A Pentest Wednesday® Story
You don’t usually think of your local library as a target for ransomware. But when every library branch across a major U.S. city suddenly went offline, one Public Library System learned that even the most trusted public institutions can become high-value targets.
In the aftermath of the ransomware outage, cybersecurity became a matter of public trust. Leadership committed to validating their defenses through real-world testing. They needed evidence that their improvements were making a measurable difference, and they found it with NodeZero®.
Impact
Over Memorial Day weekend 2024, a ransomware attack impacted digital infrastructure across 27 library branches. Nearly 27,000 people were affected, including patrons whose personal data may have been compromised.
Core services were disrupted:
- Public and staff computers
- Online catalog and loan systems
- E-books, audiobooks, and Wi-Fi access
Students and vulnerable populations relying on library technology and tutoring services were especially impacted.
Full recovery took approximately 90 days, with phased restoration of services. The IT team re-imaged around 1,000 computers and upgraded systems to contain the breach. Recovery costs exceeded $1 million, with additional legal expenses expected as investigations continued.
In the context of ransom-based attacks, the incident underscored the risk public institutions face in general, and prompted broader discussions about shoring up their digital resilience. Cybersecurity experts later praised the organization’s response and proactive steps to strengthen future defenses.
The attack didn’t just disrupt services. It revealed that the organization’s defenses were built for compliance, not resilience. The experience underscored the need for a proactive, real-world approach to security validation.
Background
After recovery, security leaders in the organization began searching for a platform that could safely emulate attacker behavior, uncover hidden risks across production systems, and demonstrate measurable progress to executives.
The security team first met Horizon3.ai at a Cybersecurity Summit in March, where they immediately felt supported in their mission to validate and strengthen defenses. The collaboration began with a short proof of value, which quickly demonstrated NodeZero’s ability to emulate real-world attacker behavior and deliver actionable, audit-ready results.
“A key reason for choosing Horizon3.ai was the quality of its reporting, which breaks down data into bite-sized and easy-to-read formats. This makes it easier to get buy-in from leadership and communicate with teams responsible for remediation.” — Cybersecurity Analyst, City Public Library System
Mitigation
To date, the organization has run 28 internal pentests using NodeZero across their critical infrastructure, patron-facing systems, and office resources. They have run an additional 7 external pentests as well. These operations revealed the true risk landscape across 1600+ assets.
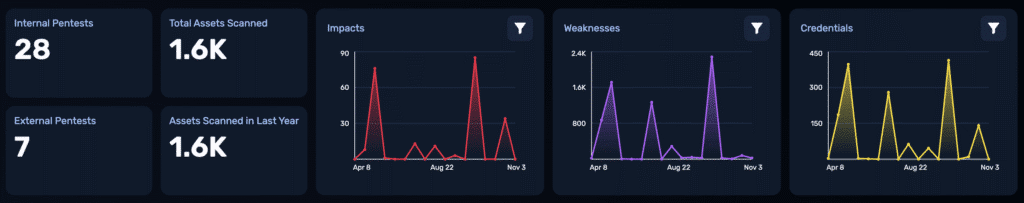
In a single baseline test, NodeZero uncovered 76 critical business impacts, over 1,200 weaknesses, and 361 compromised credentials.
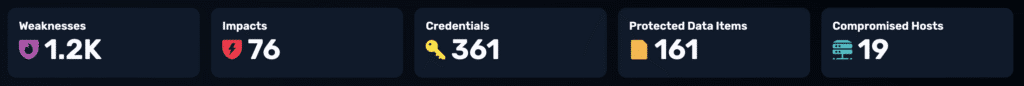
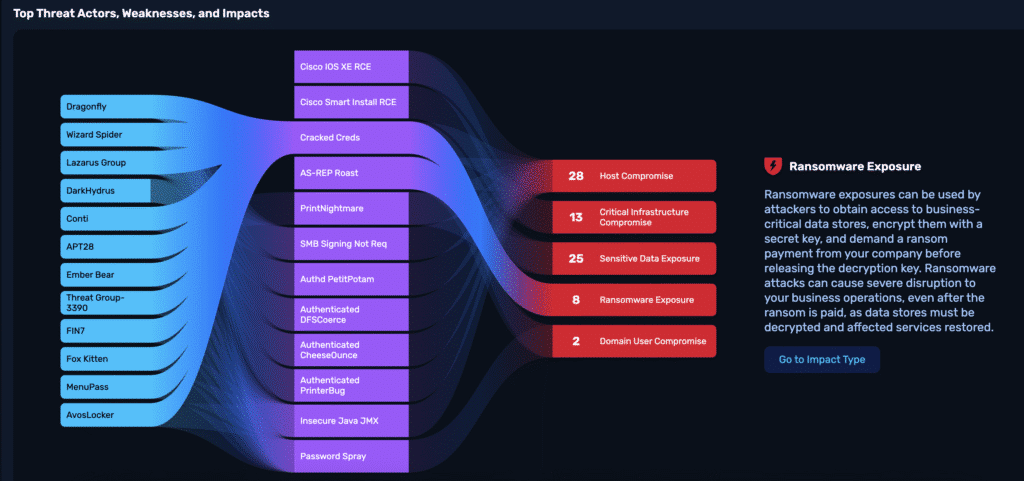
Most notably, it surfaced eight ransomware exposures, three critical and five high that had gone undetected by prior tools and assessments.
