Rapid Response
with NodeZero
Get Ahead of Emerging Threats
CISA reports that while only 4% of all CVEs have ever been exploited in the wild, 50% of those are exploited by attackers within the first two days of disclosure.
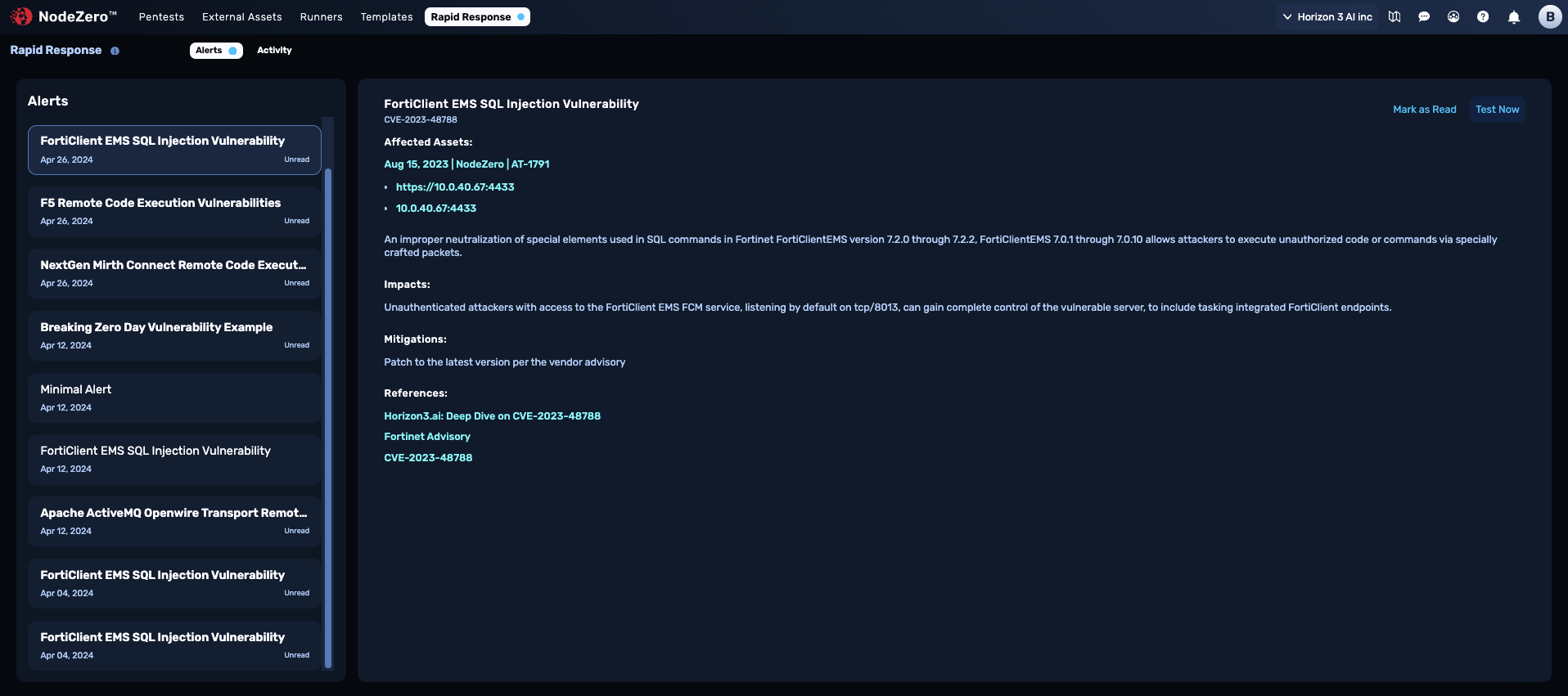
Your ability to swiftly identify and remediate the emerging threats that pose an actual risk to your organization is key to your cyber resilience. With the Horizon3.ai Rapid Response service— provided as a unique benefit to NodeZero users— you are alerted if your assets are known to be affected. Based on the impact priority, you can initiate action to the emerging threat directly from the NodeZero Rapid Response center.
