The digital transformation of healthcare, including adoption of Internet of Things (IoT) devices and leveraging cloud platforms for genomics, telemedicine, and machine learning, could lead to better treatments and improved outcomes for patients. It can also reduce costs for healthcare organizations by as much as $150 billion annually according to Accenture.
One of the hurdles organizations face in adopting new technology initiatives is healthcare security. Attacks on healthcare organizations are common. A 2020 study by the Healthcare Information and Management Systems Society (HIMSS) reported that 70 percent of the organizations had experienced “ significant security incidents” in the past year. A 2021 study found that 48% of US hospitals had either a forced or proactive shutdown their networks over a six month period due to ransomware attacks.
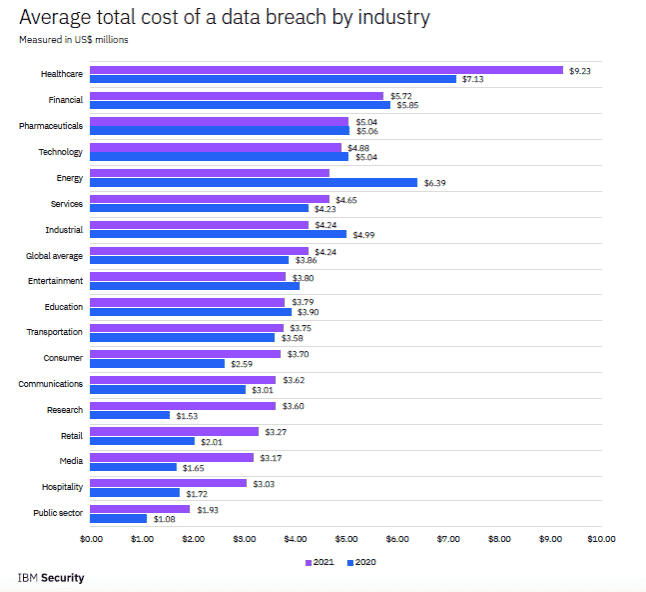
Why? Attackers value their data. This includes Personally Identifiable Information (PII) that can be used for identity theft and Personal Health Information (PHI) valued by criminals for insurance fraud. The latter can fetch up to $1,000 for a single patient’s full medical records on the dark web. Beyond reputational damage and regulatory penalties, data breaches at healthcare organizations are expensive. According to IBM’s 2021 Cost of a Data Breach Report, healthcare organizations have had the highest costs associated with breaches for 11 consecutive years, rising almost 30 percent from 2020 ($7.13 million per breach) to 2021 ($9.23 million).
Ransomware is leading to patient casualties
The consequences of a breach go far beyond monetary harm. Ransomware attacks on healthcare organizations can disrupt patient care. The 2017 WannaCry and Petya/NotPetya attacks in the UK forced over 80 National Health Service centers to shut down. Almost 20,000 patient appointments were cancelled, and five hospitals had to divert ambulance to other facilities. More recently, ransomware attacks on hospitals in Germany and Alabama contributed to patient deaths.
Defense is not easy
Defending against these attacks is not always simple, in spite of what cybersecurity product vendors tell you. Skilled attackers will chain together misconfigurations, unpatched software, and stolen credentials to elevate privileges and gain administrator access. Once this occurs, they can do anything they want, including adding new admin users, execute ransomware attacks, and steal sensitive data. Even when organizations are diligent in their patching (and the patch has been confirmed by their tooling) paths can remain open to attackers. Tools can lie…
What healthcare organizations can do
Under HIPAA, covered entities have two primary requirements: risk analysis and risk management. A risk analysis requires organizations to:
Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by the covered entity.
A thorough risk assessment includes a penetration test of your networks. A pentest will identify weaknesses, shadow IT, and attack vectors a criminal could exploit. Unfortunately, manual penetration testing can take weeks of time for preparation, execution, and analysis and tens of thousands of dollars. With ever tightening IT budgets, conducting regular network pentests is impractical for most healthcare organizations.
Opting for automated, “point and click” pentests falls far short of what is required for a thorough assessment. These offers, while affordable, rely on fixed scripts. They are not capable of the same tactics and techniques used by skilled adversaries and often result in inconsequential findings; “noise” and unproven results that defenders must research to determine if they require remediation.
NodeZero is a self-service, autonomous pentesting that provides the results of a skilled pentester at a fraction of the cost and can surface ransomware exposure that puts healthcare organizations at risk. Rather than wait for security resources to become available, IT teams can start an autonomous pentest with just a few clicks. It assesses systems as would a manual pentester, but faster, more completely, and with more actionable results. No credentials or agents are required and they are safe to run on production systems. The results are limited to exploitable weaknesses and include attack paths and “proofs” for each step, so IT teams know exactly how the attack was performed and precisely what to fix.
Autonomous pentests allow healthcare organizations to test as frequently as they like. It makes it practical to validate every software update to confirm proper the updates were successful.
Recently, Snehal Antani, CEO and co-founder of Horizon3.ai, joined Ravi Das, host of the AST Cybersecurity podcast to talk through the challenges healthcare organizations face when it comes to cybersecurity. Tune into his episode here.
Read more on how we help healthcare organizations.