NodeZero also identified 76 attack paths with these impact types:
- Host Compromise (28 instances)
- Critical Infrastructure Compromise (13 instances)
- Sensitive Data Exposure (25 instances)
- Ransomware Exposure (8 instances)
- Domain User Compromise (2 instances)
NodeZero also mapped the 76 attack paths to the following weaknesses:
- Cracked Creds (40 instances)
- AS-REP Roast (40 instances)
- Cisco IOS XE RCE (4 overall instances, 2 different endpoints)
- PrintNightmare (2 instances)
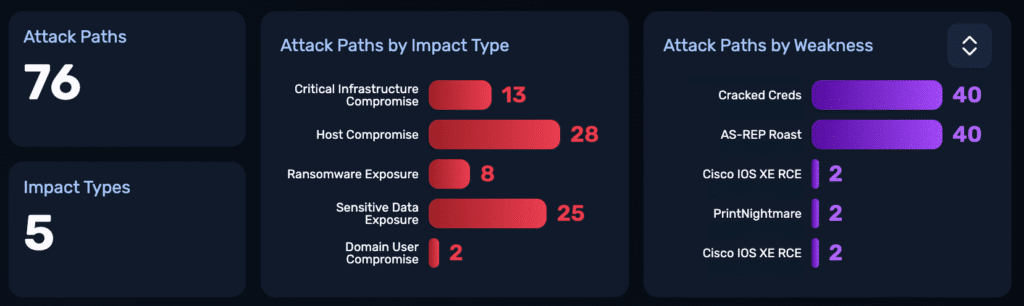
Their overall Exposure Level was High due to NodeZero exploiting critical weaknesses in the network, leading to:
- Host Compromise
- Critical Infrastructure Compromise
- Ransomware Exposure
NodeZero’s first full-network assessment mapped multiple CIDR blocks across all 27 branches and revealed the network was far flatter and more interconnected than expected – meaning a single compromise could more easily move laterally across branches. This discovery became a valuable outcome in itself, helping the team prioritize segmentation improvements and validate that security architecture is as critical as patching.
“It wasn’t about finding everything at once. It was about proving we were safer each time we tested. The find, fix, verify rhythm turned into a discipline.” — Cybersecurity Analyst, City Public Library System
Remediation
Armed with this visibility, the security team prioritized remediation based on NodeZero’s guidance. Critical weaknesses were addressed first, and follow-up 1CV tests (1-click verify) confirmed those issues were now mitigated.
