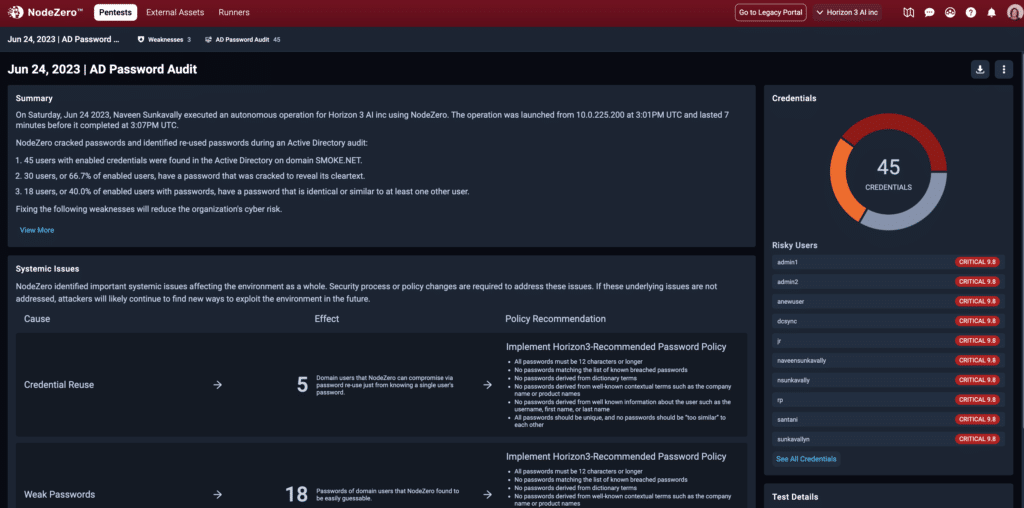
Audit Your Password Exposure
with NodeZero®
Attackers don’t hack in, they log in.
- Reveals user passwords in your Active Directory (AD) environment that are likely targets for credential stuffing, password spray, credential reuse, and password cracking attacks.
- Cracks passwords based on public breach data, open source intelligence (OSINT) tied to your company, and any weak password terms that you can provide.
- Provides a prioritized list of risky accounts along with detailed remediation guidance.
- Enables you to regularly audit passwords as employees join or leave your organization.
CISA testing estimates that valid accounts can be successfully used to gain network access 54% of the time.
Why are password audits important?
Cyber threat actors commonly use valid accounts for initial access, lateral movement, and privilege escalation. The CISA Analysis: Fiscal Year 2022 Risk and Vulnerability Assessments finds valid accounts can be used to:
Gain initial access 54.3% of the time.
Maintain persistence 56.1% of the time.
Escalate privileges 42.9% of the time.
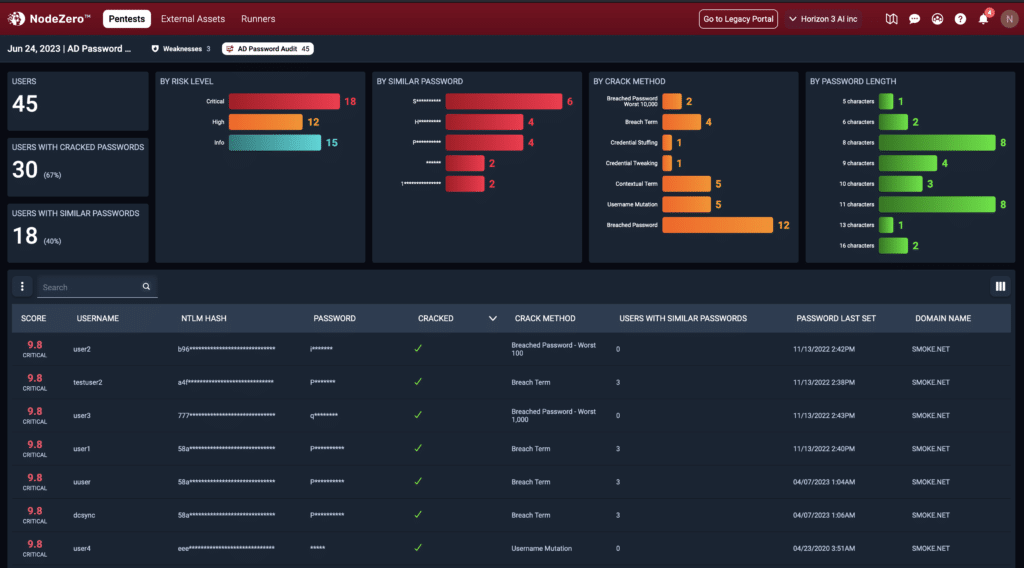
Blast Radius Impact
Remediation
A Fix Action Report is delivered with the results of your AD Password Audit operation. NodeZero provides:
Risky accounts that require immediate attention in a prioritized list
Guidance on how to improve your password policy in accordance with National Institute of Standards and Technology (NIST) standards
Output you can feed into other tools, like Splunk, to investigate attacker use of risky accounts in the past
It’s Easy to Get Started
When setting up your AD Password Audit, you are asked to enter a single IP address, add a credential, and basic information about your company such as its name and domain name. With that information, NodeZero uses OSINT to add more context about your company — context that an attacker may be able to leverage to guess weak passwords.
NodeZero uses your company domains to look up dark web data associated with your company. If you have any well-known weak passwords at your company that you want to weed out, you can add them into the “Weak Password Terms” section and NodeZero will attempt to use them (and variations of them) while cracking.
Evaluate your credential exposure today with your NodeZero free trial
See a Demo

