Resource Center
Welcome to our cybersecurity resource center where we uncover how malicious actors exploit weaknesses in systems, while going beyond the technical aspects and examining real-world perspectives across various industries.
Subscribe to AlertsCategory:
Tags:

June 5, 2023 | Blogs
Gartner® recently published a report called, Emerging Tech: Grow Your Security Service Revenue with Cybersecurity Validations. We believe the report…
May 31, 2023 | Blogs
In early 2023, CISA launched their Ransomware Vulnerability Awareness Pilot (RVWP). It’s designed to warn critical infrastructure (CI) entities that…
May 16, 2023 | Webinar Replays
Hear directly from Zach Hanley, one of Horizon3.ai's founding engineers as he walks you through a recent critical vulnerability case…
May 16, 2023 | Webinar Replays
Hear directly from two of Horizon3.ai's founding engineers - Naveen Sunkavally, Chief Architect, and Rob Alderman, Data Architect - as…April 25, 2023 | Attack Blogs, Disclosures
Apache Superset is an open source data visualization and exploration tool. It has over 50K stars on GitHub, and there…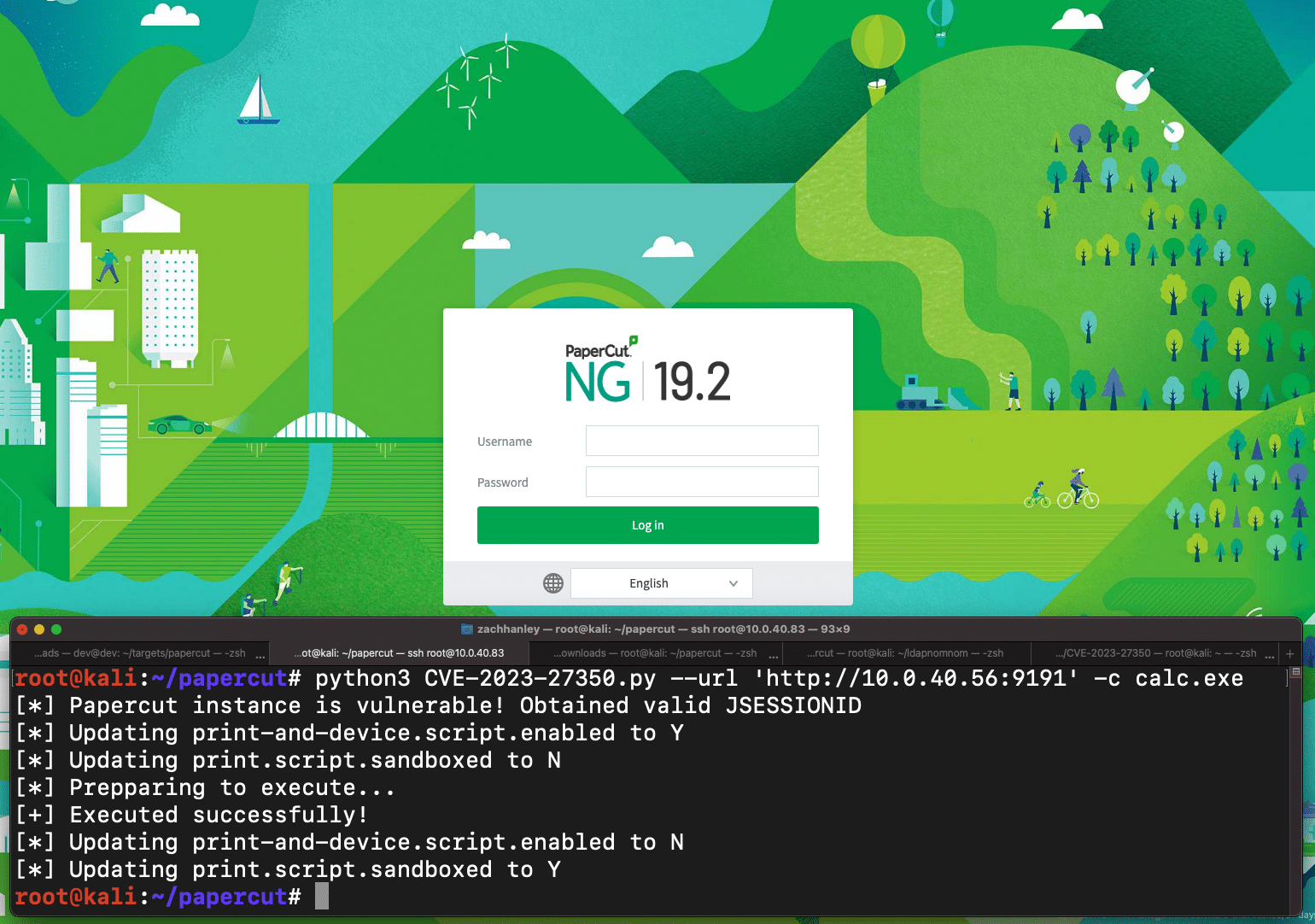
April 24, 2023 | Attack Blogs
Overview On 8 March 2023, PaperCut released new versions for their enterprise print management software, which included patches for two…
April 11, 2023 | Customer Stories
One of our customers, a public university in Victoria, British Columbia, is constantly looking for ways to improve their overall…
March 23, 2023 | Attack Blogs
Introduction Veeam has recently released an advisory for CVE-2023-27532 for Veeam Backup and Replication which allows an unauthenticated user with…
March 15, 2023 | Blogs
On 10 March, Silicon Valley Bank (SVB) – a popular institution for the venture capital community in the Bay area…
March 8, 2023 | Podcasts
"Trust but verify" is a well-known proverb, but in today's cybersecurity world, we recommend just verifying. That concept is the…
