Hackers don’t break in, they log in. This has never been more true – as the demand for data increases, more files than ever are being stored across the enterprise. Local files, file shares, cloud backups, and more are filling up with precious data. And with that, comes increased risk that the data being stored contains sensitive information that attackers are keen to get their hands on.
The following real world examples from NodeZero users highlight the risks associated with storing sensitive data, and the need for a scalable way to analyze mass amounts of data for secrets.
Domain User to Domain Admin
During an internal pentest, NodeZero compromised a domain user via a password spraying attack. Domain users often have access to a wide range of SMB shares, where tight access controls are often lacking. Due to this data sprawl, the compromised user had access to an SMB share with a “web.config” file. Web.config files are often used in ASP.NET applications, and can contain plaintext credentials. Unfortunately, this application was configured to use domain admin credentials, compromising the entire environment. The full attack path is shown below:

Domain User to PCI/PII Data Compromise
Compromising an environment isn’t the only impact that can come from open file shares. Even more common are other types of sensitive files containing PII/PCI. In this internal pentest, NodeZero compromised a domain user via another password spraying attack. The compromised user did not have wide permissions leading to further compromise, yet its access was still enough to find hundreds of files, many of which contained PCI/PII data. This type of sensitive data is often the end goal for attackers, who can then sell or ransom the data. The full attack path is shown below:
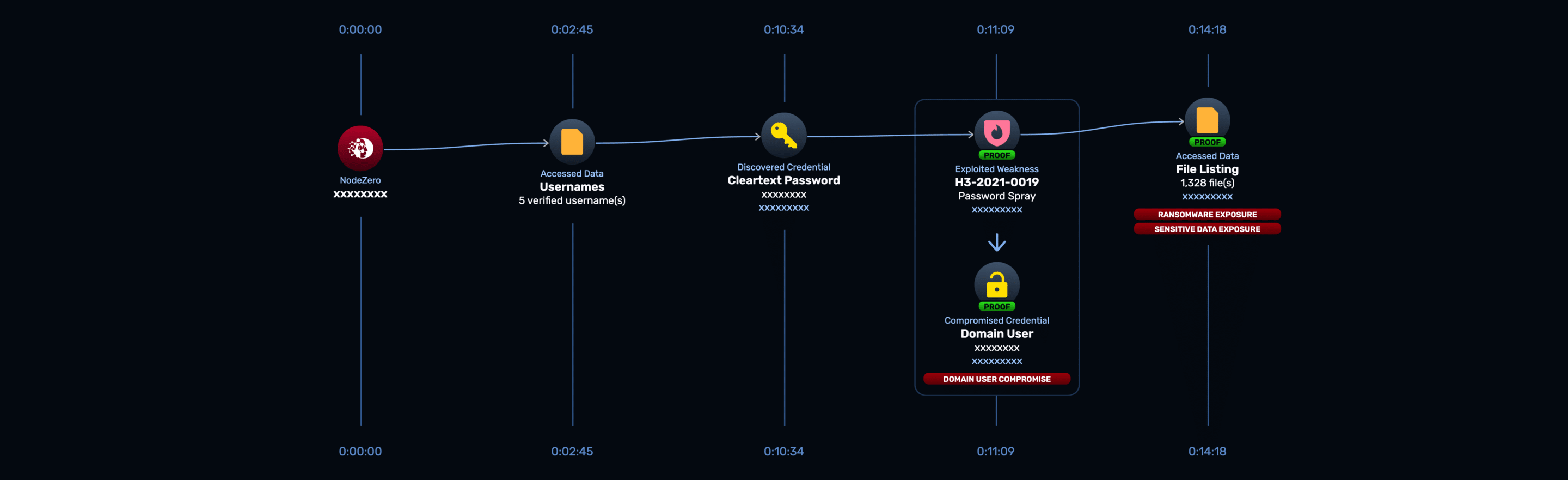
While trivial, this attack path demonstrates the pervasive issue of poor data segmentation, especially with regard to files repositories such as network shares and cloud syncing solutions.
