As Horizon3.ai wraps up the year with our highly anticipated Horizon3.ai Year in Review (2021-2022): Through the Eyes of the Attacker coming soon, we want to ensure our customers are continuing to think through:
- What does my environment look like?
- Are my security tools effective?
- Did we detect the right activity?
- Are we logging the right things?
- Are my crown jewels and keys to the kingdom– sensitive data and privileged credentials– reachable and exploitable?
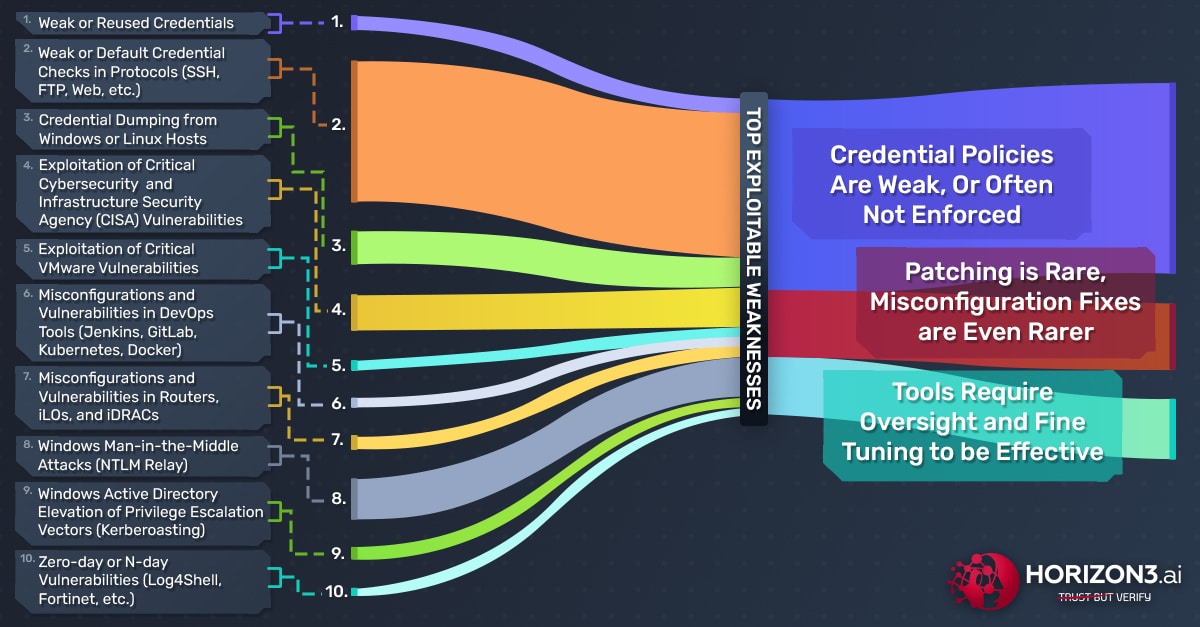
Over the past year, Horizon3.ai pentests revealed cybersecurity vulnerability trends across multiple industry sectors around the globe. Specifically, the top 3 systematic issues NodeZero surfaced are:
- Credential Policies Are Weak, Or Often Not Enforced
- Patching Is Rare, Misconfiguration Fixes Are Even Rarer
- Security Tools Require Oversight and Fine Tuning to be Effective
Our Annual Review focuses on these 3 themes and show you how the top weaknesses NodeZero found and exploited over the past year led to critical impacts, deeper implications, and ultimately positive action by the customer to remediate vulnerabilities and weaknesses. Additionally, the 3 themes presented align with CISA’s Top 15 Routinely Exploited Vulnerabilities list and their Known Exploited Vulnerabilities List (KEVL) catalog. The list below highlights the top 10 vulnerabilities and weaknesses that NodeZero enumerated and exploited over the last year:
1) Credential Policies Are Weak, Or Often Not Enforced
Attackers don’t “hack” in, they log in. Regardless of what the headlines in our newsfeeds may say, cyber threat actors do not often use sophisticated hacking tools and techniques like zero-day exploits to gain access to a network; they simply log in with legitimate user credentials. Our customers are keenly aware of the risks that credential-based attacks pose to their organizations because NodeZero allows them to safely assess their environment against them.