Get Ahead of Adversaries
Begin finding, fixing, and verifying N-day vulnerabilities in your environment before they are widely exploited. If the Horizon3.ai team discovers a zero day, you will be notified PRIOR to public disclosure if your environment is impacted. Read the white paper for a full overview of the Rapid Response service.
Complete N-Day Testing in 24 Hours
You can shorten the critical timeframe for testing for N-day exposure even in large organizations by pre-configuring runners for each of your major network segments. Then when a widespread N-day emerges, you can run those preconfigured segments concurrently, so that your full environment is tested within 24 hours. The NodeZero platform scales to support the largest networks and can run 100+ N-day tests concurrently.
Rapid Response in Action:
NodeZero Users Notified 57 Days Before CVE Cataloged
Horizon3.ai’s Attack Team consists of former US nation-state hackers and OSCP practitioners, who use their experience and extensive cyber threat intelligence sources to deliver advance notice of emerging exploitable vulnerabilities affecting any assets organizations have previously tested on the NodeZero platform.
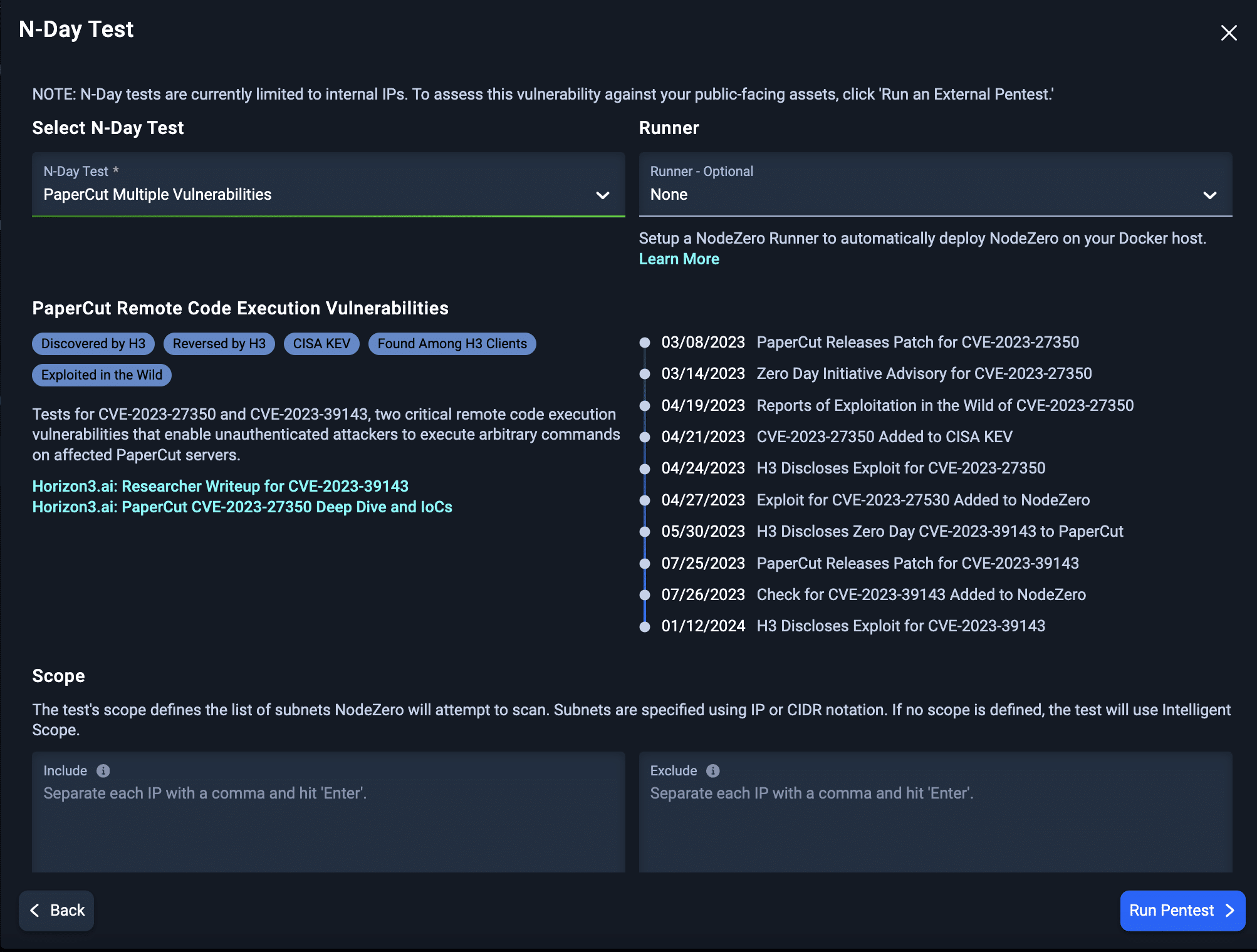
In the PaperCut example, NodeZero customers benefited from unique threat intelligence unavailable to anyone else in the world. Users were notified 26 days before a patch was publicly available and 57 days before a CVE for the zero day was officially issued and cataloged.