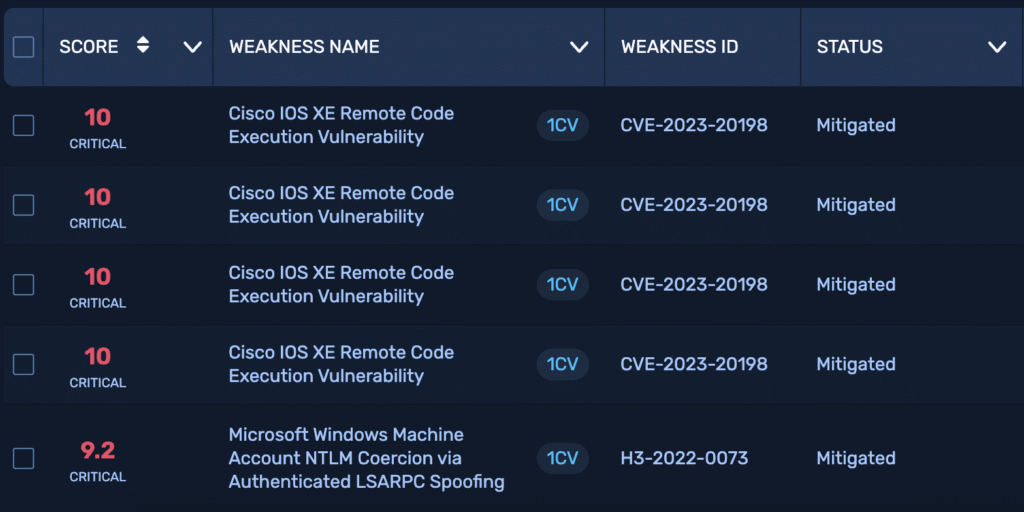
Subsequent branch-level tests verified segmentation improvements were becoming effective and revealed additional weaknesses introduced by configuration changes, reinforcing that remediation is never static.
The Find–Fix–Verify loop became central to their new “Pentest Wednesday” security discipline and testing rhythm. The organization saw improvements across three key areas:
- Cultural Shift: NodeZero’s clear, actionable reporting helped them move from a reactive to a proactive security posture, aligning IT, security, and executive leadership around real-world risk reduction.
- Risk Reduction: Established a hardened security baseline and demonstrated measurable progress to leadership over time.
- Proven Resilience: The continuous cycle of testing and remediation ensured that new vulnerabilities were quickly identified and addressed, preventing repeat incidents.
Measurable Results
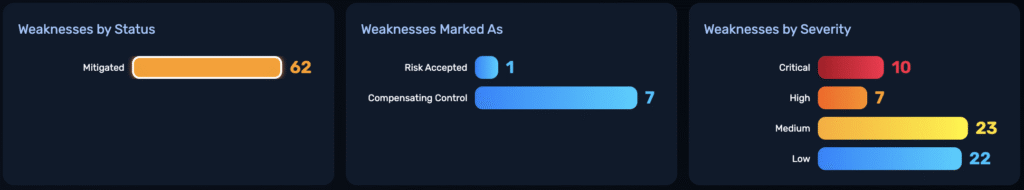
Within the first three months, the organization reduced critical weaknesses by 60%, eliminating 49 weaknesses (including 10 critical). These improvements were demonstrated with quantitative, audit-ready evidence for executive stakeholders.
“It’s incredibly rewarding to see customers experience real value so quickly. Watching them turn findings into measurable security improvements is exactly what NodeZero was built to enable.” — Ryan LeBlanc, Senior Customer Success Manager, Horizon3.ai
Real-World Impact Using NodeZero’s Advanced Data Pilfering (ADP) and High-Value Targeting Capabilities (HVT)
As part of their ongoing partnership, the team joined Horizon3.ai’s early adopter program to test new NodeZero capabilities: Advanced Data Pilfering (ADP), which identifies and validates sensitive, exploitable data, and High-Value Targeting (HVT), which automatically maps and tests access paths to critical users and systems.
The Public Library System’s security analyst ran multiple NodeZero pentests with the two new NodeZero capabilities enabled, including both blind and credential-injected scenarios. The features were quickly adopted into their internal pentesting workflows, with ADP and HVT defaulted “on” for all new tests.
- Immediate Value: In their first tests using these new capabilities, ADP successfully identified a credential that had been overlooked in prior assessments, directly validating the intended use of the feature.
- Strategic Use Case: They also saw a strong use case for ADP and HVT in assessing permissions and sensitive data on their on-premises file servers before migrating to OneDrive, especially for demonstrating risk to executive teams.
- Co-Development Partnership: The relationship has evolved into a strategic co-development phase, with real-world feedback directly fueling product development. The sentiment from both sides is one of deep collaboration and excitement, with the organization’s feedback shaping the evolution of NodeZero’s most advanced capabilities.
Conclusion
For a public institution that exists to serve its community, the ransomware attack was more than a technical challenge. It was a test of trust. Through Pentest Wednesday, the Public Library System shifted from reacting to verifying, improving their security posture with every test. Today they have proof that their systems, and their mission, stand stronger than before.
That is Pentest Wednesday in action: moving from reaction to verification, from recovery to resilience.


