Introduction
The recent ManageEngine CVE-2022-47966 is a pre-authentication remote code execution vulnerability. Depending on the specific ManageEngine product, this vulnerability is exploitable if SAML single-sign-on is enabled or has ever been enabled. ManageEngine products are some of the most widely used across enterprises and perform business functions such as authentication, authorization, and identity management. Given the nature of these products, a vulnerability such as this poses critical risk to organizations allowing attackers initial access, if exposed to the internet, and the ability for lateral movement with highly privileged credentials.
We have successfully reproduced this exploit and would like to provide additional insight into the vulnerability so users can begin to determine if they have been compromised. In this post we discuss logs entries present in:
- ManageEngine ServiceDesk Plus 14003
- ManageEngine Endpoint Central 10.1.2228.10
These Indicators of Compromise (IOCs) will likely be present on other vulnerable products and we will update this post as we confirm their presence or absence. Additionally, we will be releasing a technical deep dive describing the inner workings of this vulnerability.
IOCs for ServiceDesk Plus, Endpoint Central, and Other ManageEngine Products
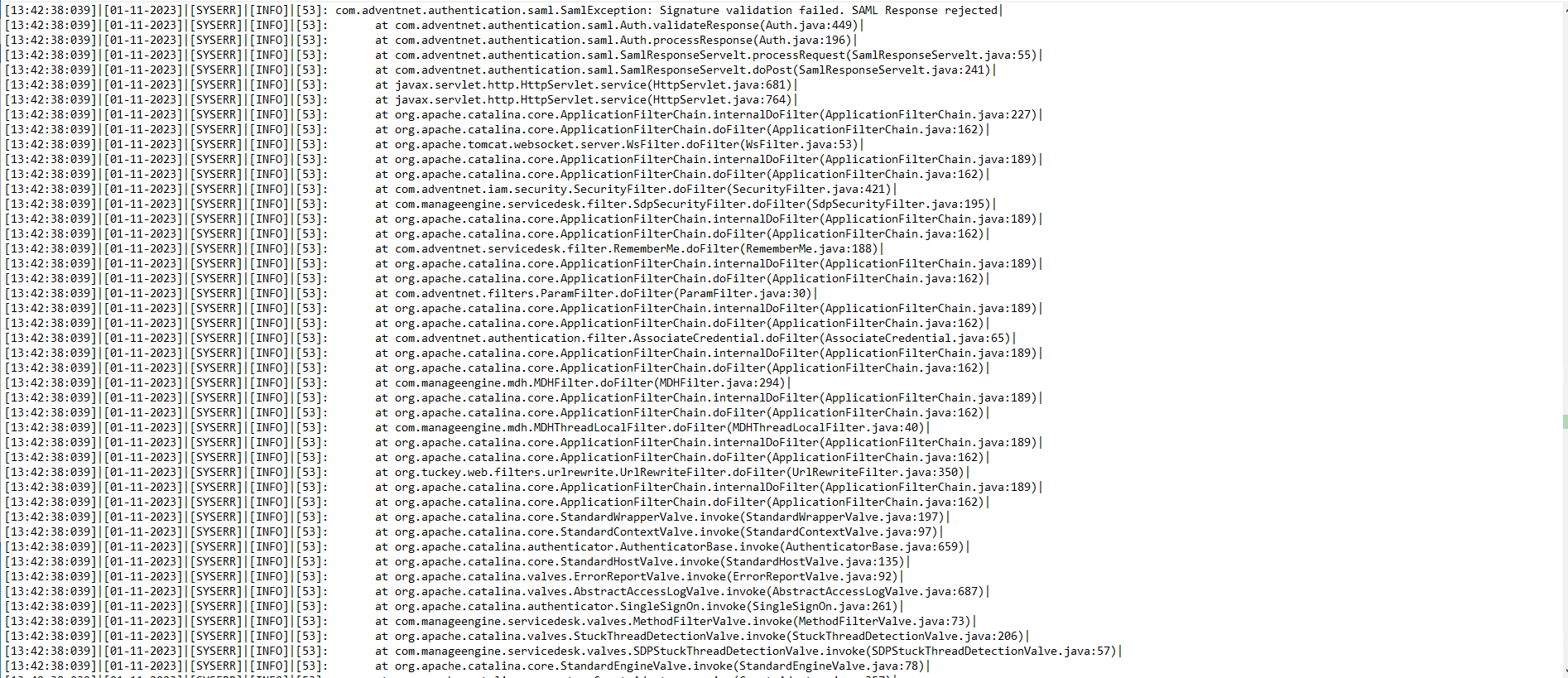
Log files in ManageEngine products can normally be found a logs folder in the product’s installation directory. For example, C:\Program Files\ManageEngine\ServiceDesk\logs. The log files typically have a name like serverout<N> files where N is some number. For example serverout0, serverout1, etc. The exact name and locations of the log files can vary between products. To search for evidence of compromise, search for a stack trace like the following:
[09:37:00:053]|[01-12-2023]|[SYSERR]|[INFO]|[59]: com.adventnet.authentication.saml.SamlException: Signature validation failed. SAML Response rejected|
In order for an attacker to execute this RCE, they will need to craft a SAML request with an invalid signature hence the exception. A screenshot with the extended stack trace can be seen below:
Attacker Mindset
The vulnerability is easy to exploit and a good candidate for attackers to “spray and pray” across the Internet. This vulnerability allows for remote code execution as NT AUTHORITY\SYSTEM, essentially giving an attacker complete control over the system. If a user determines they have been compromised, additional investigation is required to determine any damage an attacker has done.
Once an attacker has SYSTEM level access to the endpoint, attackers are likely to begin dumping credentials via LSASS or leverage existing public tooling to access stored application credentials to conduct lateral movement.
Shodan data shows that there are likely more than a thousand instances of ManageEngine products exposed to the internet with SAML currently enabled. Looking just at the ServiceDesk Plus and Endpoint Central products, we found:
- 5255 exposed instances of ServiceDesk Plus, of which 509 have SAML enabled
- 3105 exposed instances of Endpoint Central, of which 345 have SAML enabled
From this we presume that roughly 10% of all ManageEngine products exposed to the Internet have SAML enabled. Organizations that use SAML in the first place tend to be larger and more mature and are likely to be higher value targets for attackers. In fact, ManageEngine products have been highly targeted in the past several years by threat actors to gain initial access:
- CISA / FBI Flash Alert for ManageEngine Desktop Central CVE-2021-44515
- CISA / FBI Alert for ManageEngine ServiceDesk Plus CVE-2021-44055
- CISA Adds ManageEngine Password Manager Pro CVE-2022-35405 to its Known Exploited Vulnerabilities Catalog
Patch Now
ManageEngine released patches for all affected products by the end of October 2022. We expect some ManageEngine clients to have already patched, but given how slow enterprise patch cycles can be, we expect that there are many who have not yet patched.
We encourage all ManageEngine users to heed the ManageEngine advisory and patch immediately. We want to highlight that in some cases the vulnerability is exploitable even if SAML is not currently enabled, but was enabled sometime in the past. The safest course of action is to patch regardless of the SAML configuration of the product.