Horizon3.ai Discloses Zero Day to PaperCut
Zero Day Verified by Vendor
Rapid Response Program Notifies Affected Customers
Mitigation: Take assets offline ASAP
NodeZero users notified 26 days before a patch was available and 57 days before a CVE was cataloged.
PaperCut Releases Patch
Exploit Added to NodeZero
Zero Day Added to CVE Catalog
CVE-2023-39143
What are zero days?
A vulnerability or security flaw in software or systems that is unknown to the vendor or developer.
It is called “zero day” because the vendor has had zero days to fix or patch the unknown vulnerability. Zero day vulnerabilities are valuable to attackers because they can be used to launch targeted attacks without detection.
What are N-days?
An N-day is a software or hardware vulnerability that is already publicly known, (n days since disclosure) but there may or may not be a security update available to remediate the vulnerability.
The goal of vendors, distributors, and administrators is to have systems patched as quickly as possible to avoid N-day attacks.
Rapid Response in Action:
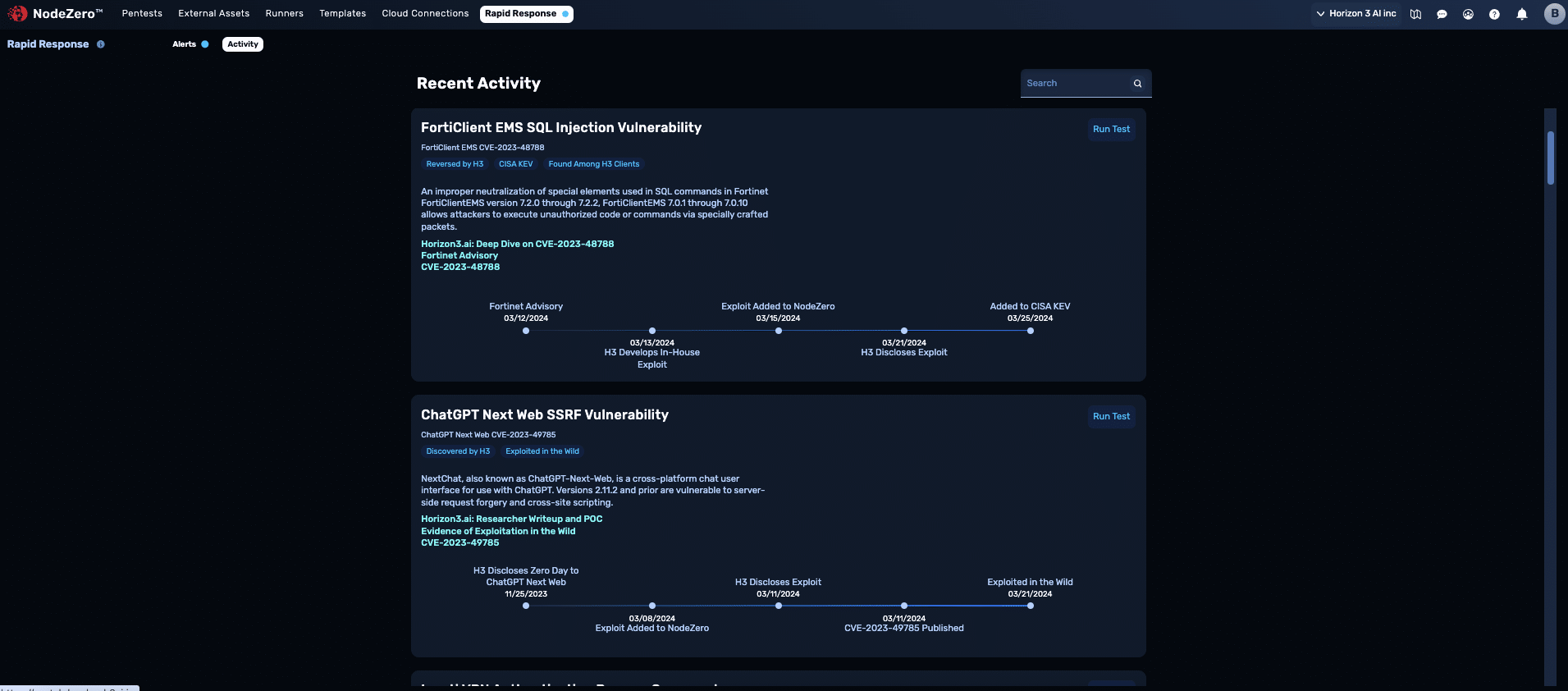
NodeZero Users Get Early Alert to FortiClient EMS N-Day
24 hours after Fortinet issued a critical advisory regarding a structured query language (SQL) vulnerability of FortiClient Enterprise Management Server (EMS), Horizon3.ai’s Attack Team was able to reverse-engineer it and get first blood on the proof-of-concept exploit for the vulnerability that allows for unauthenticated code execution.
Within the first 72 hours of Fortinet’s advisory, all NodeZero customers who were opted-in to Rapid Response were alerted of specific assets in their organizations that were manually verified as exploitable to this breaking N-day. They also received mitigation recommendations a full 10 days before the vulnerability was added to CISA’s Known Exploited Vulnerabilities (KEV) catalog.
Fortinet Announces Critical Advisory
Horizon3.ai Achieves First Blood on PoC Exploit
NodeZero users were notified if the vulnerability impacted them within 72 hours
Exploit Added to NodeZero, Rapid Response Program Notifies Exploitable Users
Mitigation: Patch ASAP
They received mitigation recommendations 10 days before the vulnerability was added to the KEV.
Horizon3.ai Discloses PoC Exploit w/ Technical Blog
Vulnerability Added to CISA KEV
CVE-2023-48788