In the last year, NodeZero successfully executed credential-based attacks over 2,000 times, and to great effect. Just as an actual Cyber Threat Actor (CTA) would do, NodeZero chains other weaknesses with the successful credential compromises to achieve multiple critical impacts. Attacks involving weak or reused credentials can have disastrous effects. While it is important for the customer to remediate chained weaknesses leading to these impacts in their environment, it is also important to rectify the underlying systemic issues that contribute to these issues: Poor authentication and/or credential policies, as well as poor enforcement of policies.
2) Patching Is Rare, Misconfiguration Fixes Are Even Rarer
Many exploitable vulnerabilities often have prescribed solutions already available. Over the last year, we have seen many of our customers run pentests only to find that their systems suffer from exploitable vulnerabilities that are several years old and have relatively easy fixes in the form of vendor-provided patches (provided as Fix Actions in NodeZero). This includes vulnerabilities from CISA’s Top 15 Routinely Exploited Vulnerabilities list and the KEVL catalog. Taken together, these lists provide a good starting point for cybersecurity professionals to understand what vulnerabilities are being actively exploited and what actions they need to prioritize to fix or mitigate the threat. Further, we have found that many customers have added software and hardware to their environments over time that is left with default settings enabled and/or improperly configured. In doing so, these environments become prime targets for nefarious CTAs that can string together weaknesses and vulnerabilities to achieve critical impacts.
When NodeZero exploits these vulnerabilities and misconfigurations as a threat actor would, it tells us a few things about an organization, their environment, and possible issues they may struggle with internally, such as:
- Trouble implementing patching policies
- Difficulty prioritizing what needs to be fixed
- Legacy systems that are not able to be patched to the latest version (financial or incompatibility issues)
- Some IT departments may have issues configuring new hardware when adding to the network
3) Security Tools Require Oversight and Fine Tuning to be Effective
A common complaint that we hear from our customers is that they are spending large sums of money on Endpoint Detection and Response (EDR) solutions only to see them fail at the first sign of trouble. Sometimes these companies are not able to detect an unauthorized host like NodeZero in their environment and prevent it from dumping a Security Account Manager (SAM) database full of credentials. This leads us to question if the company can:
- Detect nefarious actors
- Alert the cybersecurity professionals to them
- Stop the threat actor from acting
- Log what happened effectively
We often find that it is not necessarily the tool itself that failed, but rather it is a failure of configuring the tool properly. Of course, we only know that these tools are misconfigured, because our customers take the perspective of the attacker when running pentests with NodeZero. By running NodeZero, our customers can see what tactics and techniques (like NTLM relay or Kerberoasting), along with critical data such as timestamps, are used to find exploits and achieve critical impacts. From there, we can assess whether the customer’s security team did in fact detect, alert, stop and log the right actions.
For instance, a Man-In-The-Middle (MITM) attack is one of the most common cyber threat vectors that is plaguing web applications and servers. In pentests over the last year, NodeZero was able to use MITM attacks 2,605 times and captured 63,699 credentials. To defend against MITM attacks, it is recommended that organizations manage an Intrusion Detection System (IDS), require the use of Virtual Private Networks (VPNs) on all workstations, limit user access privileges, and, obviously, employ strong data encryption in all applications (not just public-facing apps).
Over the Horizon
We believe we should always be iterating, learning, and adapting as cybersecurity professionals to meet new threats, and our approach to building NodeZero is no different. In 2023, we remain committed to ensuring our customers and their environments continue to be our top priority as we consistently deliver critical attack content safely and quickly, keep users up-to-date on emerging threats, and delight our customer’s with an ever-evolving attacker’s perspective.