Domain User to AWS Admin Compromise
What is worse than compromising an environment? Pivoting to a different environment and compromising that too, of course. During another internal pentest, NodeZero compromised a local machine using the EternalBlue exploit. Once on the machine, an unprivileged domain user account was compromised by dumping the credentials from LSA. Once again, the domain user had access to an SMB share that contained an application configuration file. The file contained access keys to an AWS account with administrative privileges. The full attack path is shown below:
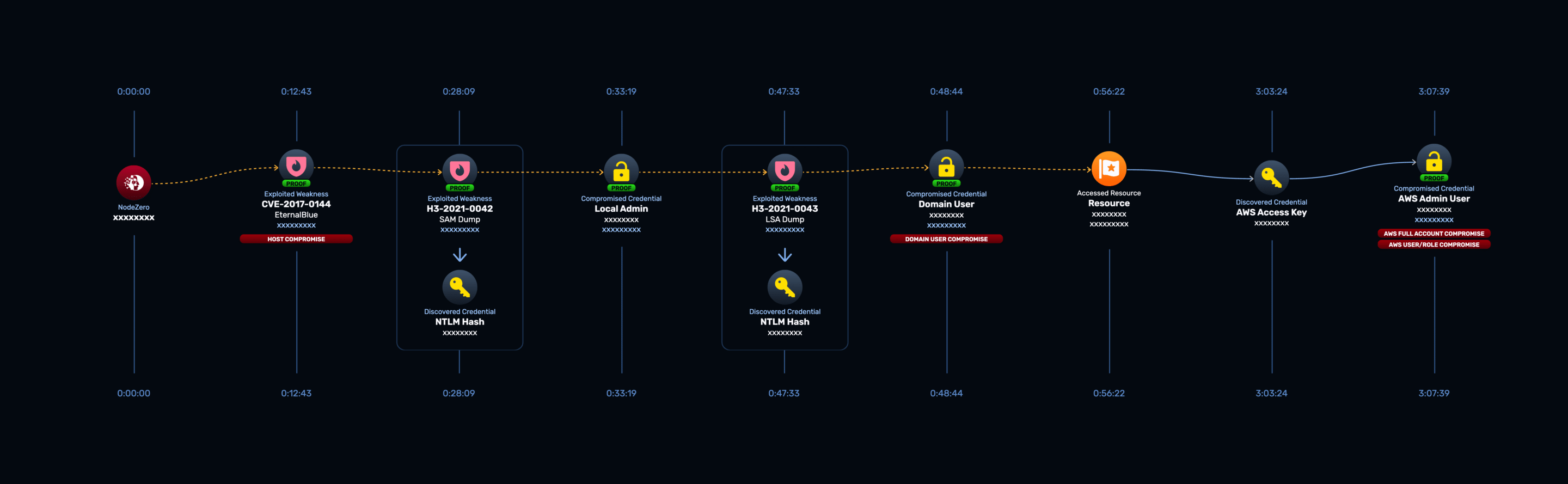
This is another example of a single vulnerability and a single file allowing NodeZero to pivot from an unprivileged user account to full cloud account compromise.
SMB Share to SQL Database Compromise
User passwords or access keys are not the only types of credential to be found through data pilfering. Even more sneaky are application credentials, when an application is configured without questioning where provided credentials will be stored. In this example, NodeZero first exploited the EternalBlue vulnerability to gain code execution on a domain computer and then obtained a domain user credential by dumping LSA on the compromised device. Next, NodeZero used the credential to identify a .NET application on an SMB share with a “.exe.config” configuration file that contained SQL database credentials, which allowed NodeZero to pilfer data from the database. The attack path is shown below:
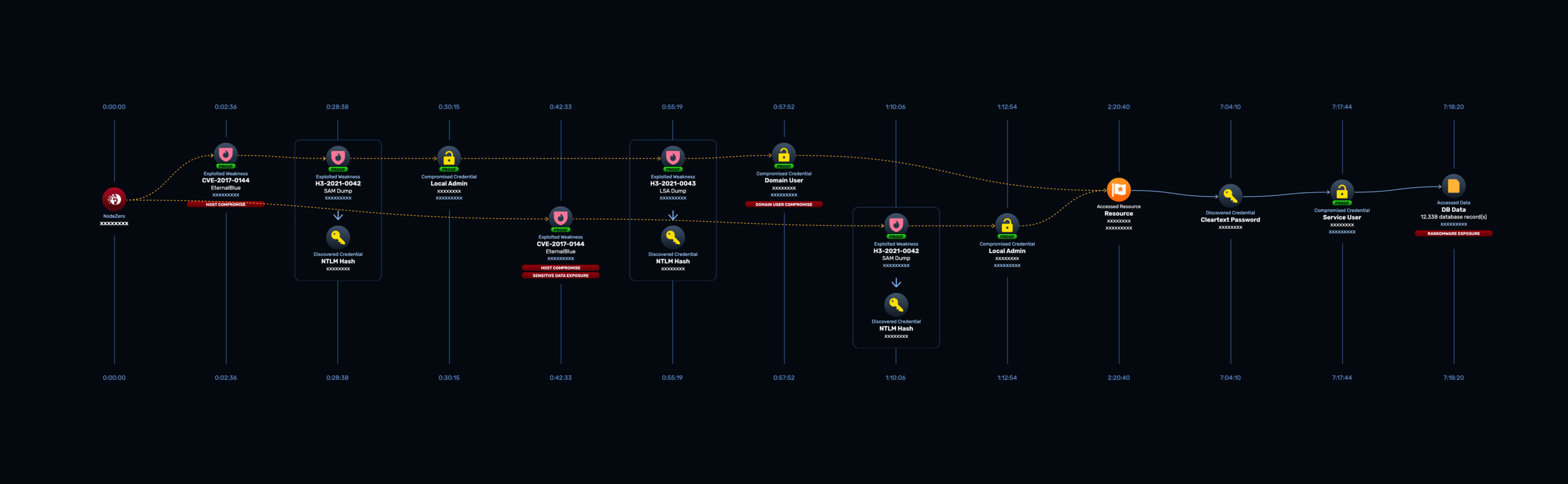
Without manually looking through an application’s file structure, identifying sensitive data can be a challenge. NodeZero’s scalable approach allows application data to be analyzed efficiently, allowing you to allocate your man hours elsewhere.