Horizon3.ai helps you get ahead of emerging threats in these key ways:
Early identification of N-days and zero days:
Emerging Threats are Verified:
NodeZero users receive tailored threat intelligence on emerging vulnerabilities. This includes a manual verification by the Horizon3.ai Attack Team of the exploitability and impact of the threat in question, unique to your organization.
Prioritizes threats by impact:
When they identify vulnerabilities that are likely to be exploited, the Horizon3.ai Attack Team reverse-engineers them and creates a proof of concept exploit to understand the impact of the vulnerability. This understanding is embedded into NodeZero and is paired with contextual understanding of your environment to modify the ratings from the The National Vulnerability Database (NVD) when appropriate. This helps you prioritize your remediations and understand when you should patch outside of your regular cycle for a particular threat.
N-day testing is part of standard operating procedure:
N-day exploits are continually added to NodeZero
The Rapid Response center shows you exactly where your organization is vulnerable to new threats, what the outcome would be if a system was exploited, and how to best mitigate or remediate the N-day in question. Use the growing list of targeted tests to test the impact of a specific vulnerability on your environment.
Our Process Helps You Find, Fix and Verify Nascent Threats
Nascent threats identified
The Horizon3.ai Attack Team continually researches the global threat environment to identify new N-days that have been exploited in the wild or are likely to be exploited in the wild.
Users alerted
The Horizon3.ai team determines if NodeZero users are affected by the zero day or N-day. Users are alerted even before the new exploit is added to NodeZero.
N-Day Test Added to NodeZero
The Horizon3.ai Attack Team develops a new attack module for the zero day or N-day, using a production-safe variant of a proof of concept if one exists or developing one from scratch if it does not. A new N-day test for the vulnerability is added to NodeZero. Users can initiate an N-day test directly from the Rapid Response center to assess if any of their assets are exploitable.
New exploits are also run automatically as part of NodeZero's standard internal and external pentests.