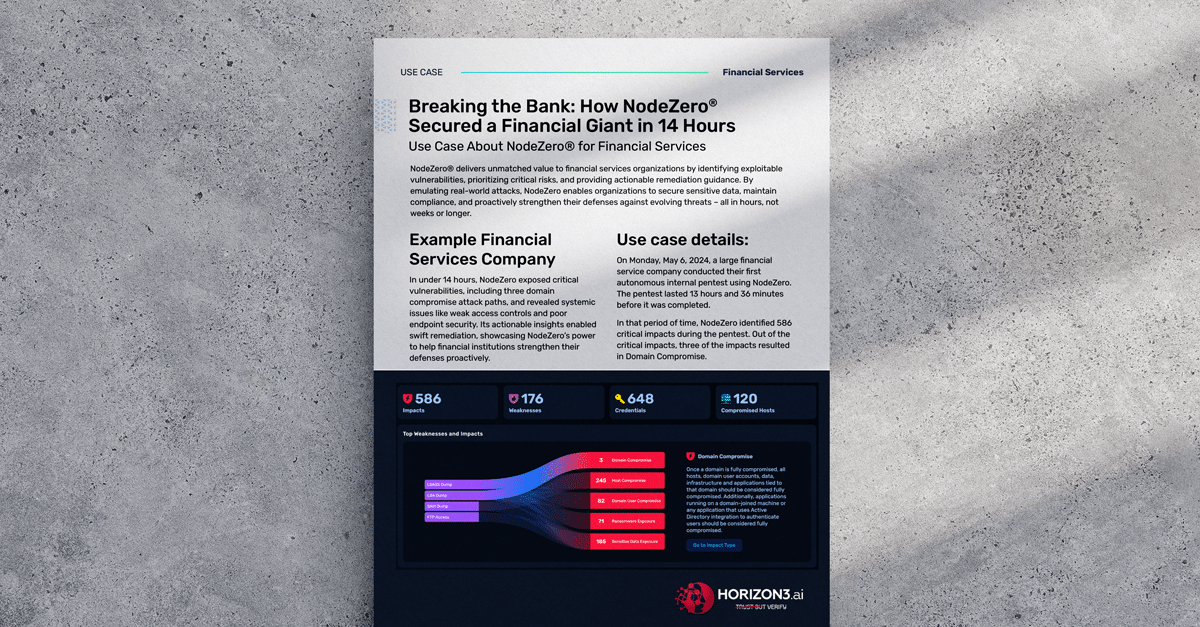
Breaking the Bank: How NodeZero® Secured a Financial Giant in Just 14 Hours
March 6, 2025
Financial firms faced 141 breaches in Q3 2024. See how NodeZero exposed critical gaps in 14 hours—before attackers could exploit them.
Identify Cybersecurity Risks at Scale to De-Risk M&A Transactions with Horizon3.ai’s NodeZero® Platform
March 5, 2025
Cybersecurity solutions to secure your mergers and acquisitions. Identify hidden risks and ensure seamless security integration for every deal.
Ivanti Endpoint Manager – Multiple Credential Coercion Vulnerabilities
February 19, 2025
Critical Ivanti Endpoint Manager vulnerabilities revealed—learn about CVE exploits and mitigation.
Fireside Chat: Horizon3.ai and Jerome’s Furniture
Discover how Jerome's Furniture revolutionized cybersecurity with NodeZero. Real-world insights on proactive, efficient defense.