UAT User to Production User Compromise
NodeZero pilfering is not limited to local files and network shares. Any file repository that NodeZero gains access to will be analyzed. In this example, during an AWS pentest, NodeZero scoured S3 buckets and found an AWS access key in a JSON file for a user in the UAT environment. Using these credentials as the UAT user, NodeZero identified a new S3 bucket access, where another JSON file was found containing an AWS access key for the production environment user. The full attack path is shown below:
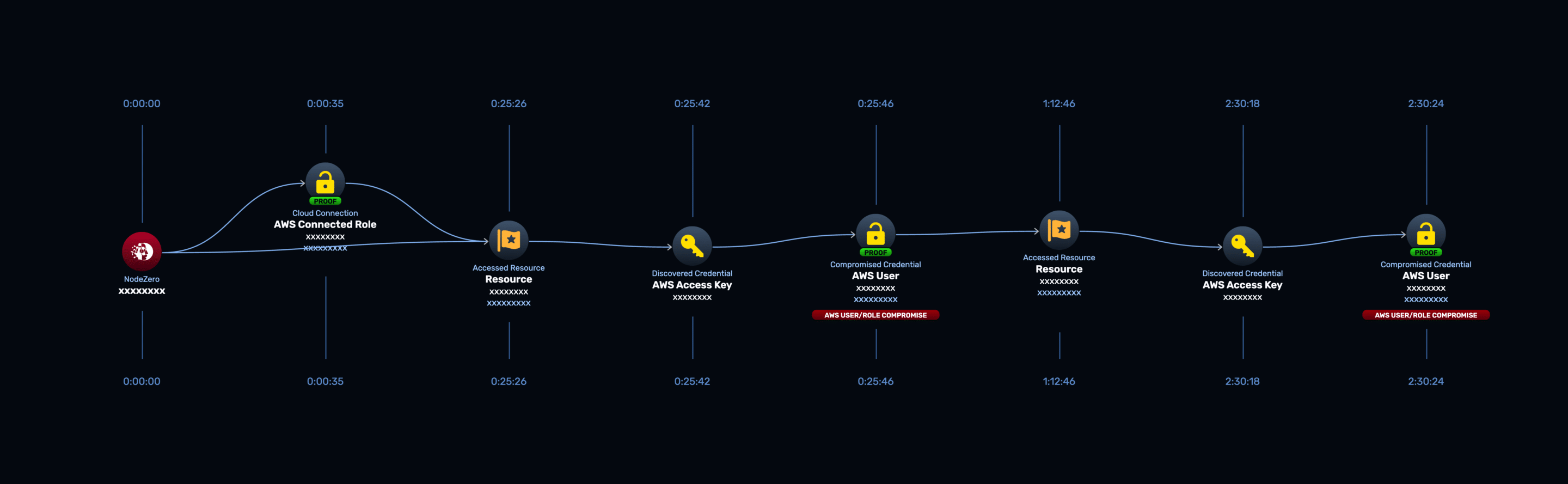
Takeaways
Files often contain credentials that break security boundaries and allow attackers to pivot from one environment to another. As organizations store more and more data, the amount of files containing sensitive information increases, while the overall ratio of sensitive files decreases, making these security holes both more common and harder to find, which increases the need for a scalable solution.
NodeZero is able to analyze files from any source for secrets on a scale only possible through extensive automation. Use NodeZero to identify sources of rogue credentials and improve your security posture!

